Three men in the United Kingdom have pleaded guilty to operating otp[.]agency, a once popular online service that helped attackers intercept the one-time passcodes (OTPs) that many websites require as a second authentication factor in addition to passwords.
Launched in November 2019, OTP Agency was a service for intercepting one-time passwords needed to log in to various websites. Scammers who had already stolen someone’s bank account credentials could enter the target’s phone number and name, and the service would initiate an automated phone call to the target that warned them about unauthorized activity on their account.
The call would prompt the target to enter a one-time passcode generated by their phone’s mobile app, and the code was then relayed to the scammer’s user panel at the OTP Agency website.
A statement published Aug. 30 by the U.K.’s National Crime Agency (NCA) said three men pleaded guilty to running OTP Agency: Callum Picari, 22, from Hornchurch, Essex; Vijayasidhurshan Vijayanathan, 21, from Aylesbury, Buckinghamshire; and Aza Siddeeque, 19, from Milton Keynes, Buckinghamshire.
KrebsOnSecurity profiled OTP Agency in a February 2021 story about arrests tied to another phishing-related service based in the U.K. Someone claiming to represent OTP Agency then posted several comments on the piece, wherein they claimed the story was libelous and that they were a legitimate anti-fraud service. However, the service’s Telegram channel clearly showed its proprietors had built OTP Agency with one purpose in mind: To help their customers take over online accounts.
Within hours of that publication, OTP Agency shuttered its website and announced it was closing up shop and purging its user database. The NCA said the February 2021 story prompted a panicked message exchange between Picari and Vijayanathan:
Picari said: bro we are in big trouble… U will get me bagged… Bro delete the chat
Vijayanathan: Are you sure
Picari: So much evidence in there
Vijayanathan: Are you 100% sure
Picari: It’s so incriminating…Take a look and search ‘fraud’…Just think of all the evidence…that we cba to find…in the OTP chat…they will find
Vijayanathan: Exactly so if we just shut EVERYTHING down
Picari: They went to our first ever msg…We look incriminating…if we shut down…I say delete the chat…Our chat is Fraud 100%
Vijayanathan : Everyone with a brain will tell you stop it here and move on
Picari: Just because we close it doesn’t mean we didn’t do it…But deleting our chat…Will f*^k their investigations…There’s nothing fraudulent on the site
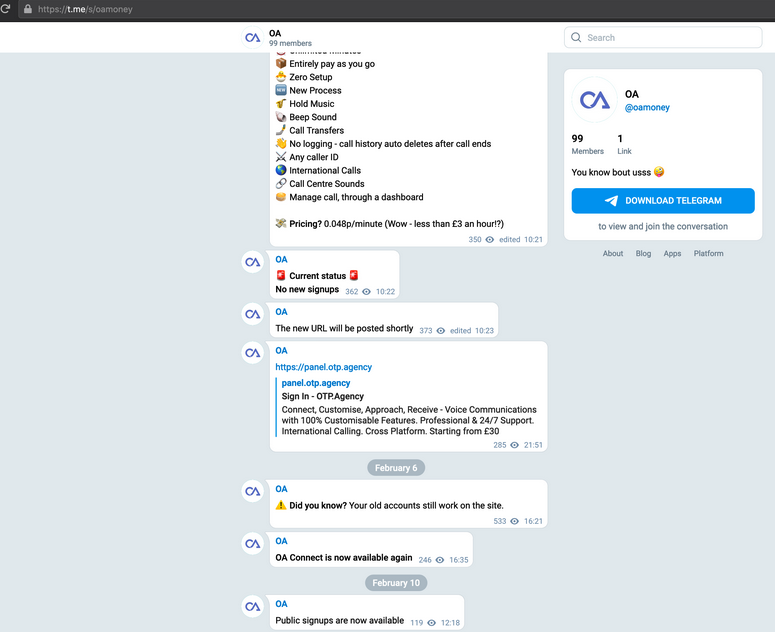
Despite deleting its Telegram channel, OTP Agency evidently found it difficult to walk away from its customers (and/or the money). Instead of shutting down as Vijayanathan wisely advised, just a few days later OTP Agency was communicating with customers on a new Telegram channel, offering a new login page and assuring existing customers that their usernames, passwords and balances would remain the same.
OTP Agency, immediately after their initial shutdown, telling customers their existing logins will still work.
But that revival would be short-lived. The NCA said the site was taken offline less than a month later when the trio were arrested. NCA investigators said more than 12,500 people were targeted by OTP Agency users during the 18 month the service was active.
Picari was the owner, developer and main beneficiary of the service, and his personal information and ownership of OTP Agency was revealed in February 2020 in a “dox” posted to the now-defunct English-language cybercrime forum Raidforums. The NCA said it began investigating the service in June 2020.

The OTP Agency operators who pleaded guilty to running the service; Aza Siddeeque, Callum Picari, and Vijayasidhurshan Vijayanathan.
OTP Agency might be gone, but several other similar OTP interception services are still in operation and accepting new customers, including a long-running service KrebsOnSecurity profiled in September 2021 called SMSRanger. More on SMSRanger in an upcoming post.
Text messages, emails and phone calls warning recipients about potential fraud are some of the most common scam lures. If someone (or something) calls saying they’re from your bank, or asks you to provide any personal or financial information, do not respond. Just hang up, full stop.
If the call has you worried about the security and integrity of your account, check the account status online, or call your financial institution — ideally using a phone number that came from the bank’s Web site or from the back of your payment card.
Further reading: When in Doubt, Hang Up, Look Up, and Call Back
Source:: KrebsOnSecurity