
Phishers want their fake pages to cost minimum effort but generate as much income as possible, so they eagerly use various tools and techniques to evade detection, and save time and money. Examples include automation with phishing kits or Telegram bots. Another tactic, popular with scammers big and small, phishers included, is hacking websites and placing malicious content on those, rather than registering new domains. Besides tucking a phishing page inside the website they hack, scammers can steal all of the data on the server and completely disrupt the site’s operation.
What sites get hacked the most
Abandoned websites end up captured by cybercriminals fairly often. A lack of maintenance and security patches means they are easy to compromise using a known exploit. Besides, on a long-neglected site, phishing pages can stay up for long periods of time, as no one monitors what gets published, which is exactly what scammers look for.
This does not mean malicious actors do not attack actively maintained sites, though. Smaller websites attracting little traffic are among those exposed to the hacking threat. Their owners may not be able to afford to spend enough money on information security or hiring a security professional, they may be unfamiliar with security settings, or they may be confident that their website is too small to be of any interest to hackers. However, to a phisher, the possibility of hacking the website is more important than its popularity, as links to scam pages are likely to be emailed or sent via instant messaging platforms. Therefore, even smaller websites are an attractive target for scammers.
According to W3Techs, 43.1% of all websites on the internet are powered by the WordPress content management system. There is a huge number of third-party plugins designed for extending the functionality of this popular platform. New vulnerabilities exploited by hackers are discovered both in plugins and in WordPress itself on a regular basis. The rest of this article will deal with phishing pages on hacked websites that are powered by WordPress.
Hacking WordPress websites
Most of the time, phishers who hack WordPress websites do so by exploiting security holes. After a successful exploitation attempt, hackers upload a WSO web shell and use that to gain access to the website control panel, circumventing the authentication step. This opens the control panel to all comers, allowing for any changes anyone may wish to make. In May 2023, our systems discovered over 350 unique domains with open access to the control panel. That said, the real number of these websites could be much higher, as a compromised control panel may not be publicly accessible all the time.
Control panel of a hacked website
Alternatively, malicious actors may hijack the website administrator’s account by brute-forcing a weak password or using leaked credentials. In that case, they do not need any extra software to access the control panel. All they have to do is log into the compromised account and start putting up fake pages.
Sometimes, hackers leave the site’s main functionality in place as they publish phishing pages. A visitor would never guess the site has been hacked: every section is where it is supposed to be, and only relevant information can be seen. Scammers hide their malicious content inside new directories that cannot be accessed from the main website menu.

Home page of a hacked website
However, most hacked websites have broken links to other sections on the home page, as hackers delete the original directories, replacing these with phishing content.

Phishing page on a hacked website
Data, such as credentials for a website, bank card details including the CVV or other personal information depending on the type of scam, will be stored in the control panel if entered by a visitor on the fake page. If the website also has a web shell installed and anyone can get access to the content, the victim’s data will be visible to anyone.
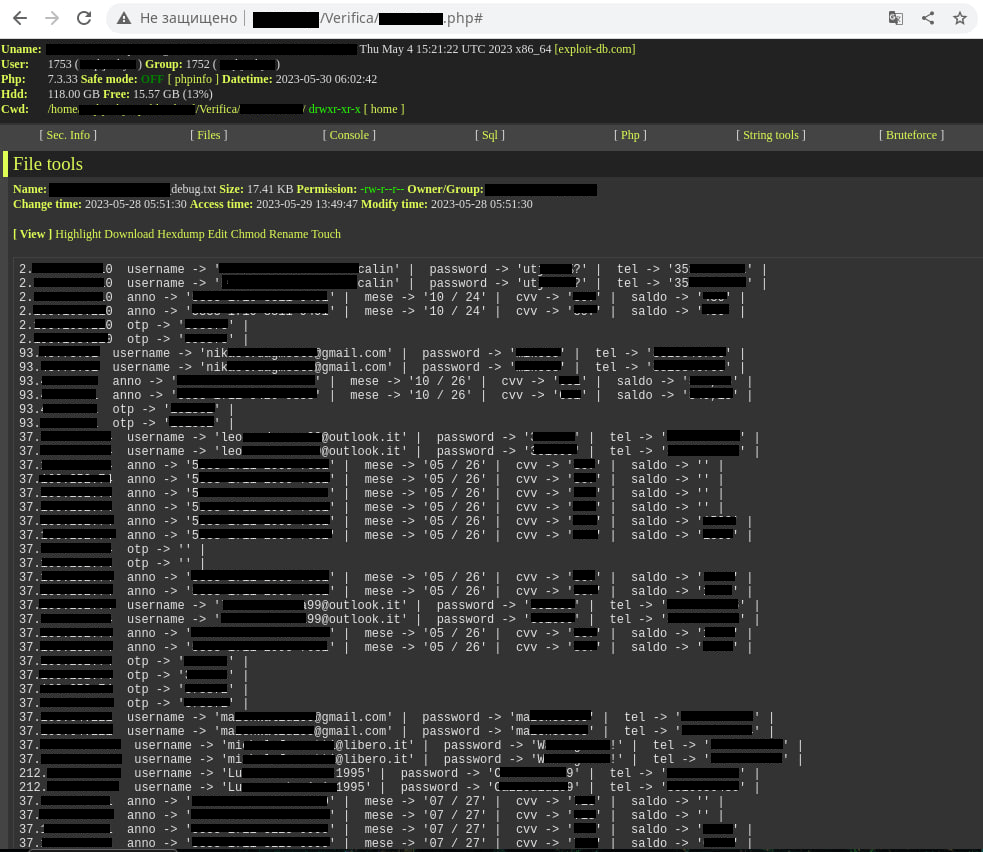
Page with stolen user data
Scammers may offer the stolen data for sale on the dark web or use it to siphon money out of the victim’s bank account. Furthermore, they may use the information they collect to make their future scams look more credible.
Signs of a hacked WordPress site
There are several fairly obvious signs that may suggest you are looking at a phishing page hosted on a compromised website.

Phishing page: the URL is showing /wp-content/ and the page is named login.php

Home page of the hacked Chinese site

Phishing page in French in a new directory on the same website

Phishing page placed inside the “Netflix” directory and imitating the Netflix login form
Statistics on hacked WordPress sites
We added the typical features of hacked websites to our web threat detection rules to enable our technology to recognize and block this type of phishing. This section contains statistics on websites detected with the help of that new functionality.
From May 15 through July 31, 2023, we discovered 22400 unique WordPress websites that had been hacked to create phishing pages. The figure includes both compromised sites with open access to the control panel at the time of detection and those whose control panels were not available to unauthenticated users.
Number of detected unique hacked WordPress sites, May 15 – July 31, 2023 (download)
During the same period of time, users made a total of 200 213 attempts at visiting fake pages hosted on compromised websites.
Numbers of attempts to visit phishing pages on hacked WordPress websites, May 15 – July 31, 2023 (download)
Services and organizations whose users are most frequently targeted by phishing pages on hacked websites include Netflix, European banks and popular delivery services.
Takeaways
Seasoned cybercriminals hack legitimate websites as a way of setting phishing traps. Both long-neglected and actively maintained websites may be targeted this way. In particular, hackers tend to compromise smaller websites whose owners cannot immediately recognize their presence.
Websites powered by WordPress often suffer from vulnerabilities that allow scammers to easily gain access to the control panel using a special script and publish malicious content. Alternatively, hackers can brute-force the administrator’s credentials or use a stolen password. Website admins should use strong, unique passwords and multi-factor authentication to protect their accounts from hijacking, update the server software on a regular basis, and deactivate plugins that are not in use.
Although hackers work hard to create credible imitations of popular websites whose users they are targeting, you can recognize the signs of phishing on a hacked website. In particular, watch for the following:
- Default names of WordPress directories appearing in the URL
- Name of the imitated brand appearing in one of the directory names
- Page content unrelated to the rest of the website
Between mid-May and mid-June, our systems detected upward of seven thousand unique websites that had been hacked and used for phishing purposes.
Source:: Securelist