Network-as-a-service (NaaS) has become a significant component of the networking market.
NaaS represents a paradigm shift in enterprise networking, transitioning from capital-intensive infrastructure ownership to flexible, subscription-based models. Analyst estimates project the NaaS market to grow at a healthy 26.7% compound annual growth rate (CAGR), hitting $115.5B by 2032.
The architectural shift for networking that NaaS introduces also requires a rethinking of security strategy as well. NaaS security strategy development requires a fundamentally different approach than traditional network security planning. Unlike conventional infrastructure where security controls are implemented at known boundaries, NaaS demands dynamic, software-defined security architectures that can adapt to distributed, multi-tenant environments.
NaaS security architecture fundamentals
Moving to NaaS shouldn’t be a lift-and-shift exercise, where the same setup used on-premises now becomes the same deployment in NaaS.
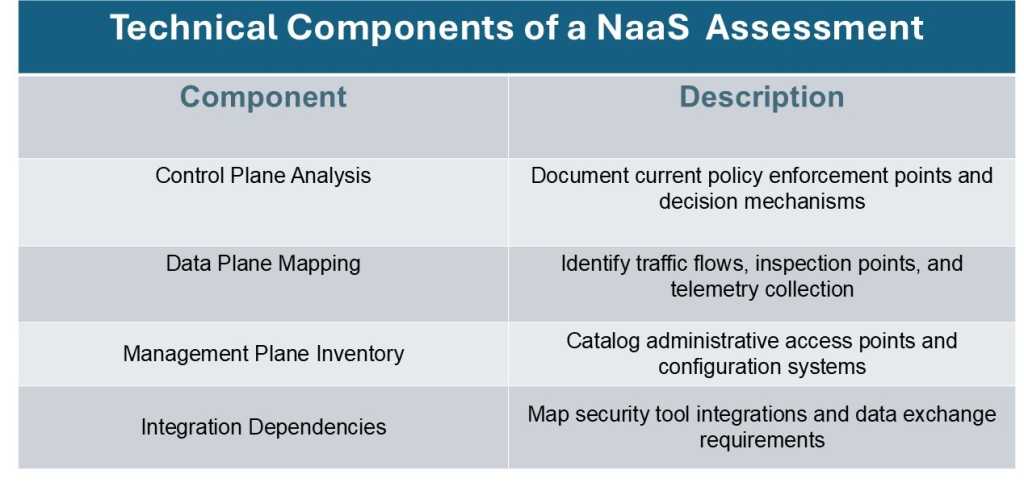
Before implementing NaaS security controls, organizations should conduct a comprehensive technical assessment of their current and target architectures.
“Organizations should take the opportunity to also evaluate their existing security policies and governance model and not look at it as only a technology change,” Marc Herren, director of network advisory at ISG, told Network World. “Shifting to an as-a-service model is an opportunity to clean up policies and remove technical debt associated with traditional network security controls. “
This assessment should map existing security control points, data flows, and enforcement mechanisms to identify gaps that will emerge in the NaaS environment.
Besfore you implement NaaS security controls, it’s important that you conduct a detailed technical assessment of your current and target architectures.
IDG
What is a shared-responsibility architecture?
NaaS operates on a shared responsibility model that differs from traditional network ownership. Organizations must navigate new security boundaries where providers control network edges and infrastructure while customers remain responsible for securing their data, applications, and access controls within the service.
The following chart details the core architectural differences for security across traditional and NaaS environments.
Comparing the core architectural differences for security across traditional and NaaS environments.
IDG
Technical Security Challenges in NaaS
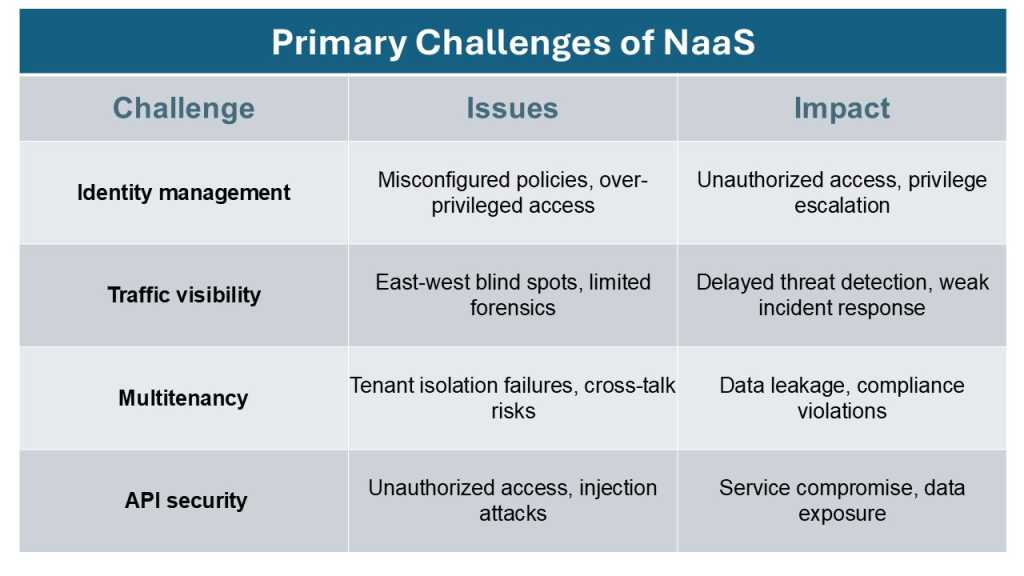
There are numerous technical security challenges with NaaS that network and IT administrators need to deal with.
“Organizations often underestimate the complexity of securing distributed, cloud-native network layers, leading to blind spots and over-privileged access paths,” Nigel Gibbons, director and senior advisor at NCC Group, told Network World.
According to Gibbons, the most common issues are: misconfigured identity policies, lack of east-west traffic visibility, weak tenant isolation, unpatched virtual network functions and mixing OT and IT inappropriately in shared network segments.
Jeremy Nelson, CISO at solution integrator Insight Enterprise explained to Network World that his organization often runs into a few recurring technical issues with NaaS.
“Unplanned downtime is a big one, usually stemming from hardware failures, software bugs, or network configuration errors,” Nelson said. “Security vulnerabilities are another major concern, often due to outdated equipment, poor configurations, and lack of proper monitoring.”
John Isch, practice director for infrastructure solutions at Orange Business, emphasizes the complexity of identity management in particular for NaaS as being a core challenge.
“Identity management presents unique challenges in NaaS environments, as traditional network perimeters disappear and enforcing least privilege becomes more complex across distributed services,” Isch told Network World.
Building a technical security strategy for NaaS
The process of building out a technical security strategy for NaaS shouldn’t be an ad hoc approach, it should be a well-reasoned plan. The most successful strategies combine comprehensive assessment with phased implementation.
“Making the shift from traditional network security to NaaS requires a solid plan,” Nelson said. “Start by assessing your current network setup to pinpoint any challenges and figure out what is needed.”
John Isch advocates starting with foundational assessment. He says the best place to start is with a comprehensive risk assessment to identify vulnerabilities and compliance needs. This assessment should feed into a roadmap containing the criteria for success, clear security policies, milestones that should be hit and defined roles to ensure the transition goes as smoothly as possible.
Security standards and microsegmentation
A key part of a technical security strategy for NaaS is the integration and implementation of security controls.
Implementing effective security controls in NaaS environments requires specific technical approaches that experts have validated across numerous deployments. The focus must be on authentication mechanisms, segmentation strategies and monitoring capabilities.
NaaS implementations should support a wide range of authentication protocols, according to Nigel Gibbons. That includes security assertion markup language (SAML), OpenID Connect (OIDC), Open Authorization (OAuth) 2.0 and certificate-based authentication. FIDO 2/Passkeys and System for Cross-domain identity management (SCIM) further enhance phishing resistance and lifecycle automation.
“Identity should be enforced at every access layer, replacing static credentials with context-aware, token-based mechanisms,” Gibbons said.
There is also a need for the implementation of microsegmentation as a security control that can help to limit a potential attack surface .
“Identify and prioritize applications, data and users that need granular segmentation and understand the traffic patterns and requirements,” Herren recommends. “Ensure that comprehensive testing is done after implementation and the provider can roll back the changes if needed.”
Operational considerations for NaaS security strategy
The operational reality of NaaS security extends beyond initial implementation to ongoing management and optimization. Industry experts emphasize the importance of maintaining security effectiveness while adapting to dynamic environments.
Operational excellence best practices
• Phased migration: Implement progressive security validation during migration and conduct specialized threat modeling focused on NaaS-specific attack vectors.
• Continuous improvement: Ongoing training, regular reviews and updating of security strategies to adapt to the evolving threat landscape will ensure the NaaS security solution remains relevant.
• Provider coordination: Any transition needs to be coordinated with the selected NaaS provider to align security measures with capabilities.
It’s also important to understand and emphasize the critical nature of provider relationships.
“It’s crucial to understand your SLAs regarding vulnerability management and ensure the NaaS provider offers constant monitoring and timely resolution of network-based vulnerabilities,” Nelson said. “Additionally, organizations must clearly outline their zero-trust requirements and ensure the provider can meet these needs with a full suite of security services.”
When evaluating NaaS providers for security, Nelson suggests that organizations check to make sure the provider is aligned with the NIST Cybersecurity Framework, which covers essential functions like identify, protect, detect, respond, and recover.
“Look at their risk management strategies, incident response capabilities, and continuous monitoring processes,” Nelson said. “Lastly, make sure they’re compliant with industry standards like SOC 2, PCI DSS, HIPAA, ISO 27001 and GDPR.”
Successfully securing NaaS environments requires a fundamental transformation in security thinking and implementation. The journey demands comprehensive planning, robust technical controls and ongoing operational excellence. The shift from traditional network security to NaaS security is not merely a technology change but an opportunity to modernize security architectures.
Source:: Network World
