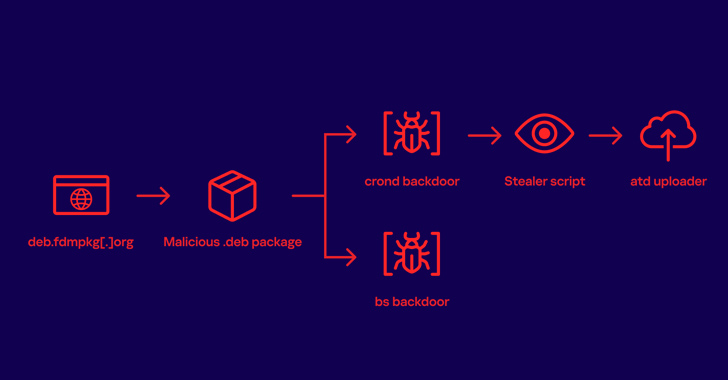
A download manager site served Linux users malware that stealthily stole passwords and other sensitive information for more than three years as part of a supply chain attack.
The modus operandi entailed establishing a reverse shell to an actor-controlled server and installing a Bash stealer on the compromised system. The campaign, which took place between 2020 and 2022, is no longer active.
”
Source:: The Hackers News
