Today, we’re excited to expand our recent Unified Risk Posture announcement with more information on our latest integrations with CrowdStrike. We previously shared that our CrowdStrike Falcon Next-Gen SIEM integration allows for deeper analysis and further investigations by unifying first- and third-party data, native threat intelligence, AI, and workflow automation to allow your security teams to focus on work that matters.
This post explains how Falcon Next-Gen SIEM allows customers to identify and investigate risky user behavior and analyze data combined with other log sources to uncover hidden threats. By combining Cloudflare and CrowdStrike, organizations are better equipped to manage risk and decisively take action to stop cyberattacks.
By leveraging the combined capabilities of Cloudflare and CrowdStrike, organizations combine Cloudflare’s email security and zero trust logging capabilities with CrowdStrike’s dashboards and custom workflows to get better visibility into their environments and remediate potential threats. Happy Cog, a full-service digital agency, currently leverages the integration. Co-Founder and President Matthew Weinberg said: ‘The integration of Cloudflare’s robust Zero Trust capabilities with CrowdStrike Falcon Next-Gen SIEM enables organizations to gain a more comprehensive view of the threat landscape and take action to mitigate both internal and external risks posed by today’s security challenges.’
Cloudflare Email Security with Falcon Next-Gen SIEM
With Cloudflare Email Security’s configurable policies, organizations can now push indicators of compromise (IoC) alerts to Falcon Next-Gen SIEM, notifying analysts about suspicious activity, such as a user engaging with a phishing email. By proactively alerting analysts when suspicious activity is detected, Cloudflare and CrowdStrike can provide early detection of account compromises or insider threats.
Cloudflare Zero Trust Logs with Falcon Next-Gen SIEM
We are also integrating Cloudflare’s Zero Trust platform with Falcon Next-Gen SIEM. This allows our mutual customers to push Cloudflare Zero Trust logs from Cloudflare Access and Cloudflare Gateway to Falcon Next-Gen SIEM for better visualization, analysis, and remediation. This integration allows Cloudflare logs to be used to customize and enhance Falcon Next-Gen SIEM detections and trigger CrowdStrike workflows to automatically configure a response action. An example workflow: based on a new detection of a user’s access request being deemed fraudulent, or if a user is engaging with risky websites, the Falcon platform can trigger Cloudflare to move users to affected user groups and apply adaptive access control policies, such as access isolating or quarantining the user.
How To Get Started
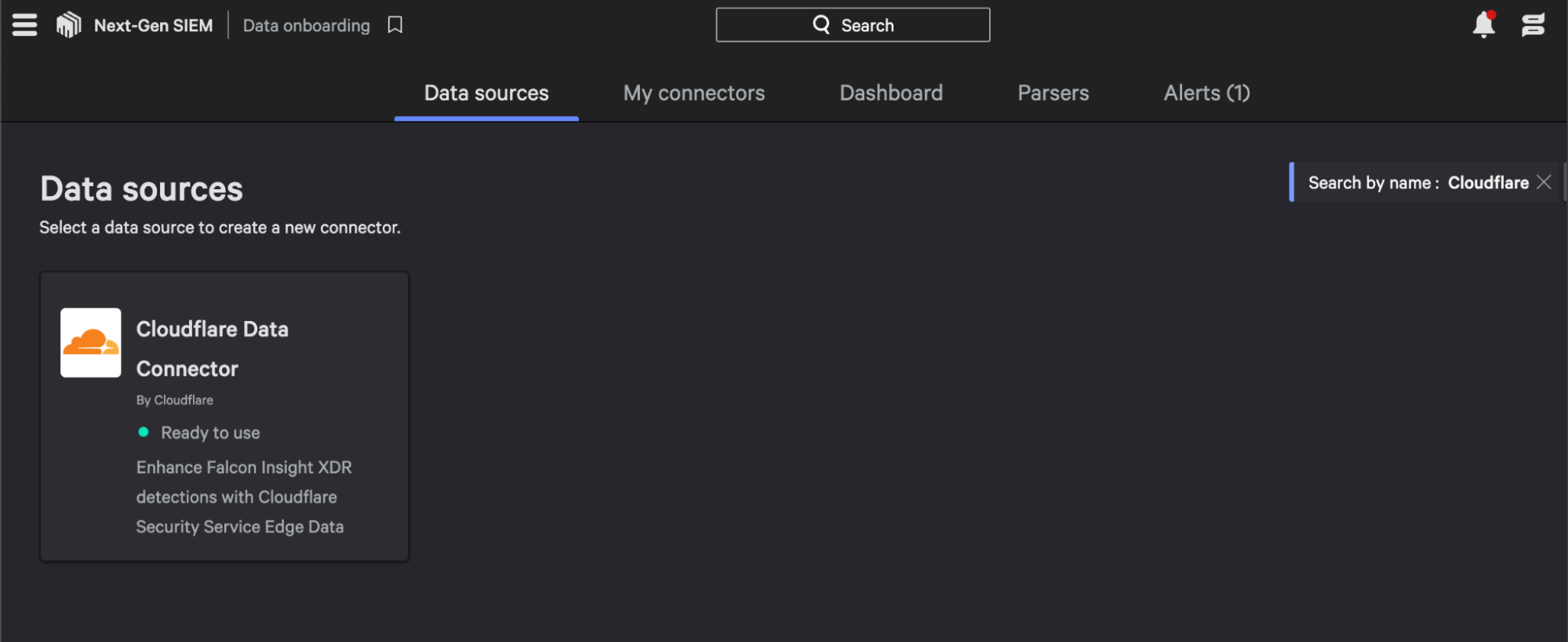
To connect Cloudflare Zero Trust logs, start with the Falcon Next-Gen SIEM module. Navigate to the Data Connectors tab of your Falcon Next-Gen SIEM dashboard and select the Cloudflare Data Connector.
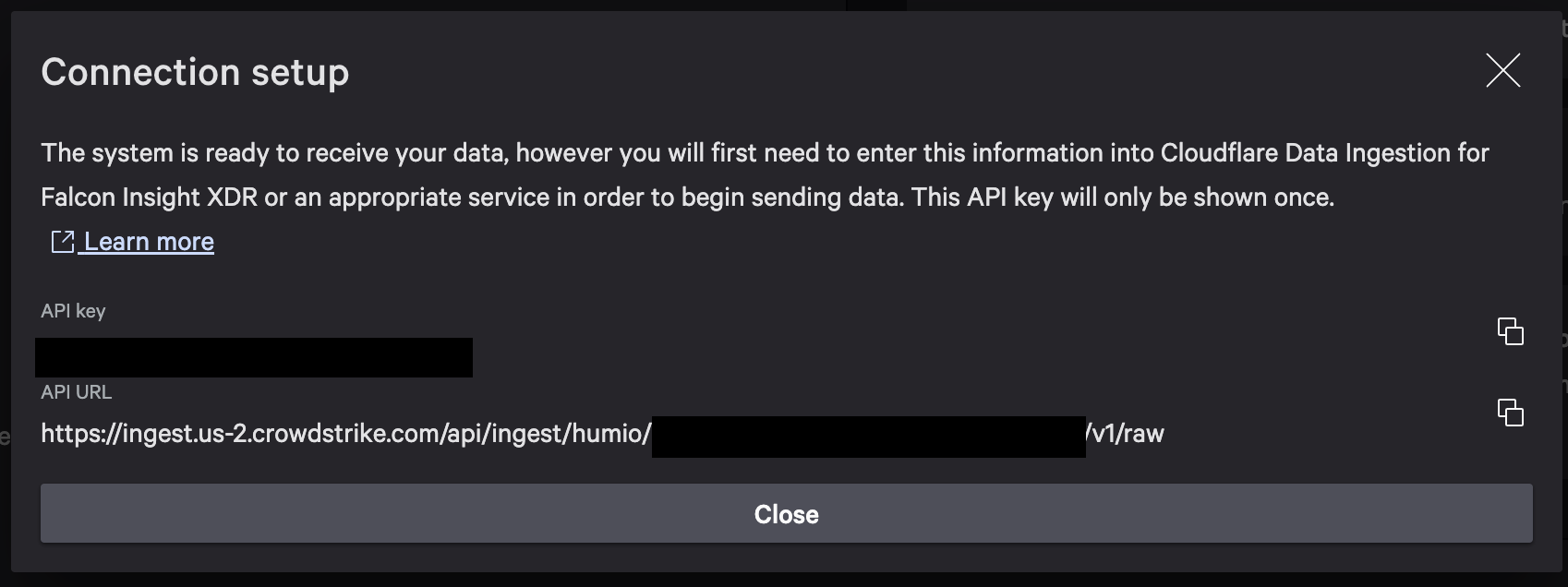
Give the connector a name and select “Save”, and you will receive two pieces of information: an API key and an API URL. Be sure to make note of the key, as it will only be shown once.
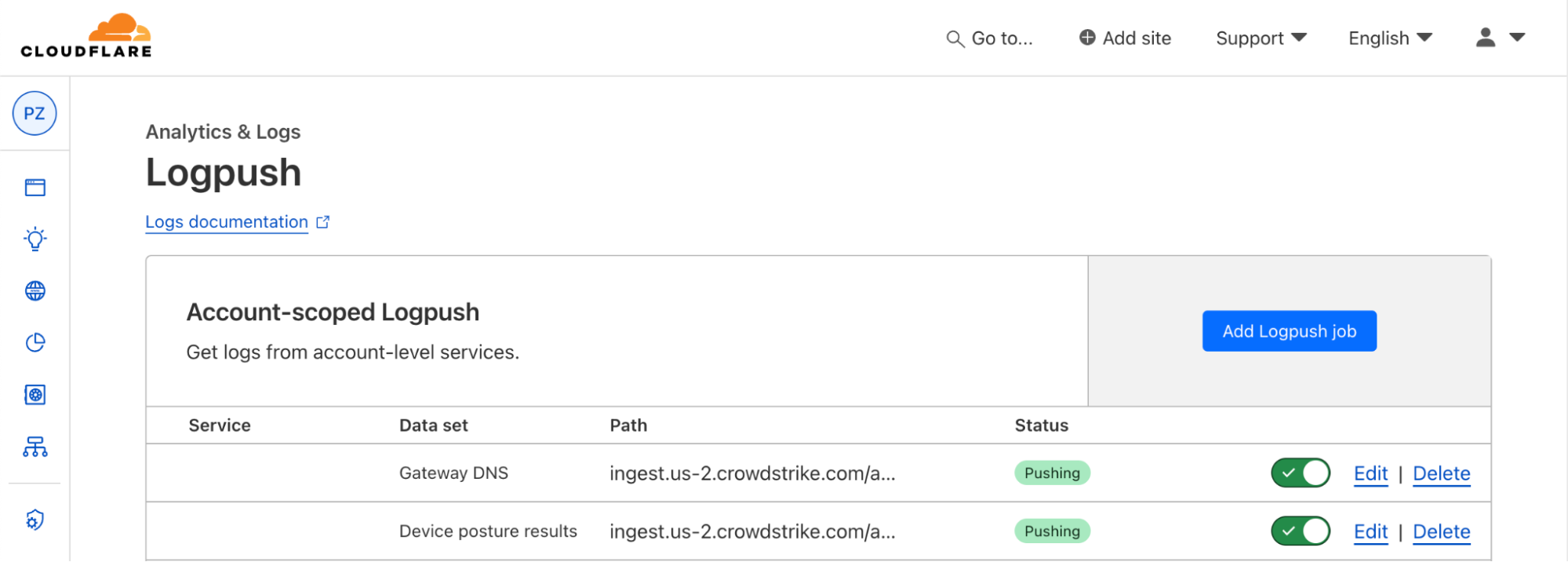
Next, in Cloudflare, create an HTTP logpush job via API, and format the “destination_conf” field as follows:
"destination_conf": "?header_Authorization=Bearer%20&tags=,dataset:"
Note:
is optional for account-level logpush jobs
follows a dot delimited syntax, so
http_requestsbecomeshttp.requests
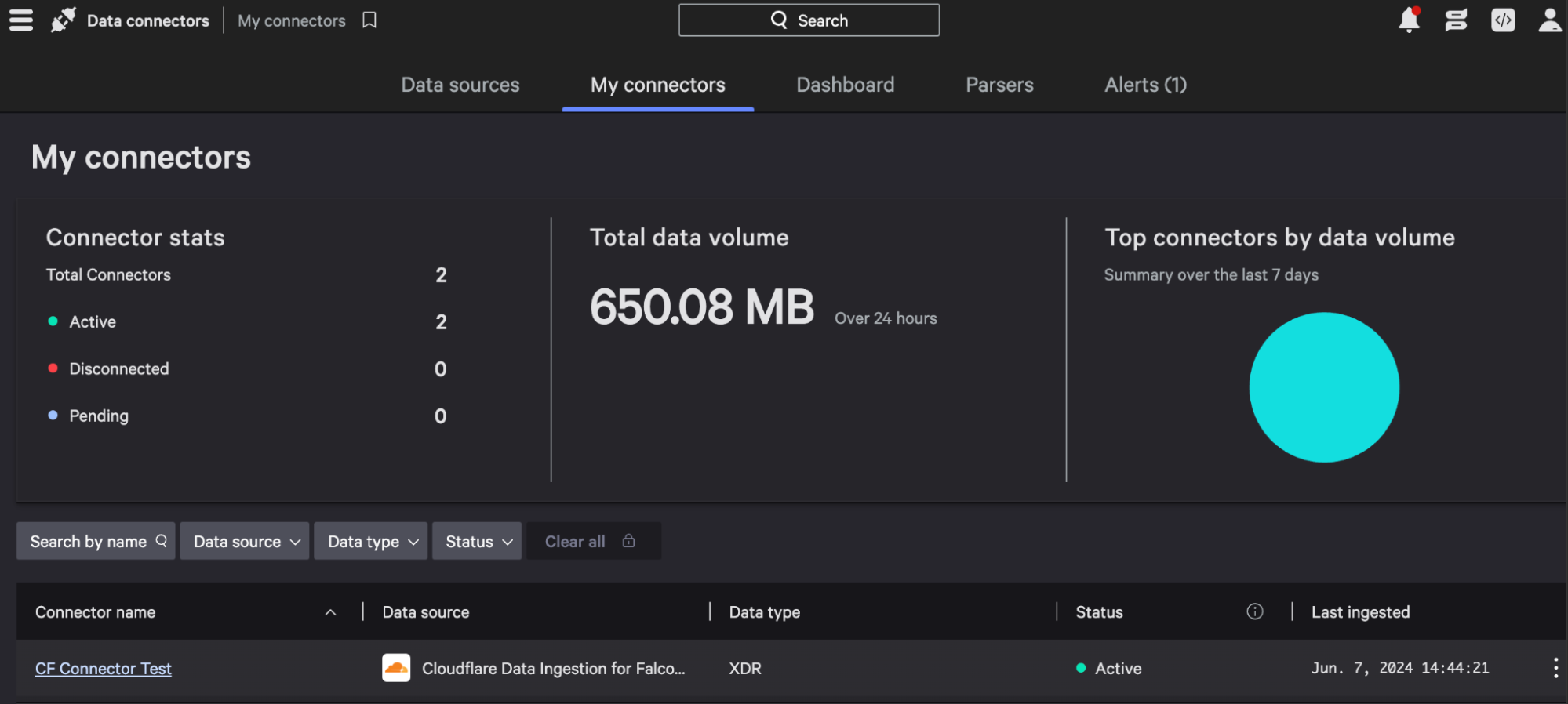
Once the job is created and active, you will start to see events populating in the My Connectors section of your Falcon dashboard. Once Cloudflare data is populated in Falcon Next-Gen SIEM, you can now search events and create Falcon Fusion SOAR automation workflows and correlation rules, all based on Cloudflare log events.
In Summary
Together, CrowdStrike and Cloudflare’s shared telemetry will further decrease the mean time to containment and expedite any organization’s ability to decisively respond to risks within their environment. The two platforms work together as one, allowing organizations to block suspicious activity and deliver high-fidelity alerts to security analysts for further investigation.
To learn more about these integrations, feel free to reach out to us to get started with a consultation. We can discuss your existing environment and ensure that you are best equipped to achieve better visibility and remediation in the face of emerging threats.
Source:: CloudFlare
