
Over the last few years, Linux machines have become a more and more prominent target for all sorts of threat actors. According to our telemetry, 260,000 unique Linux samples appeared in the first half of 2023. As we will demonstrate in this article, campaigns targeting Linux can operate for years without being noticed by the cybersecurity community.
We discovered one such long-lasting attack when we decided to investigate a set of suspicious domains, among them:
- 2c9bf1811ff428ef9ec999cc7544b43950947b0f.u.fdmpkg[.]org
- c6d76b1748b67fbc21ab493281dd1c7a558e3047.u.fdmpkg[.]org
- 0727bedf5c1f85f58337798a63812aa986448473.u.fdmpkg[.]org
- c3a05f0dac05669765800471abc1fdaba15e3360.u.fdmpkg[.]org
To a security researcher’s eye, these domains look alarming, as they can be a sight of malware using domain-generation algorithms for C2 communications. We thus decided to take a close look at the fdmpkg[.]org domain.
A malicious Debian repository
We identified that the domain in question has a deb.fdmpkg[.]org subdomain. Going there in the browser shows the following web page:
As suggested by the page, this subdomain claims to host a Debian repository of a piece of software called ‘Free Download Manager’. We further discovered a Debian package of this software available for download from the https://deb.fdmpkg[.]org/freedownloadmanager.deb URL. This package turned out to contain an infected postinst script that is executed upon installation. This script drops two ELF files to the paths /var/tmp/crond and /var/tmp/bs. It then establishes persistence by creating a cron task (stored in the file /etc/cron.d/collect) that launches the /var/tmp/crond file every 10 minutes.
The version of Free Download Manager installed by the infected package was released on January 24, 2020. Meanwhile, the postinst script contains comments in Russian and Ukrainian, including information about improvements made to the malware, as well as activist statements. They mention the dates 20200126 (January 26, 2020) and 20200127 (January 27, 2020).

A DNS-based backdoor
Once the malicious package is installed, the executable /var/tmp/crond gets launched on every startup through cron. This executable is a backdoor, and it does not import any functions from external libraries. To access the Linux API, it invokes syscalls with the help of the statically linked dietlibc library.
Upon startup, this backdoor makes a type A DNS request for the .u.fdmpkg[.]org domain. In response to this request, the backdoor receives two IP addresses that encode the address and port of a secondary C2 server. The following addresses were returned at the time of our research:
- 172.111.48[.]101
- 172.1.0[.]80
The first IP address in the list above is the address of the secondary C2 server, while the second address contains the connection port (encoded in the third and fourth octets) and the connection type (encoded in the second octet).
After parsing the response of the DNS request, the backdoor launches a reverse shell, using the secondary C2 server for communications. The communication protocol is, depending on the connection type, either SSL or TCP. In the case of SSL, the crond backdoor launches the /var/tmp/bs executable and delegates all further communications to it. Otherwise, the reverse shell is created by the crond backdoor itself.
A Bash stealer
Having found out that the crond backdoor creates a reverse shell, we decided to check how this shell is used by attackers. To do that, we installed the infected Free Download Manager package in a malware analysis sandbox. Having analyzed the traffic generated by crond, we determined that the attackers deployed a Bash stealer to the sandbox. This stealer collects data such as system information, browsing history, saved passwords, cryptocurrency wallet files, as well as credentials for cloud services (AWS, Google Cloud, Oracle Cloud Infrastructure, Azure).

After collecting information from the infected machine, the stealer downloads an uploader binary from the C2 server, saving it to /var/tmp/atd. It then uses this binary to upload stealer execution results to the attackers’ infrastructure.
We did not observe any other activity performed via the reverse shell, and thus the whole infection chain can be described with the graph below:
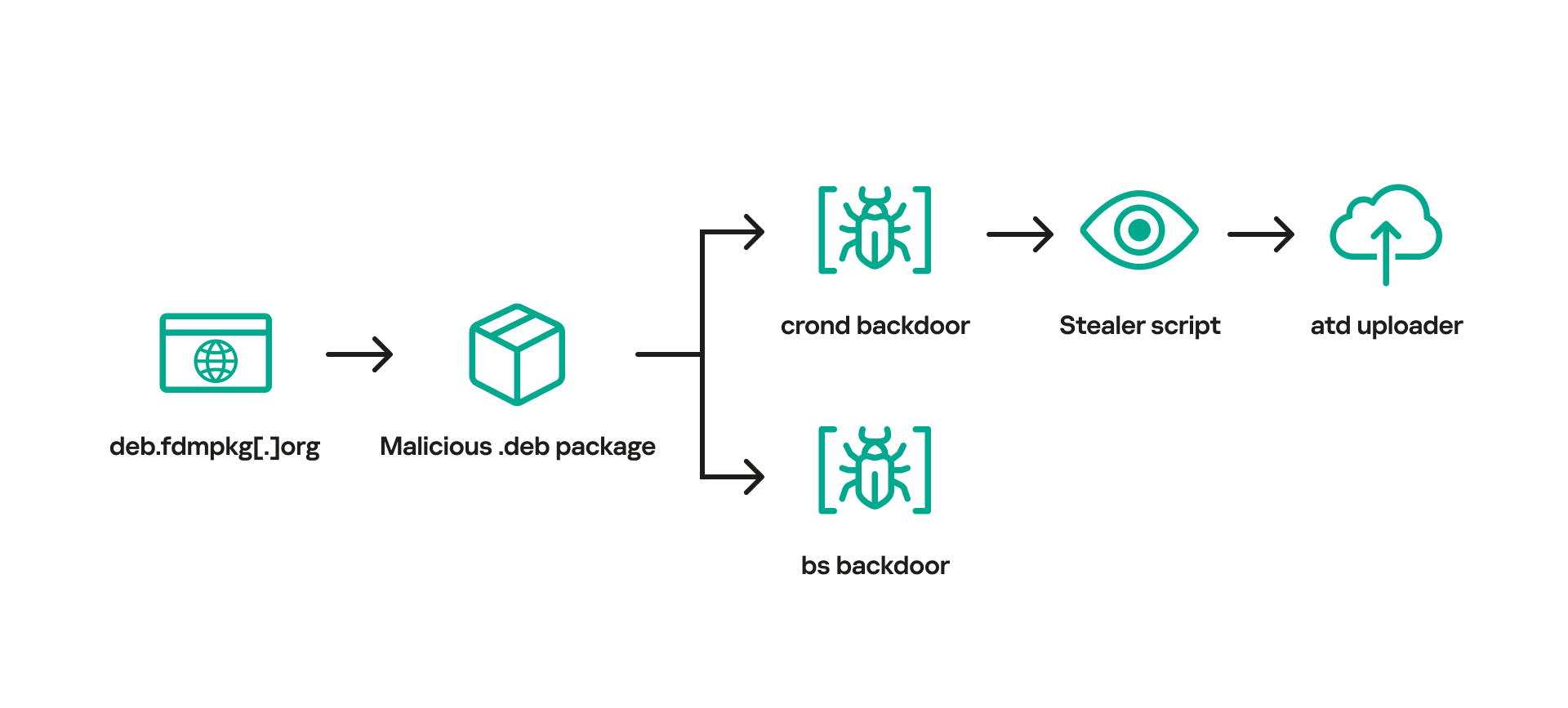
Mystery of the infection vector
After analyzing all components in the chain, we wanted to find out how the infected Debian package was distributed to victims. We checked the official website of Free Download Manager (freedownloadmanager[.]org). Packages available for download from this website turned out to be hosted on the files2.freedownloadmanager[.]org domain, and they were not backdoored.
We then decided to conduct an open-source check on the fdmpkg[.]org domain. This check revealed a dozen posts on websites such as StackOverflow and Reddit, where users have been discussing problems caused by the infected Free Download Manager distribution, not realizing they actually became victims of malware. These posts were made over the course of three years – from 2020 to 2022.
In one such post on Unix Stack Exchange, the author complains about the message ‘Waiting for process: crond’ that prevents the computer from shutting down:

The responses to this post, which came from users dealing with the same problem, suggest that this issue is caused by the Free Download Manager software. They advise to remove the files /etc/cron.d/collect, /var/tmp/crond and /var/tmp/bs. However, none mention that these three files are malicious.

In another post created in 2020, a Reddit user asked whether it is OK to install Free Download Manager without running the postinst script, which, unbeknownst to the user, contained malware.
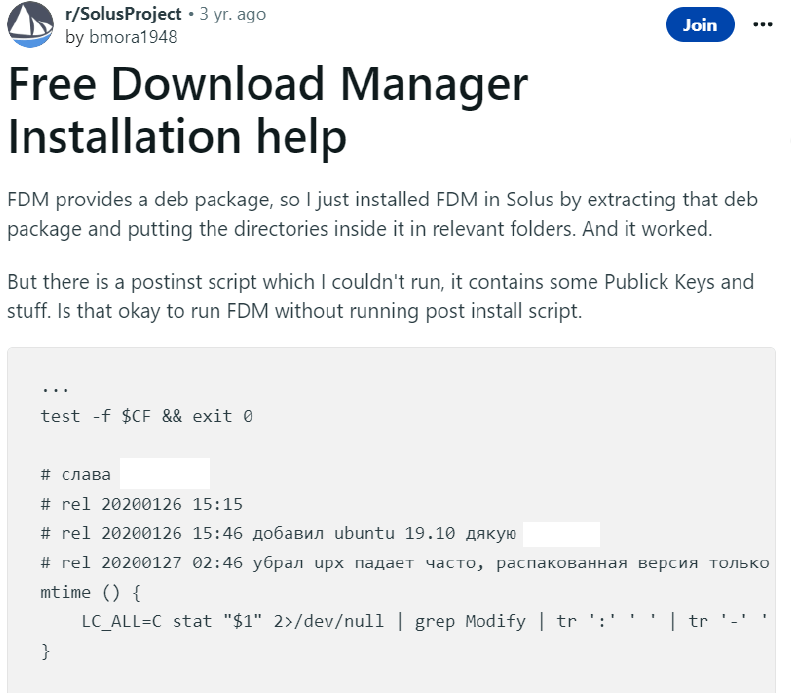
Moreover, the post author pasted the contents of the script, and another Reddit user pointed out in the comments that it may be malicious. However, these users did not identify the website distributing the infected package or find out what this script does.
We additionally found a post on Reddit mentioning that the official website of this software was distributing malware in 2015. However, the malware described in this post turned out to be unrelated to the campaign that we discovered.

All these posts on social networks made us think that the malicious Debian package could have been distributed via a supply chain attack, through the freedownloadmanager[.]org website. So, we decided to look for further facts that could prove or disprove this claim.
An unexpected redirection
While checking videos on Free Download Manager that are hosted on YouTube, we identified several tutorials demonstrating how to install this software on Linux machines. We observed the following actions that happen in all these videos:
- The video makers opened the legitimate website of Free Download Manager (freedownloadmanager[.]org) in the browser;
- They afterwards clicked on the Download button for the Linux version of the software;
- They were redirected to the malicious https://deb.fdmpkg[.]org/freedownloadmanager.deb URL that hosts the infected version of Free Download Manager.

We also noted that the redirection to the malicious deb.fdmpkg[.]org domain was not occuring in all cases. In another video posted within the same timeframe, , a user clicked on the ‘Download’ button hosted on the software website and ended up downloading Free Download Manager from the legitimate website.
Thus, it is possible that the malware developers scripted the malicious redirection to appear with some degree of probability or based on digital fingerprint of the potential victim.
We further inspected the legitimate Free Download Manager website, wanting to find out if the software developers were aware their website was potentially compromised. In one of the comments made on the software’s blog in 2021, a user complains about observing access to the 5d6167ef729c91662badef0950f795bf362cbb99.u.fdmpkg[.]org domain. A reply to this comment from the user ‘blogadmin’ says that Free Download Manager is not related to this domain and advises to make use only of official versions of the software:

However, nobody bothered to discover how this user ended up installing this suspicious version of Free Download Manager. As such, the official website of this software continued distributing the malicious Debian package until at least 2022.
Origins of the backdoor
Having established how the infected Free Download Manager package was distributed, we decided to check whether the implants discovered over the course of our research have code overlaps with other malware samples. It turned out that the crond backdoor represents a modified version of a backdoor called Bew. Kaspersky security solutions for Linux have been detecting its variants since 2013.

Code of the 2013 version of Bew (left, MD5: 96d8d47a579717223786498113fbb913) and the crond backdoor (right, MD5: 6ced2df96e1ef6b35f25ea0f208e5440)
The Bew backdoor has been analyzed multiple times, and one of its first descriptions was published in 2014. Additionally, in 2017, CERN posted information about the BusyWinman campaign that involved usage of Bew. According to CERN, Bew infections were carried out through drive-by downloads.
As for the stealer, its early version was described by Yoroi in 2019. It was used after exploitation of a vulnerability in the Exim mail server.

The Bash stealer described in 2019 (left, MD5: 8C7EFB0493B6FB805B2C2F0593DE0AB1) and the stealer used in the FDM campaign in 2022 (right, MD5: AD7F99D44931489B2C38DF7A5A166C4D)
Why wasn’t the malicious package discovered earlier?
The malware observed in this campaign has been known since 2013. In addition, the implants turned out to be quite noisy, as demonstrated by multiple posts on social networks. According to our telemetry, victims of this campaign are located all over the world, including Brazil, China, Saudi Arabia and Russia. Given these facts, it may seem paradoxical that the malicious Free Download Manager package remained undetected for more than three years.
We assess that this is due to the following factors:
- As opposed to Windows, Linux malware is much more rarely observed;
- Infections with the malicious Debian package occurred with a degree of probability: some users received the infected package, while others ended up downloading the benign one;
- Social network users discussing Free Download Manager issues did not suspect that they were caused by malware.
While the campaign is currently inactive, this case of Free Download Manager demonstrates that it can be quite difficult to detect ongoing cyberattacks on Linux machines with the naked eye. Thus, it is essential that Linux machines, both desktop and server, are equipped with reliable and efficient security solutions.
We additionally contacted the developers of Free Download Manager and notified them about this campaign. At the time of publishing this article, we had not received a response from them.
Indicators of Compromise
File checksums
b77f63f14d0b2bde3f4f62f4323aad87194da11d71c117a487e18ff3f2cd468d (Malicious Debian Package)
2214c7a0256f07ce7b7aab8f61ef9cbaff10a456c8b9f2a97d8f713abd660349 (crond backdoor)
93358bfb6ee0caced889e94cd82f6f417965087203ca9a5fce8dc7f6e1b8a3ea (bs backdoor)
d73be6e13732d365412d71791e5eb1096c7bb13d6f7fd533d8c04392ca0b69b5 (atd uploader)
File paths
/etc/cron.d/collect
/var/tmp/crond
/var/tmp/bs
/var/tmp/atd
Network indicators
fdmpkg[.]org
172.111.48[.]101
Source:: Securelist
