IT threat evolution Q1 2024
IT threat evolution Q1 2024. Mobile statistics
IT threat evolution Q1 2024. Non-mobile statistics
Targeted attacks
Operation Triangulation: the final mystery
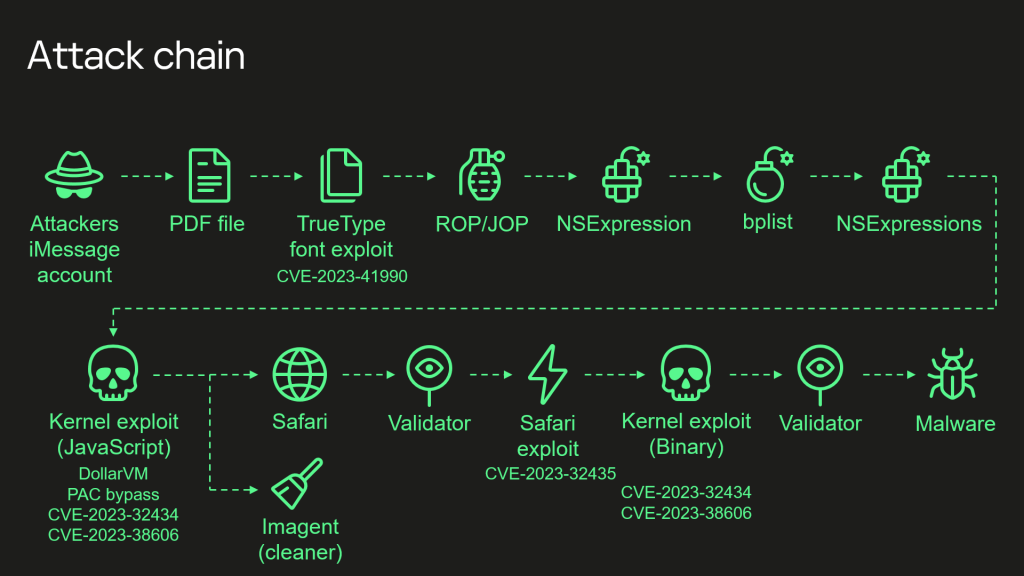
Last June, we published a series of reports on Operation Triangulation, a previously unknown iOS malware platform distributed via zero-click iMessage exploits that allowed an attacker to browse and modify device files, get passwords and credentials stored in the keychain, retrieve geo-location information and execute additional modules that extended their control over compromised devices.
In late December, in a presentation at the 37th Chaos Communication Congress (37C3), experts from our Global Research and Analysis Team (GReAT) described the attack chain in detail, including – for the first time – how the attackers exploited the CVE-2023-38606 hardware vulnerability.
Recent iPhone models include additional hardware-based security that prevents attackers from taking full control over the device even if they can read and write kernel memory – as was accomplished in the Operation Triangulation attack by exploiting the CVE-2023-32434 vulnerability. The attackers were able to bypass this hardware-based security protection using another hardware feature of Apple-designed SoCs (System on a Chip): they did this by writing the data, destination address and data hash to unknown hardware registers of the chip that are not used by the firmware.
We would guess that this unknown hardware feature was probably intended for debugging or testing purposes, or was included by mistake. Since it is not used by the firmware, we have no idea how the attackers learned to use it.
A lightweight method for detecting potential iOS malware
Over the past few years, our researchers have analyzed Pegasus malware infections on several iOS devices. The common methods for analyzing an iOS mobile infection are either to examine an encrypted full iOS backup or to analyze the network traffic of the affected device. However, both methods are time consuming and require a high level of expertise. This led us to look for a faster and easier way to identify possible iPhone infections.
During our analysis, we discovered that infections left traces in an unexpected system log, shutdown.log. This is a text-based system log file available on every mobile iOS device. Each reboot event is logged in this file, along with multiple environment characteristics: these log files can have entries going back several years, providing a wealth of information. The shutdown.log file is stored in a sysdiagnose (sysdiag) archive – this can be thought of as a collection of system logs and databases that can be generated for debugging and troubleshooting purposes. The method for generating a sysdiag can vary across different iOS versions. Nevertheless, this archive is usually located in the OS general settings, specifically under ‘Privacy and Analytics’ (the exact location name may, again, vary between iOS versions). Creating the archive usually takes only a few minutes. The result is a .TAR.GZ file about 200-400MB in size, which can then be transferred to the analysis machine. Once the archive is unpacked, the shutdown.log file is located in the system_logs.logarchiveExtra directory.
This sysdiag dump analysis is a minimally intrusive and resource-light method of identifying possible iPhone infections using system-based artifacts. It can be used to complement infection identification from a different vantage point.
You can read the full analysis here.
DinodasRAT Linux implant targeting entities worldwide
In early October 2023, after ESET published an article by about a campaign dubbed Operation Jacana targeting Windows users, we discovered a new Linux version of DinodasRAT (aka XDealer). The code and networking IoCs (Indicators of Compromise) overlap with the Windows samples described by ESET that were used in attacks against government entities in Guyana. Sample artifacts suggest that this version (V10, according to the attackers’ versioning system) may have started operating in 2022, although the first known Linux variant (V7), which has still not been publicly described, dates back to 2021.
DinodasRAT is a multi-platform backdoor written in C++ that offers a range of capabilities. This RAT allows an attacker to surveil and harvest sensitive data from a target computer. The backdoor is fully functional, giving the operator complete control over an infected machine, enabling data exfiltration and espionage.
The DinodasRAT Linux implant primarily targets Red Hat-based distributions and Ubuntu Linux. In our telemetry data and continuous monitoring of this threat since October 2023, we have observed that the most affected countries and territories are mainland China, Taiwan, Turkey and Uzbekistan.
Other malware
New macOS backdoor stealing crypto wallets
Last December, we discovered some cracked apps circulating on pirate websites and infected with a Trojan proxy. Recently, we found a new macOS malware family that was piggybacking the cracked software in order to steal crypto wallets.
Cracked applications are one of the easiest ways for attackers to get malware onto people’s computers: to elevate their privileges, they only need to ask for the password, which usually arouses no suspicion during software installation.
However, some of the things the malware authors came up with, such as placing their Python script inside a domain TXT record on the DNS server, were ingenious. The script was later added to startup agents to download and execute the next-stage payload in an infinite loop, so the malware operators could deliver updates to the infected machine as needed.
The final payload was a backdoor that could run scripts with administrator privileges and replace Exodus and Bitcoin crypto wallet applications with infected versions that stole secret recovery phrases during the wallet unlock process.
Read our analysis here.
Coyote: a multi-stage banking Trojan
Developers of banking Trojans are constantly looking for new ways to distribute their implants. In a recent investigation, we came across new malware called Coyote that targets customers of more than 60 banking institutions, mainly from Brazil. What caught our attention was the sophisticated infection chain that makes use of several advanced technologies that set it apart from other banking Trojans.
Instead of using Delphi or an MSI installer for distribution, Coyote uses a relatively new tool for installing and updating Windows desktop applications called Squirrel. In this way, the malware authors hope to disguise the Trojan as an update packager.
When Squirrel is executed, it ends up running a NodeJS application compiled with Electron. This application executes obfuscated JavaScript code to copy all executables found in a local folder named temp to the user’s captures folder inside the Videos folder: it then runs a signed application from that directory.
An interesting element of the infection chain is the use of Nim, a relatively new programming language, to load the final stage. The loader’s objective is to unpack a .NET executable and execute it in memory using the CLR. This implies that the loader aims to load the executable and execute it within its process, reminiscent of how Donut works.
After all these steps, the Coyote Trojan is executed.

Coyote infection chain
The goal of the Coyote Trojan is consistent with typical banking Trojan behavior. It monitors all open applications on the infected system and waits for the user to access the specific banking application or website.
Network tunneling with … QEMU
Cyber attackers often use legitimate tools to evade detection systems and keep development costs to a minimum. Network scanning, capturing a process memory dump, exfiltrating data, running files remotely, and even encrypting drives – can all be done with trusted software. To gain a foothold inside a compromised infrastructure and develop the attack, adversaries can use previously installed malware or connect to the network through the company’s RDP servers or corporate VPN (to do this, the attackers must have access to accounts with appropriate privileges).
Another way to connect to the internal network of an attacked organization is to use utilities to set up network tunnels or forward network ports between corporate systems and the adversary’s servers, allowing attackers to bypass NAT and firewalls to gain access to internal systems. There is no shortage of utilities that can be used to create a network tunnel between two systems. Some connect directly, while others use a proxy, which hides the IP address of the attacker’s server.
While investigating an incident at a large company, we noticed unusual malicious activity inside one of the systems. We analyzed the artifacts and found that the adversary had deployed and launched (a) the Angry IP Scanner network scanning utility, (b) the Mimikatz password, hash, and Kerberos ticket extractor and Active Directory attack tool, and (c) the QEMU hardware emulator. While the first two were self-explanatory, QEMU raised some questions; what use would threat actors have for a virtualizer?
We discovered that QEMU supports connections between virtual machines: the -netdev option creates network devices (backend) that can then connect to virtual machines. We had no way of reliably determining how the attackers ran QEMU on their own server, so we decided to set up a bed consisting of three systems, as follows:
- “InternalHost” was located inside the network, with no internet access and running an RDP server on port 3389. It simulated the isolated system without access to the internet.
- “PivotHost” was located inside the network, but it had internet access. It simulated the system that had been breached by the attackers and used to reach InternalHost.
- “AttackerServer” was hosted in the cloud and simulated the adversary’s server.
Our goal was to reach InternalHost from AttackerServer. The diagram below shows the general layout of the tunnel.

Network tunnel diagram
We were able to determine that this technique for gaining network access was indeed effective. You can read the details of our investigation here.
While the use of legitimate tools to perform various attack steps is nothing new to incident response professionals, attackers sometimes come up with ingenious uses for unlikely software, as was the case with QEMU. This underscores the need for multi-level protection that includes both reliable endpoint protection and specialized solutions to detect and protect against complex and targeted attacks, including human-operated ones.
Source:: Securelist
