IoT devices (routers, cameras, NAS boxes, and smart home components) multiply every year. Statista portal predicts their number will exceed 29 billion by 2030. As connected device numbers increase, so does the need for protection against various threats. The first-ever large-scale malware attacks on IoT devices were recorded back in 2008, and their number has only been growing ever since. We conducted an analysis of the IoT threat landscape for 2023, as well as the products and services offered on the dark web related to hacking connected devices. This report contains the key findings of our research.
Attack vectors
There are two main IoT infection routes: brute-forcing weak passwords and exploiting vulnerabilities in network services.
Telnet, the overwhelmingly popular unencrypted IoT text protocol, is the main target of brute-forcing. A successful password cracking enables hackers to execute arbitrary commands on a device and inject malware. Brute-force attacks on services that use SSH, a more advanced protocol that encrypts traffic, can yield similar outcomes. However, it takes more resources to attack SSH, while the number of services accessible online is smaller compared to Telnet.
In the first half of 2023, 97.91% of password brute-force attempts registered by our honeypots targeted Telnet, and only 2.09%, SSH. The majority of infected devices that carried out these attacks were traced to China, India, and the United States, while China, Pakistan, and Russia were the most actively attacking countries.
Ten countries and territories where most devices that attacked Kaspersky honeypots were located, H1 2023 (download)
Ten countries and territories where most attacks on Kaspersky honeypots came from, H1 2023 (download)
Brute-force attacks are fairly common as Telnet and SSH services running on IoT devices typically use widely known default passwords. Unfortunately, users tend to leave these passwords unchanged. As if that were not enough, many IoT devices have unalterable main passwords set by manufacturers.
Another way of compromising a device is by leveraging vulnerabilities in the services that run on it. Injecting malicious code into requests sent to the web interface is the most common way of exploiting vulnerabilities. The consequences of these attacks can be substantial, such as in the case of a vulnerability in the TR-064 protocol implementation used by ISPs to automate configuration of devices on the LAN. The security flaw enabled unauthenticated transmission of TR-064 packets, resulting in the proliferation of the Mirai malware.
Regardless of the compromising technique, IoT devices may come under attack both from malicious actors’ own servers and from malware through so-called self-spreading, whereby malicious files seek out vulnerable devices online and implant copies onto them through diverse means. In the latter scenario, the attack may also originate from an IoT device infected earlier.
Dark web services: DDoS attacks, botnets, and zero-day IoT vulnerabilities
Of all IoT-related services offered on the dark web, DDoS attacks are worth examining first. Botnets made up of IoT devices and utilized for distributed DoS attacks have become more prevalent on dark web forums and are in high demand among hackers.
See translation
I’m the world’s best-known DDoS attacker for hire (getting ahead of myself here). Not going to waffle — I’ll just tell you why it is my service you should choose.
Our advantages:
1. Botnet based on Medusa, working since 2020. Starts ~50 browser instances per Windows PC which evade any anti-DDoS defense.
10,000–80,000 online devices: the largest Windows or IoT botnet in 2023.
In the first half of 2023, Kaspersky Digital Footprint Intelligence service analysts discovered a total of more than 700 ads for DDoS attack services posted on various dark web forums.
DDoS ads distributed by month, H1 2023 (download)
The price of a service like that is driven by numerous factors that determine attack complexity, such as DDoS protection, CAPTCHA, and JavaScript verification on the victim’s side. The overall cost of an attack varies between $20 per day and $10,000 per month. The average price charged by those who posted the ads was $63.5 per day, or $1350 per month.
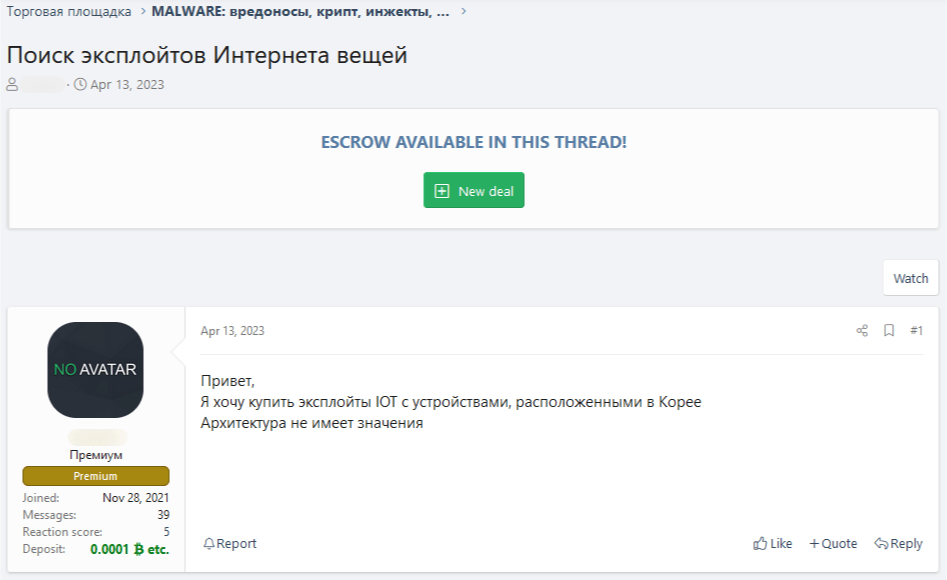
Another type of service sold on the dark web is IoT hacking. Cybercriminals seek exploits for zero-day vulnerabilities in IoT devices.
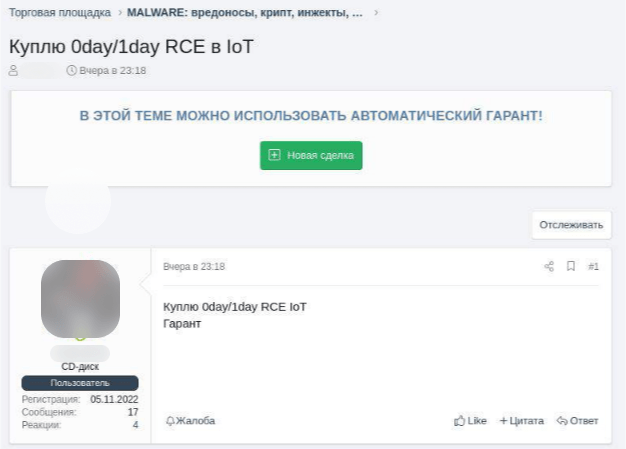
See translation
Will buy 0day/1day RCE in IoT
Escrow

See translation
Hi,
I want to buy IoT exploits with devices located in Korea
Any architecture
There are also offers to purchase and sell IoT malware on dark web forums, often packaged with infrastructure and supporting utilities. In the screenshot below, the vendor is offering a homebrew DDoS bot complete with a C2 server and software for uploading the malware via Telnet or SSH:
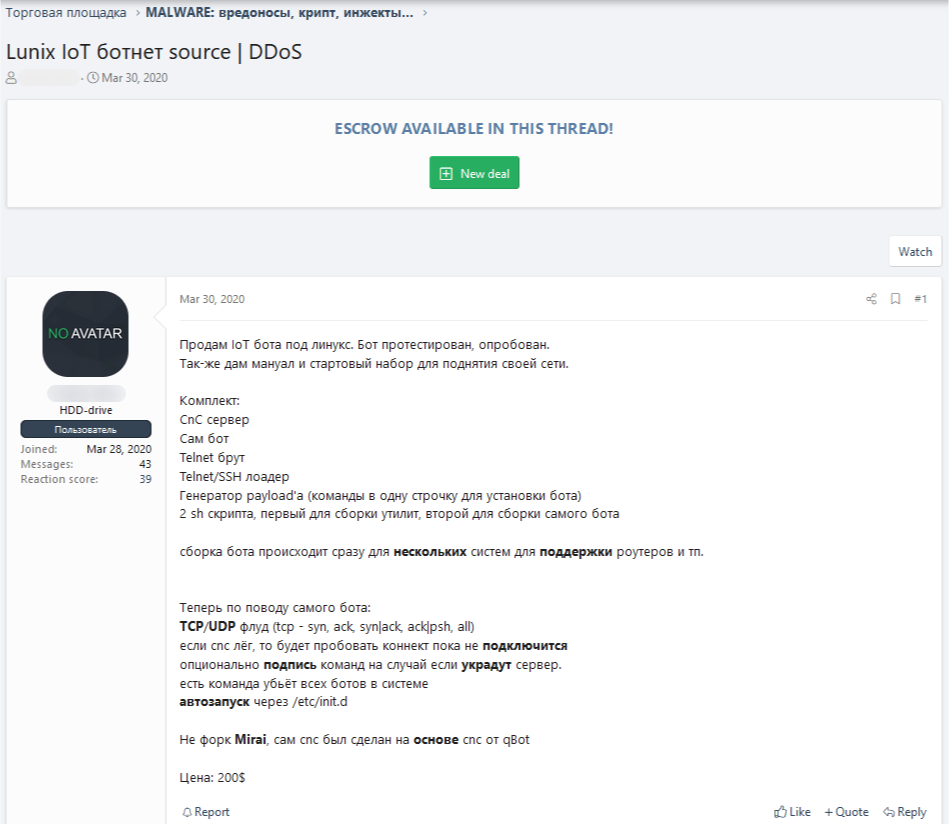
See translation
Selling Linux IoT bot. Tested, tried.
Comes with a manual and network startup kit.
What’s in the box:
C2 server
The bot
Telnet brute force
Telnet/SSH loader
Payload generator (one-line commands for installing the bot)
2 .sh scripts: utility and bot compilers
Bot compiles for several systems at once to support routers, etc.
As for the bot itself:
TCP/UDP flood (tcp – syn, ack, syn|ack, ack|psh, all)
If C2 down, will try to reconnect until successful
Optional signed commands in case C2 gets stolen
Command to kill all bots in the system
Autorun via /etc/init.d
Not a Mirai fork. C2 based on qBot
Price: $200
Below that, you can see a screenshot of an ad where the poster seeks both malware and help with installing it.
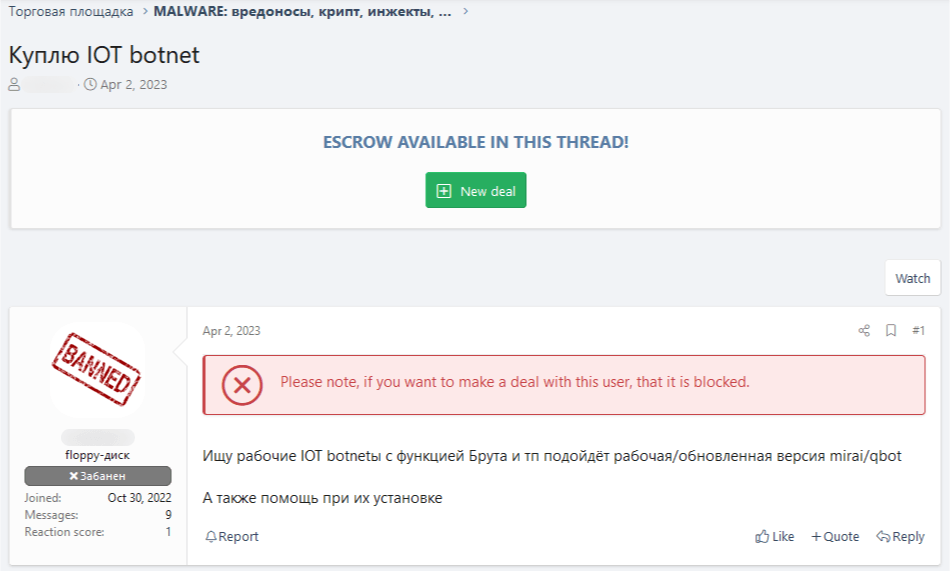
See translation
Looking for functional IoT botnets with brute force, etc. Working/updated mirai/qbot mod will work.
Also looking for help installing these
In some cases, sellers or buyers specify the target type of IoT device.
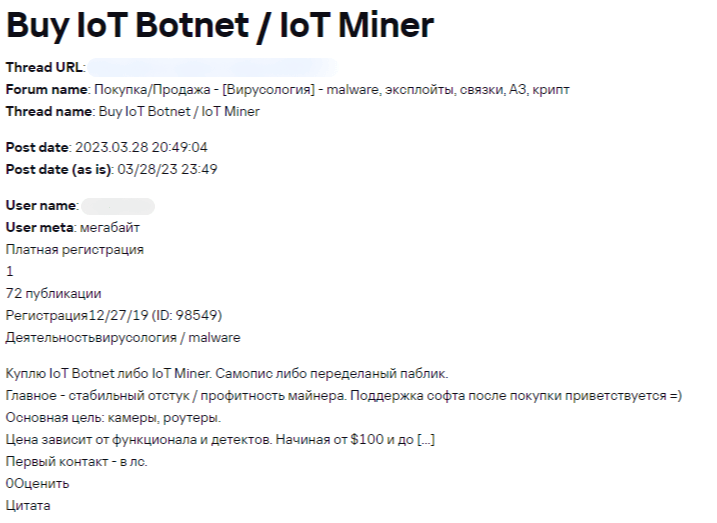
See translation
Buy IoT Botnet / IoT Miner
Will buy IoT botnet or miner. Custom-written or modified public.
Stable ping / miner profitability is what matters. After-purchase support is a plus =)
Key targets: webcams, routers.
Price: varies with features and detects. From $100 to […]
First contact via PM.
Screenshot of an ad from the Kaspersky Threat Intelligence Portal stream
In rare instances, networks of pre-infected devices are also available for purchase on dark web forums. However, adverts of this nature are infrequent. For instance, the user in the screenshot below is searching for a new owner for a botnet of 200 routers and cameras located in Argentina.
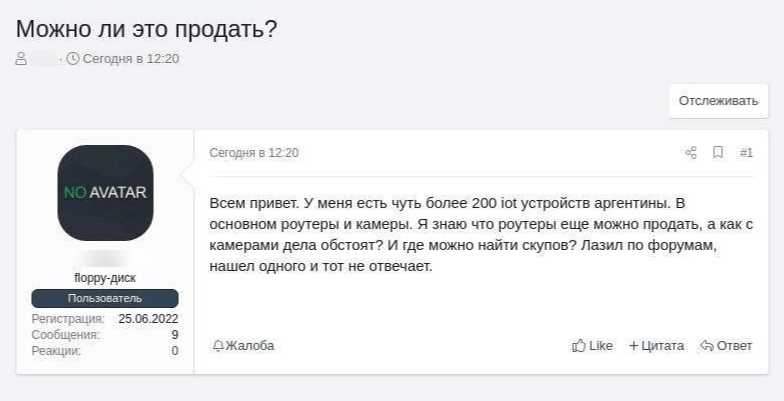
See translation
Hey all! I have a tad over 200 iot devices in Argentina, mostly webcams and routers. I know the routers can be sold, but what about the webcams? Where do I find buyers? Found one while browsing forums, but they wouldn’t reply.
Objectives and types of malware that attacks the IoT
Bad actors who infect IoT devices may be pursuing diverse goals. They may be looking to exploit the infected hardware as a tool to launch cyberattacks, camouflage malicious traffic, leverage the resources of the devices for crypto mining, or demand a ransom to restore access to the device. Some may attack any IoT device, while others, only certain types of hardware that are capable of serving their objectives. Below, we provide an overview of purpose-specific types of IoT malware.
DDoS botnets
Trojans that hijack a device and use it to initiate DoS attacks targeting various services are the most frequently observed type of IoT malware. For DDoS malware, the targeted device type is irrelevant, as each device is capable of fulfilling the attacker’s goal: sending requests over the Web. Although most of these malicious programs stem from modified Mirai code, there are many other families that differ in their techniques for spreading and gaining persistence.
For example, RapperBot, although utilizing some portions of the Mirai code base, consists mostly of original code. Its capabilities include smart brute-forcing by analyzing the initial request for authentication data it receives from a Telnet service. The malware can use that request to identify the device type and proceed to brute-force passwords specific to that type only, thereby boosting its self-spreading performance.
Ransomware
Unlike DDoS malicious programs, ransomware largely targets IoT devices that contain user data: NAS boxes. DeadBolt, which affected thousands of QNAP NAS devices in 2022, is a prominent example of IoT ransomware. The attack took advantage of CVE-2022-27593, a vulnerability that allowed bad actors to modify system files on the box. User files were encrypted, with the device’s interface displaying a ransom note demanding payment of 0.03 BTC to recover the data. Although the manufacturer issued an update that resolved the vulnerability, similar attacks remain a concern.
Miners
Attackers made attempts at using IoT devices for Bitcoin mining during Mirai campaigns, despite their low processing power. The practice has not become widespread due to relative inefficiency.
DNS changer
Malicious actors may use IoT devices to target users who connect to them. A 2022 campaign known as Roaming Mantis, or Shaoye, spread an Android app whose capabilities included modifying DNS settings on Wi-Fi routers through the administration interface. Any router still using the default access credentials, like admin:admin, could be infected. On such a device, the configuration would be altered to make it use the operators’ DNS server. This server then redirects all users who connect to the router to a website that uploaded malicious APK files to Android devices and displayed phishing pages on iOS devices.
Proxy bots
Another widespread way of abusing infected IoT devices is to leverage them as proxy servers that redirect malicious traffic, making it difficult to track. These proxy servers are mostly employed for spam campaigns, evasion of antifraud systems, and various network attacks.
IoT malware: competition and persistence
IoT malware is notable for a huge diversity of families derived from Mirai, which was first discovered in 2016. The source code of Mirai was posted on a dark web forum, encouraging hundreds of modifications that appeared within a short time, using various DDoS techniques, brute-force dictionaries, and vulnerabilities leveraged for self-spreading.
The significant number of players resulted in fierce competition among cybercriminals: both those who specialized in DDoS attacks and those who targeted the IoT at large. Consequently, malware developers started to add features intended to neutralize competing products on the infected device and prevent further infection by competitors.
The most commonly used preemptive tactic is adding firewall rules that block incoming connection attempts. Less frequently, remote device management services will be shut down. Malware that arrives late to the party will search for certain process names, scan ports, and analyze the device memory for malicious patterns to suppress infections already present on the device. Processes associated with competitors will be terminated and files, deleted, as hackers vie for control over the device.
Other threats stemming from the lack of IoT device security
Attackers have shown interest in Web-connected video cameras, as evidenced in ads for buying and selling access to compromised IoT devices. Various ways exist to monetize Illicit access to webcams. Cameras may be hacked for their CPU power only, to mine crypto, or to install DDoS utilities. They can be made to serve as routers (proxies or VPN servers) to anonymize illicit traffic. Some hackers even use them as, well, web cameras.
An illustration of that is a recent incident involving a Moscow Oblast, Russia resident who found that private footage shot by a camera she had purchased on AliExpress to monitor her dog has somehow found its way onto some Chinese websites.
Security researcher Paul Marrapese who has studied the consumer webcam segment says security holes are not uncommon. Regrettably, vendors could have done a much better job fixing those. Paul has discovered critical vulnerabilities in the firmware and protocols of certain webcam models, and one of the vendors he contacted never even got back to him to discuss remediation.
It is worth mentioning that manufacturers of such cameras often employ various implementations of peer-to-peer (P2P) protocols, such as Shenzhen Yunni iLnkP2P or CS2 Network P2P, which they share with more than 50 million other devices. These protocols either poorly encrypt traffic or use no encryption at all, exposing devices to man-in-the-middle (MitM) attacks. An attacker can easily eavesdrop on device traffic and steal user credentials or redirect the video stream.
According to a study by Trend Micro, peeping into webcam owners’ private lives is anything but rare. However, it is worth noting that aside from cameras, a variety of other IoT devices may be used for snooping. For example, despite their primary function not being related to video surveillance, most smart pet feeders on the market can capture real-time audio and video footage. While their popularity is soaring and new models are coming out to fulfill rising demand, vendors often neglect to protect these devices properly. Our recent test of a popular smart feeder model exposed a massive number of security vulnerabilities. Exploiting these weaknesses enables the device to be used for spying on pet owners, in addition to creating other opportunities for hackers.
Kids’ smart devices are another category of IoT devices that calls for increased focus on security. Sadly, some vendors do not take this seriously. We witnessed the lack of security in these devices for the first time when a maker of smartwatches commissioned our Product Security Maturity Assessment using the IoT Security Maturity Model approach developed by the Industry IoT Сonsortium. The vendor failed the test as security issues that we found were bad enough to essentially convert the product into a surveillance tool for watching the kid and their surroundings. Therefore, we did not issue a certificate.
Issues of inadequate security plague both consumer and industrial IoT devices. The latter may also contain basic security flaws, and their vendor-recommended settings may be unsafe.
The most common configuration issue in industrial IoT devices is using default passwords. For example, one manufacturer of media converters used for connecting elevator equipment to control room monitoring systems supplied these along with highly unsafe connection and configuration tips in the service documentation. On top of that, our researchers found that the devices themselves contained vulnerabilities that could be exploited even by not-so-highly-skilled hackers to assume full control of the converter. The recommendations were later updated to remove the insecure settings. However, the device vendor, who initially showed promptness in fixing security issues, soon lost all of that responsible spirit. As a result, many of the vulnerabilities we discovered remain unpatched to this day, over a year after receiving the notice from us.
One might get the impression that we consider all IoT devices insecure and the vendors, neglectful of the culture of secure development. That is not quite so. As an example, Bosch has attained our product security maturity certificate for a smart camera intended for industrial applications. We would really like all vendors of IoT devices intended for both consumers and industrial users to prioritize the cybersecurity of their products as much as they can.
Conclusion
IoT devices attract hackers for many reasons: they can be used to carry out DDoS attacks, camouflage traffic, or snoop on owners through built-in webcams. Similarly, NAS boxes may be targeted by ransomware gangs, and routers, by malicious actors who are after devices that connect to those, including smartphones on public Wi-Fi networks or other devices on the victim’s LAN.
Besides relentlessly attacking the IoT, hackers offer their services on the dark web market. That said, most connected devices, including those in industrial environments, remain easy prey due to the use of default passwords and the presence of device vulnerabilities, some of which the vendors never get to fixing. Vendors of both home and industrial IoT devices should adopt a responsible approach to product cybersecurity and introduce protective measures at the product design phase. In particular, we recommend abandoning default passwords in favor of unique ones for each individual unit and releasing patches on a regular basis to address any discovered vulnerabilities.
Source:: Securelist