This post is also available in 简体中文, 繁體中文, 한국어, 日本語, Français, Deutsch and Español.
Managing risk posture — how your business assesses, prioritizes, and mitigates risks — has never been easy. But as (ZTNA), only allowing access when the Falcon ZTA risk score is above a specific threshold they have defined.
Our ZTNA denies the user’s next request to access an application because the Falcon ZTA score falls below that threshold.
Because of this failed device posture check, Cloudflare increases the risk score for that user, which places them in a group with more restrictive controls.
In parallel, CrowdStrike’s Next-GenSIEM has continued to analyze the specific user’s activity and broader risks throughout the organization’s environment. Using machine learning models, CrowdStrike surfaces top risks and proposes solutions for each risk to your analyst.
The analyst can then review and select remediation tactics — for example, quarantining the user’s device — to further reduce risk throughout the organization.
Use Case #2: Protect apps, APIs, & websites
This next use case is focused on protecting apps, APIs, and websites from threat actors and bots. Many customers first adopt Cloudflare for this use case, but may not be aware of the risk evaluation algorithms underpinning their protection.
Figure 3: Protect apps, APIs & sites with ML-backed threat intelligence
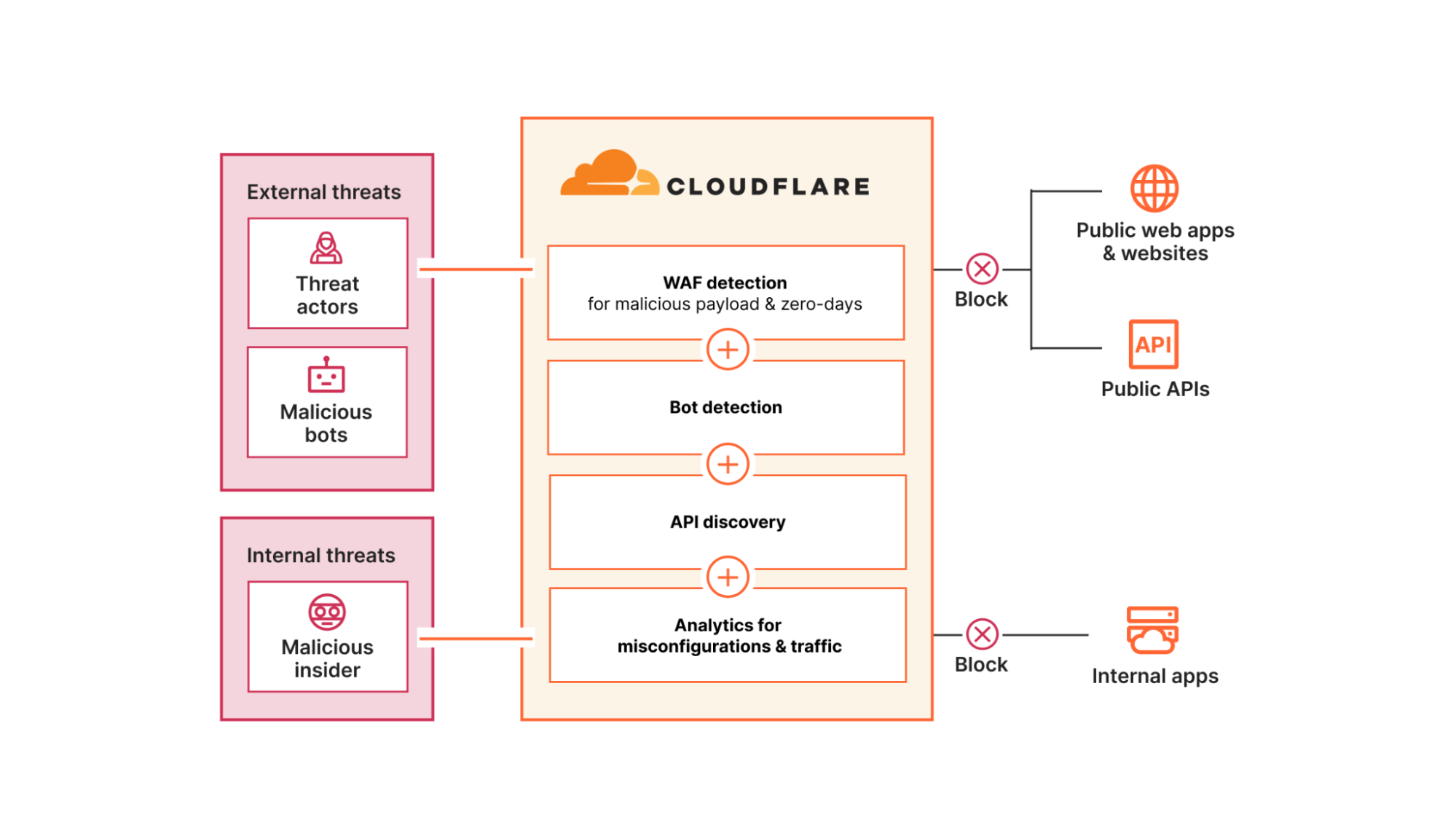
Cloudflare’s Application Services detect and mitigate malicious payloads and bots using risk models backed by machine learning (ML) including:
- Our WAF attack score, which scores whether a request contains a zero-day exploit, or common OWASP Top 10 risks such as a SQL injection, cross-site scripting, or remote code execution payload
- Our bot score, which scores the likelihood that a request came from a bot
- Our malicious script classifier, which looks at the dangers of browser scripts for your website visitors
These risk models are trained largely on telemetry from Cloudflare’s global network, which is used as a reverse proxy by nearly 20% of all websites and sees about 3 trillion DNS queries per day. This unique real-time visibility powers threat intelligence and even enables us to detect and mitigate zero-days before others.
Cloudflare also uses ML to discover new API endpoints and schemas without requiring any prerequisite customer input. This helps organizations uncover unauthenticated APIs and map their growing attack surface before applying protections.
Unlike other vendors, Cloudflare’s network architecture enables risk evaluation models and security controls on public-facing and internal infrastructure to be shared across all of our services. This means that organizations can apply protections against app vulnerability exploits, DDoS, and bots in front of internal apps like self-hosted Jira and Confluence servers, protecting them from emerging and even zero-day threats.
Organizations can review the potential misconfigurations, data leakage risks, and vulnerabilities that impact the risk posture for their apps, APIs, and websites within Cloudflare Security Center. We are investing in this centralized view of risk posture management by integrating alerts and insights across our security portfolio. In fact, we recently announced updates focused on highlighting where gaps exist in how your organization has deployed Cloudflare services.
Finally, we are also making it easier for organizations to investigate security events directly and recently announced beta availability of Log Explorer. In this beta, security teams can view all of their HTTP traffic in one place with search, analytics dashboards, and filters built-in. These capabilities can help customers monitor more risk factors within the Cloudflare platform versus exporting to third party tools.
Use Case #3: Protect sensitive data with UEBA
This third use case summarizes one common way many customers plan to leverage our user risk / UEBA scores to prevent leaks and mishandling of sensitive data:
Figure 4: Protect apps, APIs & sites with ML-backed threat intelligence
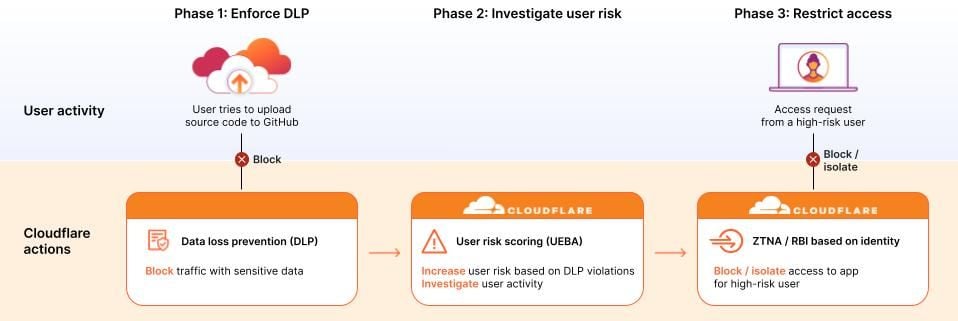
- Phase 1: In this example, the security team has already configured data loss prevention (DLP) policies to detect and block traffic with sensitive data. These policies prevent one user’s multiple, repeated attempts to upload source code to a public GitHub repository.
- Phase 2: Because this user has now violated a high number of DLP policies within a short time frame, Cloudflare scores that suspicious user as high risk, regardless of whether those uploads had malicious or benign intent. The security team can now further investigate that specific user, including reviewing all of his recent log activity.
- Phase 3: For that specific high-risk user or for a group of high-risk users, administrators can then set ZTNA or even browser isolation rules to block or isolate access to applications that contain other sensitive data.
Altogether, this workflow highlights how Cloudflare’s risk posture controls adapt to suspicious behavior from evaluation through to enforcement.
How to get started with unified risk posture management
The above use cases reflect how our customers are unifying risk management with Cloudflare. Through these customer conversations, a few themes emerged for why they feel confident in our vision to help them manage risk across their expanding attack surface:
- The simplicity of our unified platform: We bring together SASE and WAAP risk scoring and controls for people and apps. Plus, with a single API for all Cloudflare services, organizations can automate and customize workflows with infrastructure-as-code tools like Terraform with ease.
- The flexibility of our integrations: We exchange risk signals with the EPP, IDP, XDR, and SIEM providers you already use, so you can do more with your tools and data. Plus, with one-time integrations that work across all our services, you can extend controls across your IT environments with agility.
- The scale of our global network: Every security service is available for customers to run in every location across our network spanning 320+ locations and 13K+ interconnects. In this way, single-pass inspection and risk policy enforcement is always fast, consistent, and resilient, delivered close to your users and apps.
If you’re ready to see how Cloudflare can help you manage risk, request a consultation today. Or if you’re at RSA Conference 2024, come to any of our in-person events.
To continue learning more about how Cloudflare can help you evaluate risk, exchange risk indicators, and enforce risk controls, explore more resources on our website.
Source:: CloudFlare
