Intro
The e-commerce market continues to grow every year. According to FTI consulting, in Q1 2024, online retail comprised 57% of total sales in the US, and it is expected to increase by 9.8% over 2023 by the end of this year. In Europe, 72% of those aged 16–74 buy online, their share growing by the year. Globally, according to eMarketer, e-commerce sales are to reach $6.9 trillion by the end of 2024.
At Kaspersky, we closely monitor the evolving landscape of shopping-related cybersecurity threats. Each year, we track how cybercriminals target this rapidly expanding sector and the challenges they pose to consumers, especially during peak shopping seasons. As shoppers seek the best deals in the run-up to major sales events like Black Friday, cybercriminals and fraudsters gear up to exploit this demand, attempting to steal personal data, funds, and spread malware through deceptive shopping lures.
This report continues the series of annual analyses we’vewe published on Securelist in 2023, 2022 and 2021, which track the evolving landscape of shopping-related cybersecurity threats. In it, we present our findings on the dynamic nature of shopping threats, with a particular focus on the tactics used by cybercriminals during Black Friday, and offer insights into how consumers can stay safe in the face of the growing risks.
Methodology
To assess the current state of the shopping threat landscape, we conduct an annual analysis of various threat vectors. These include financial malware, phishing sites impersonating major global retailers, banks and payment systems, and spam emails that may lead to fraudulent websites or spread malware. This year, we also specifically analyzed the rise of fake mobile applications designed to steal shopping data. The threat data we rely on is sourced from Kaspersky Security Network (KSN), which processes anonymized cybersecurity data shared consensually by Kaspersky users. This report draws on data collected from January through October 2024.
Alongside this, with the help of Kaspersky Digital Footprint Intelligence, we explored what happens to all the stolen information, and specifically, how scammers offload it on dark web forums.
Key findings
- In the first ten months of 2024, Kaspersky identified more than 38 million phishing attacks targeting users of online stores, payment systems, and banks.
- As many as 44.41% of these attacks targeted banking service users.
- We detected 198,000 Black Friday-themed spam messages in the first two weeks of November.
- More than 13 million banking trojan-related attacks were detected in 2024.
- Despite the high number, the overall activity of PC banking trojans continues to decline.
- Credit card data is widely offered on the dark web, alongside shopping accounts.
- Dark web sellers offer Black Friday discounts, just like regular shops.
Shopping fraud and phishing
Phishing and scams are among the top threats for online shoppers. Fraudsters often create fake websites, emails or ads that closely resemble those of legitimate retailers. Given that shoppers are often busy or distracted, they may not take the time to carefully review links or emails, which makes them more vulnerable to these threats.
Kaspersky’s automated technologies are designed to detect and prevent various forms of financial phishing and scams that fraudsters run during the Black Friday season, including fake pages that mimic bank websites, payment systems such as PayPal, Visa or Mastercard, and online stores such as Amazon, eBay or AliExpress. These pages may target victims’ login credentials and payment information or trick users into transferring money to the scammers. Additionally, they may also steal other personal details from unsuspecting shoppers.
From January through October 2024, Kaspersky products successfully blocked more than 38,473,274 attempts to access phishing links targeting users of online shopping platforms, payment systems and banks. This represents a significant increase of 24.9% over the same period last year, when 30,803,840 phishing attacks were recorded.
If we break this down, 44.41% of these phishing attempts targeted users of banking services, 18.01% mimicked payment systems, and 37.5% attempted to impersonate e-shops. Notably, there has been a shift in the types of targets. While last year online store impersonation accounted for the largest share (43.47%), this year, attacks targeting banking users became prevalent, increasing slightly from 35.19%.
Financial phishing attacks by category, January–October 2024 (download)
Although the share of online store phishing and scams dropped insignificantly against 2023, the overall number of detected attempts to follow a phishing link grew slightly from roughly 13 million to 14,428,512. The top brands mimicked by the scammers remained the same as in the previous year, however, our analysis revealed that the overall number of phishing attacks per examined platform in 2024 appeared somewhat lower than in 2023. Given the growth in the number of all online store-themed phishing attempts, this may mean that the attacks have become more targeted and region-specific or that the number of platforms mimicked by the fake sites has increased.
TOP 5 popular online stores mimicked by the scammers, January–October 2024 (download)
In 2024, Kaspersky products detected and blocked 3,807,116 phishing attempts, primarily those distributing Amazon-related scam and phishing pages that were designed to steal personal and banking data from users, or trick them into buying non-existent goods.
Phishing attempts were also widespread across other major e-commerce platforms. In 2024, eBay was mimicked in 512,107 phishing attempts we blocked, while Walmart was used as a lure in 31,638, and MercadoLibre, the Latin American marketplace, in 214,834 cases. Phishing pages mimicking Alibaba Group stores were accessed 919,770 times.
Major scam campaigns preying on Black Friday 2024
Black Friday scams commonly spread through social media, search engine ads and, most frequently, mass email campaigns. Since many retailers rely on email to promote upcoming sales ahead of the holiday season, cybercriminals often exploit this by sending fraudulent messages with links to scam websites. Starting at the beginning of September, Kaspersky’s telemetry detected a week-by-week increase in spam emails containing the term “Black Friday”. As the shopping event approached, the volume of these emails surged, reaching a total of more than 198,428 spam messages just in the first two weeks of November.
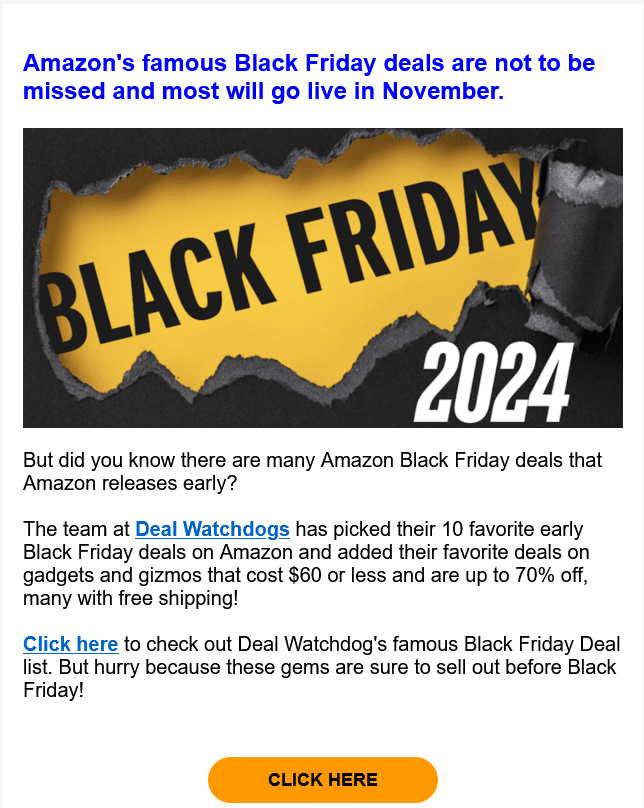
Scammers often impersonate major retailers like Amazon, Walmart or Etsy with deceptive emails to lure unsuspecting victims. These emails typically claim to come from the companies themselves and promote exclusive discounts, especially during high-traffic shopping periods like Black Friday. For example, one spam campaign circulating this year falsely claimed that Amazon’s “special buyers team” had handpicked top items not to miss, offering an exclusive sale of up to 70% off. Emails like this are designed to exploit the urgency and excitement of seasonal sales to trick consumers into clicking potentially dangerous links.
The email typically contains a link that redirects to a fake online store website, where unsuspecting victims may make fake purchases. Such pages are typically designed to look identical to the real ones, although sometimes they feature poor spelling or minor inconsistencies in domain names. However, if the victim tries to buy something on a site like that, they usually just lose money. Moreover, any data they entered on a fake website, such as their payment details, ends up in the hands of scammers. This can lead to various harmful outcomes, such as unauthorized purchases or further exploitation of the stolen data for fraudulent purposes.
Another common scam making the rounds this year capitalizes on consumers’ inclination to try their chances. Scammers know consumers are eager to win even minor prizes, so they craft messages that offer a limited-time survey with prize draws, the prizes being valuable goods, such as a free iPhone 14. To heighten the sense of urgency, these scams emphasize that the recipient is one of only a handful of “select” users eligible for the deal.
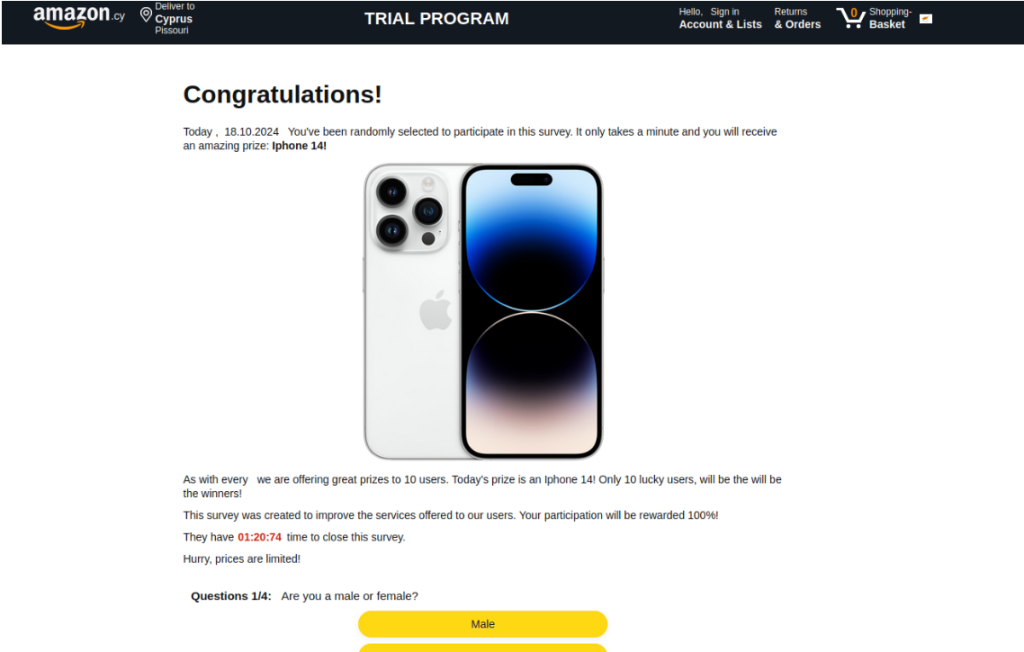
The catch is always the same: the recipient must act quickly, or they risk missing out on the “exclusive” offer. These tactics prey on consumers’ fear of losing out, tricking them into acting impulsively. In reality, there is no deal — just a carefully designed scam aimed at manipulating victims into making small payments to the scammers, thus losing money and giving away their payment details.
A similar scheme goes for gift cards. Scammers offer a “reward” for sharing some “basic info”, such as an email address, and spending some money on a fake site.
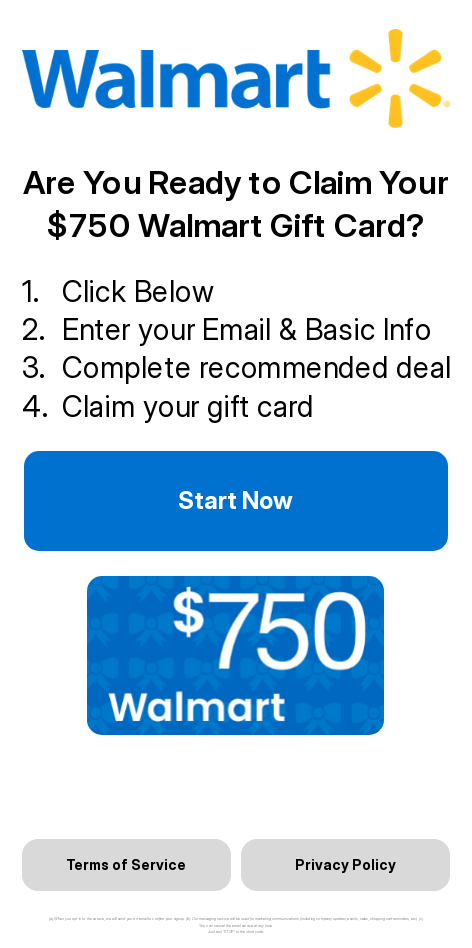
It is not only buyers that are targeted by Black Friday scams — sellers are also at risk. For example, we have seen a fake Etsy verification scam targeting individuals registered as sellers on the platform — the scammers must have obtained a copy of the seller database. The victim receives an email claiming that their account has been temporarily locked. The message urges them to click a link to unlock it. On a fake site, they are asked to enter their bank card details, including the card number, expiration date, CVV and billing address, supposedly for identity verification. The scam page may faithfully reproduce the design of the Etsy website, with only a few minor differences in the URL or visuals. Once the victim provides the card details, the scammers can steal their financial information or use it for fraudulent transactions.
While in the West, these scams are widespread before and during Black Friday, in the APAC region, scammers often capitalize on 11.11 (Singles’ Day), taking advantage of the unique shopping culture and timing. We’ve observed phishing campaigns targeting users across the entire Asia-Pacific, with fake online store pages appearing much earlier than expected. These pages, in languages like Vietnamese and Japanese, are distributed well in advance of 11.11, highlighting how scammers are tailoring their tactics to the region’s shopping habits. For example, the page on the screenshot below was detected in September 2024. This early targeting reflects a deeper understanding of the APAC market, with scammers taking advantage of the heightened consumer activity leading up to the event.
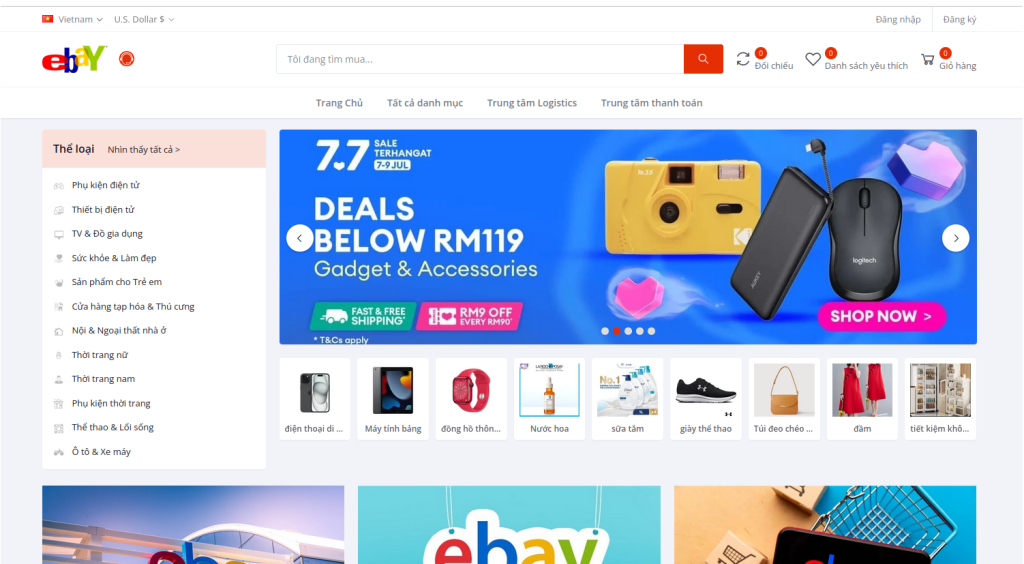
Fake app offers
This year, we have also discovered some malicious campaigns targeting users by spreading fake mobile shopping apps. Designed to imitate official retailer apps, they seem to offer lucrative deals but ask for payment upfront or collect personal data, such as credit card numbers or login credentials. Our security solutions blocked more than 8000 attacks during this campaign, which might potentially be targeting a broad spectrum of users worldwide.
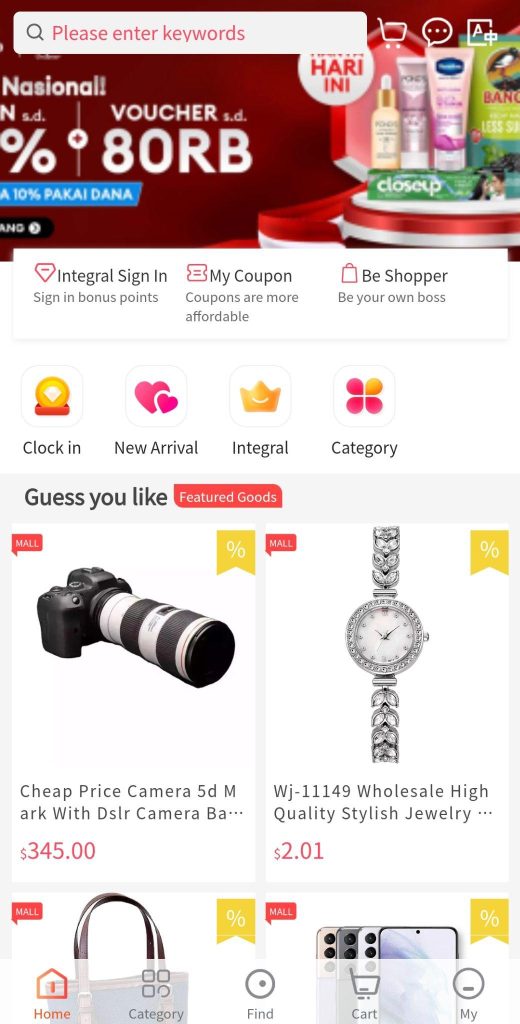
Fake closely resembling an official online store app
Banking trojans
In addition to phishing, banking trojans, or “bankers”, are a key tool for cybercriminals looking to exploit busy shopping seasons like Black Friday. These malicious programs are designed to steal sensitive data from online banking and payment systems. In this section, we analyze the activity of PC banking trojans, which, having sneaked onto the victim device, typically start monitoring their browser. Once the user opens a banking website the malware is interested in, it may use tactics such as web injection and form-grabbing to capture login credentials, credit card details and other personal information entered on the website. Some banking trojans can also monitor the victim’s clipboard in search of crypto wallet addresses. Once an address is detected, the malware substitutes it with a malicious one.
As online shopping surges during major sales events like Black Friday, cybercriminals target e-commerce sites and online marketplaces in addition to banks. Banking trojans can inject fake forms into legitimate sites, tricking users into entering sensitive data when making purchases or checking out. This increases the risk of identity theft, financial fraud and data theft, making consumers particularly vulnerable during peak shopping seasons.
Interestingly, this year, we’ve seen a continued decline in the number of PC banking trojan attacks following a sharp rise in 2022, when we observed a 92% year-over-year increase. This year, the number of attacks has dropped to 13,313,155, down from 18 million last year and representing a 46% decrease in just two years. This trend suggests a shift in cybercriminal tactics, which may be explained by the users increasingly switching to mobile banking. However, the threat of PC banking trojans remains significant, as illustrated by such families as Grandoreiro, which, in spite of the recent group member arrests, is ramping up its operations and targeting more than 1700 banks all over the globe. This underscores the necessity for users to stay vigilant, especially during high-traffic shopping events.
Overall number of banking Trojan attacks, January–October 2021–2024 (download)
Stolen shopping data on dark web forums
What do scammers do with all the stolen data? After a phishing attack, scammers who steal shopping accounts or credit card data may use it for their own profit or sell it on dark web forums or marketplaces. These platforms operate in a highly anonymous environment, allowing cybercriminals to benefit from stolen personal and financial information without revealing their identities.
The stolen data is often sold in bulk, with scammers arranging it into bundles. These bundles may include usernames, passwords, credit card details, shipping addresses and sometimes even security question answers. The more valuable the data, the higher the price. For example, full sets of stolen credit card details, known as “fullz”, often include not only the credit card number, expiration date and CVV code, but also the cardholder’s name, billing address and phone number. This makes them particularly valuable for fraudulent transactions.
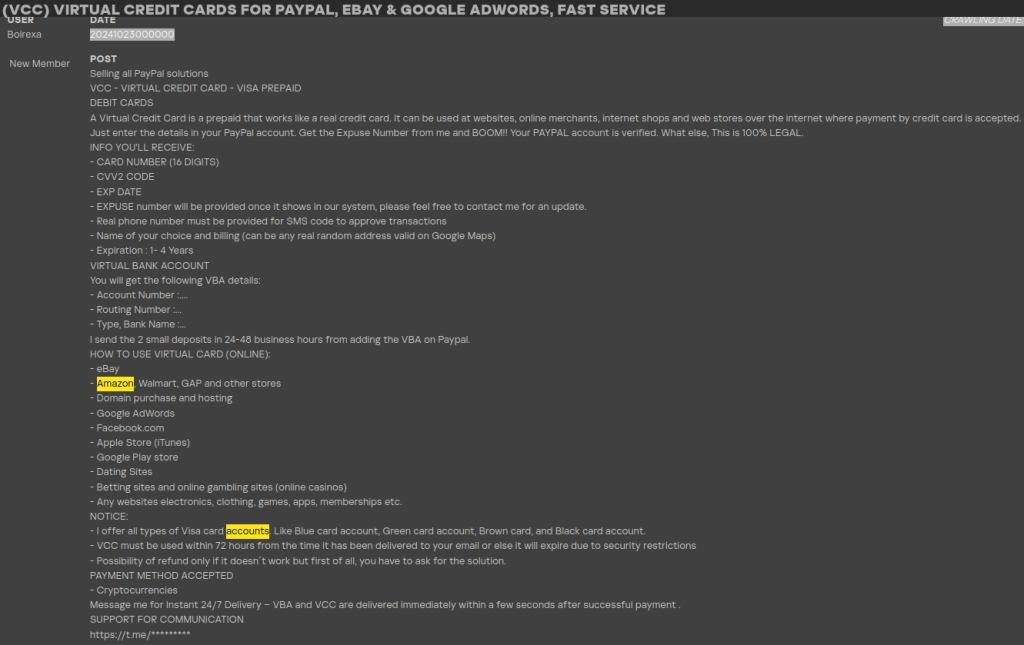
An example of a dark web ad selling user shopping data, retrieved with Kaspersky Digital Footprint Intelligence
Similarly, stolen shopping account credentials for popular platforms like Amazon, eBay or Walmart are highly sought after, as these accounts often contain saved payment methods, shipping addresses and other sensitive information that can be exploited by the buyer. Whoever acquires this data can monetize it by buying goods with the victim’s credit card, use it for money laundering and other malicious purposes.
Interestingly, darknet markets often mirror the pricing strategies and marketing techniques of legitimate online stores. Some sellers even offer special Black Friday promotions, such as discounts or bundled deals, much like what you’d see during seasonal sales in common online stores. For instance, one seller we observed offered a 10% discount on stolen card details from various countries: Canada, Australia, Italy and Spain. The sets were priced between $70 and $315 per card depending on its quality and the region it was from. This competitive pricing strategy reflects the demand and supply dynamics on the dark web, with sellers adjusting their offerings to attract buyers during specific periods much like any other retail market.
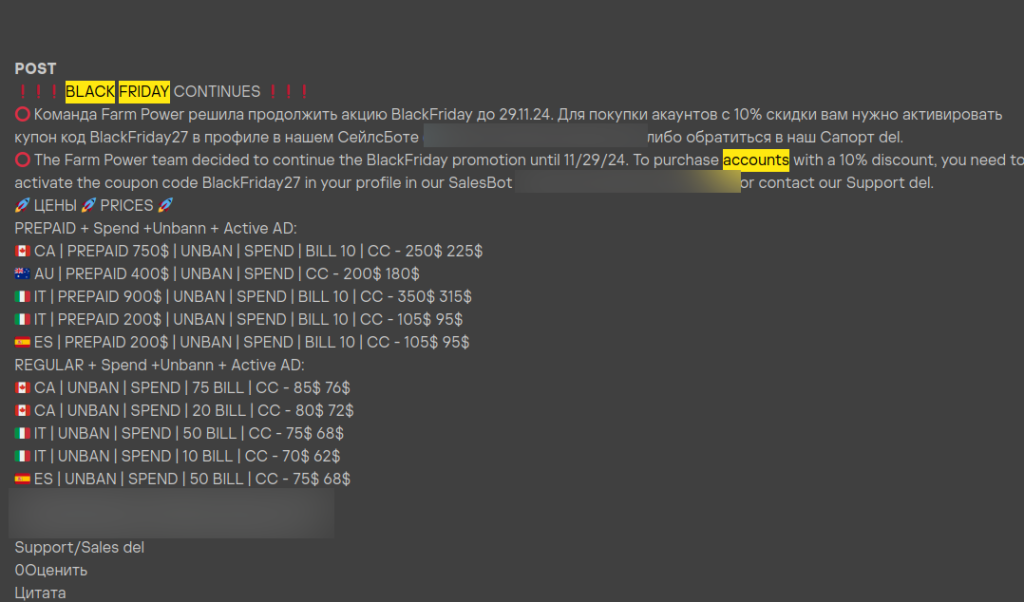
Black Friday sales on the dark web, retrieved with Kaspersky Digital Footprint Intelligence
Cybercriminals who deal with stolen credit cards — including those who sell, buy or cash them out — are known as carders. These may be individual fraudsters who use the data for their own profits or members of organized groups. Carders often buy credit cards in huge volumes to resell or capitalize on by buying high-ticket items, which they then resell or ship to drop addresses. In case of organized groups, the data may be also used for more complex schemes, like creating fake identities, opening new credit accounts or laundering money.
Conclusions
As Black Friday continues to be a major shopping event, it also remains a source of profit for cybercriminals looking to exploit consumers and businesses alike. Our analysis highlights a range of growing threats, from phishing attacks to the rise of fake mobile applications, all designed to steal money and sensitive shopping data. Scammers capitalize on the urgency and high traffic surrounding Black Friday sales, with phishing campaigns harder to spot among streams of other limited time offers.
Furthermore, the dark web continues to be a marketplace where stolen data can be swiftly sold, offering fraudsters easy access to compromised accounts, payment information and personal details. Beyond bank cards, cybercriminals target stolen credentials for popular shopping platforms like Amazon and eBay, granting them direct access to victims’ financial information and facilitating widespread fraud and identity theft.
Consumers must remain vigilant, especially during peak shopping periods, and adopt stronger security measures like two-factor authentication, secure payment options, and cautious browsing habits. Additionally, a comprehensive security solution detecting and blocking malware and phishing pages and providing financial data protection features may help stay safe amid the shopping rush.
Source:: Securelist
