In 2022, Kaspersky security solutions detected 1,661,743 malware or unwanted software installers, targeting mobile users. Although the most common way of distributing such installers is through third-party websites and dubious app stores, their authors every now and then manage to upload them to official stores, such as Google Play. These are usually policed vigorously, and apps are pre-moderated before being published; however, the authors of malicious and unwanted software employ a variety of tricks to bypass platform checks. For instance, they may upload a benign application, then update it with malicious or dubious code infecting both new users and those who have already installed the app. Malicious apps get removed from Google Play as soon as they are found, but sometimes after having been downloaded a number of times.
With many examples of malicious and unwanted apps on Google Play being discovered after complaints from users, we decided to take a look at what the supply and demand of such malware on the dark web looks like. It is especially important to analyze how this threat originates, because many cybercriminals work in teams, buying and selling Google Play accounts, malware, advertising services, and more. It’s a whole underground world with its own rules, market prices, and reputational institutions, an overview of which we present in this report.
Methodology
Using Kaspersky Digital Footprint Intelligence, we were able to collect examples of offers of Google Play threats for sale. Kaspersky Digital Footprint Intelligence allows discreet monitoring of pastebin sites and restricted underground online forums to discover compromised accounts and information leakages. The offers presented in this report were published between 2019 and 2023 and were collected from the nine most popular forums for the purchase and sale of goods and services related to malware and unwanted software.
Key findings
- The price of a loader able to deliver a malicious or unwanted app to Google Play ranges between $2,000 and $20,000.
- To keep their activities low-profile, a large percentage of attackers negotiate strictly through personal messages on forums and messengers, for example, in Telegram.
- The most popular application categories to hide malware and unwanted software include cryptocurrency trackers, financial apps, QR-code scanners and even dating apps.
- Cybercriminals accept three main kinds of payment: a percentage of the final profit, subscription or rent, and one-time payment.
- Cybercriminals offer to launch Google ads to attract more people to download malicious and unwanted apps. The cost of ads depends on the target country. Ads for users from the USA and Australia cost the most — up to about $1 (US).
Types of malicious services offered on the dark web
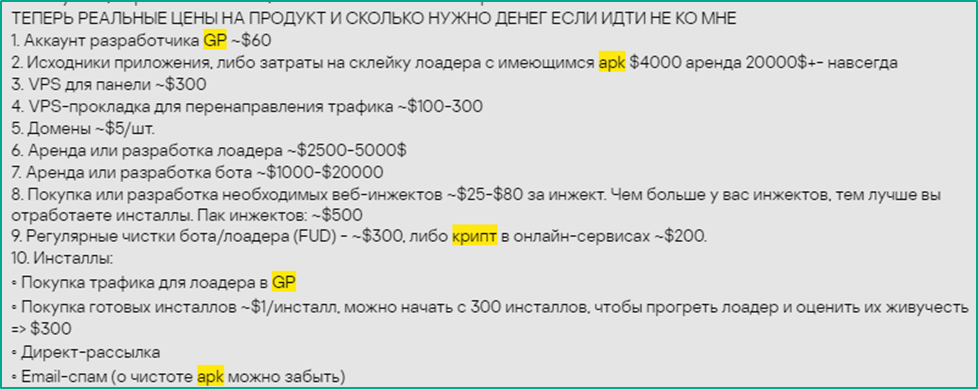
As on legitimate online marketplaces, there are also various offers on the dark web for customers with different needs and budgets. In the screenshot below, you can see an offer list, which gives an overview of the number of different goods and services that may be needed to target Google Play users. The author of the list calls the prices too high; however, they do not contradict the prices we’ve seen in other dark web offers. The main products that attackers buy are developers’ Google Play accounts that can be either hacked or registered by cybercriminals using stolen identities, as well as source code of various tools that help the buyer to upload their creations to Google Play. Also, such services as VPS (for $300), or Virtual Private Server, which the attackers use to control infected phones or to redirect user traffic, as well as web-based injections are offered. A web injection is malicious functionality that monitors the victim’s activity, and if they open a web page that is of interest to the cybercriminals, an injector replaces it with a malicious one. Such a feature is offered for $25–80 apiece.
A dark web service provider calls these prices too high, and indicates that they sell the same services cheaper
See translation
Here are the real product prices and how much money you need if you don’t choose me
- Traffic purchase for the GP loader
- Installations purchase ~$1/installation; you can start with 300 installations to warm up the loader and assess their persistence => $300
- Direct messaging
- Email spam (forget about APK being undetectable)
Let’s take a look at some specific programs and services that cybercriminals offer for sale.
Google Play loaders
In most of the offers we analyzed, attackers sell Google Play loaders, programs whose purpose is to inject malicious or unwanted code into a Google Play app. This app is then updated on Google Play, and the victim may download the malicious update onto their phone. Depending on what exactly was injected into the app, the user may obtain the final payload with the update or get a notification prompting them to enable installation of unknown apps and install it from an external source. In the latter case, until the user agrees to install the additional app, the notification does not disappear. After installing the app, the user is asked for permissions to access key data from the phone, such as Accessibility Services, camera, microphone, etc. The victim may not be able to use the original legitimate app until they give the permissions required to perform malicious activities. Once all the requested permissions are granted, the user is finally able to use the app’s legitimate features, but at the same moment their devices become infected.
To convince the buyer to purchase their loaders, cybercriminals sometimes offer to provide a video demonstration, as well as to send a demo version to the potential client. Among the loader features, their authors may highlight the user-friendly UI design, convenient control panel, victim country filter, support for the latest Android versions, and more. Cybercriminals may also supplement the trojanized app with functionality for detecting a debugger or sandbox environment. If a suspicious environment is detected, the loader may stop its operations, or notify the cybercriminal that it has likely been discovered by security investigators.
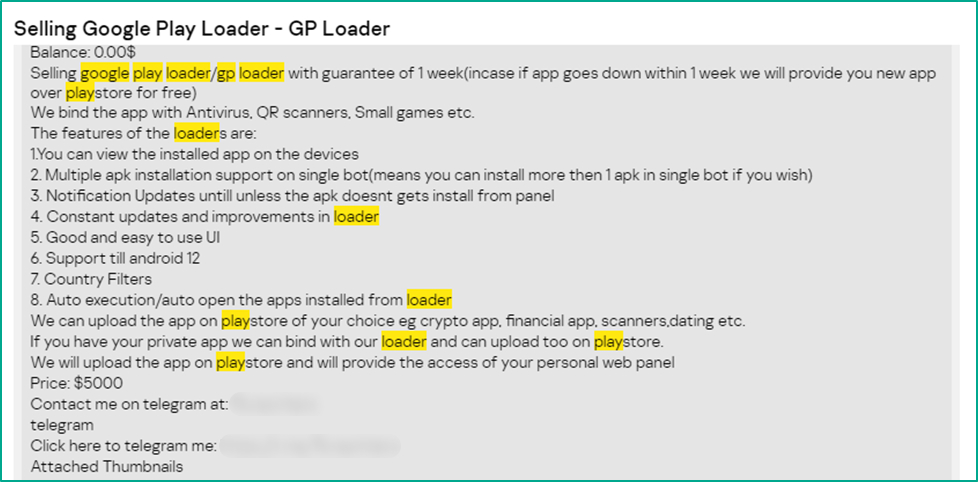
Google Play loaders are the most popular offer on the dark web among Google Play threats
Often loader authors specify the types of legitimate apps their loaders work with. Malware and unwanted software is frequently injected into cryptocurrency trackers, financial apps, QR-code scanners and even dating apps. Cybercriminals also highlight how many downloads the legitimate version of the target app has, which means how many potential victims can be infected by updating the app with malicious or unwanted code. Most frequently, sellers promise to inject code into an app with 5,000 downloads or more.
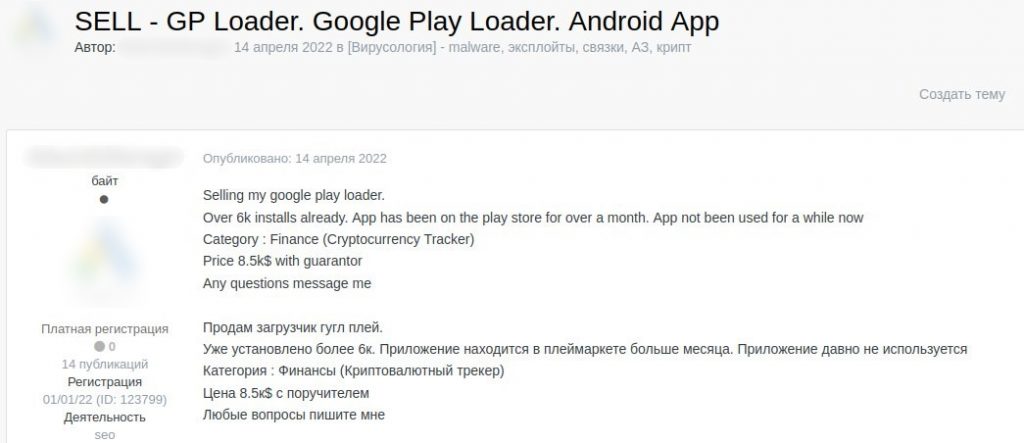
Cybercriminals sell a Google Play loader injecting code into a cryptocurrency tracker
Binding service
Another frequent offer on the dark web is binding services. In essence, these do exactly the same thing that Google Play loaders do — hide a malicious or unwanted APK file in a legitimate application. However, unlike a loader, which adapts the injected code to pass the security checks on Google Play, a binding service inserts malicious code into an app that is not necessarily suitable for the official Android marketplace. Often, malicious and unwanted apps created with a binding service are distributed through phishing texts, dubious websites with cracked games and software, and more.
As binding services have a lower successful installation rate than loaders, the two differ greatly in price: a loader can cost about $5,000, while a binding service usually costs about $50–$100 or $65 per file.
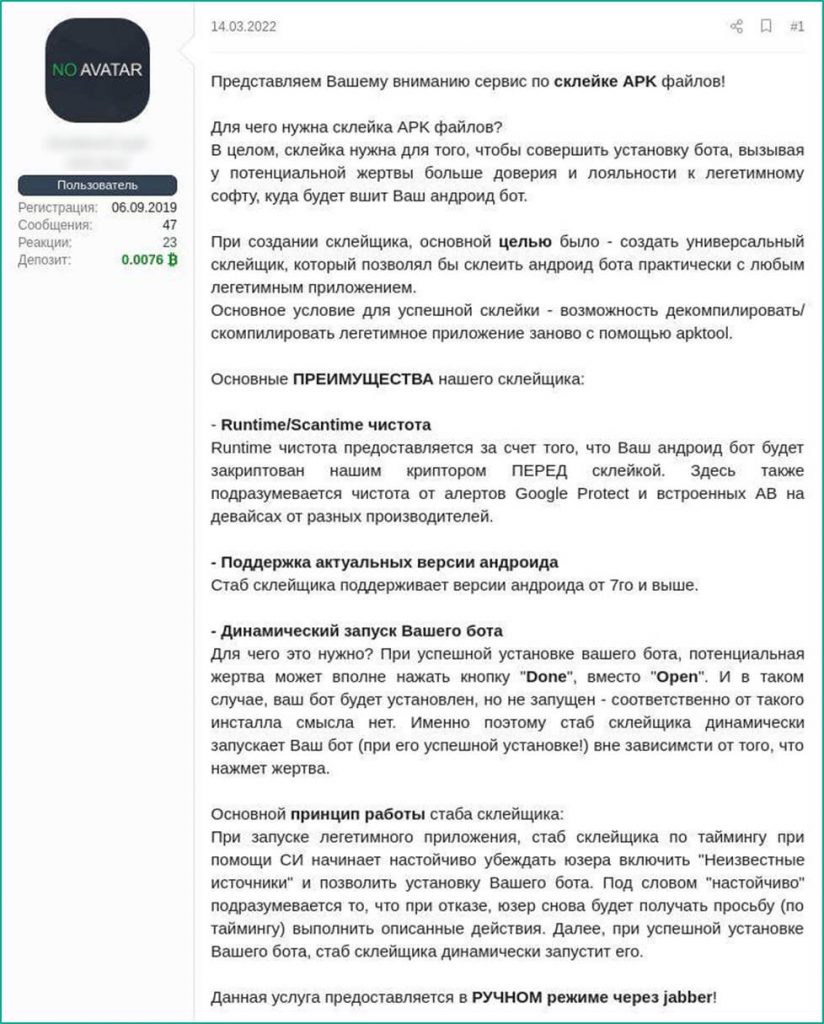
Seller’s description of a binding service
See translation
We present for your consideration an APK binding service.
What is APK binding for? In a nutshell, binding allows attackers to install a bot to gain more trust from the victim, who is loyal to the legitimate app that the Android bot is bound to.
In creating this binding service, our main goal was to create a universal binder that would allow binding an Android bot to any legitimate application.
The main condition for enabling binding is the possibility to decompile a legitimate app and then compile it back using apktool.
Our binder’s main ADVANTAGES:
Runtime/scantime FUD
Runtime cleanness is achieved by encrypting the Android bot with our cryptor BEFORE binding. It is also clear of alerts from Google Protect and built-in antivirus on devices from different vendors.
Most recent Android version support
The binder is compatible with Android 7 and higher
Dynamic bot launch
What is it for? After a successful installation, the victim may tap Done instead of Open, and such installation is of no use. The binder dynamically launches the bot, no matter what the victim taps.
The binder’s main operating principle is that when the legitimate application is launched, it prompts the user to allow installation from unknown sources on a timer using social engineering, so that the bot can be installed. If the user rejects this, they receive another request after some time. Upon successful installation, the binder dynamically launches the bot.
This service is provided manually via jabber.
The advantages and features of binding services listed in sellers’ ads are often similar to those of loaders. Binders usually lack Google Play-related features, though.
Malware obfuscation
The purpose of malware obfuscation is to bypass security systems by complicating malicious code. In this case, the buyer pays either for processing a single application, or for a subscription, for example, once per month. The service provider may even offer discounts for the purchase of packages. For example, one of the sellers offers obfuscation of 50 files for $440, while the cost of processing only one file by the same provider is about $30.
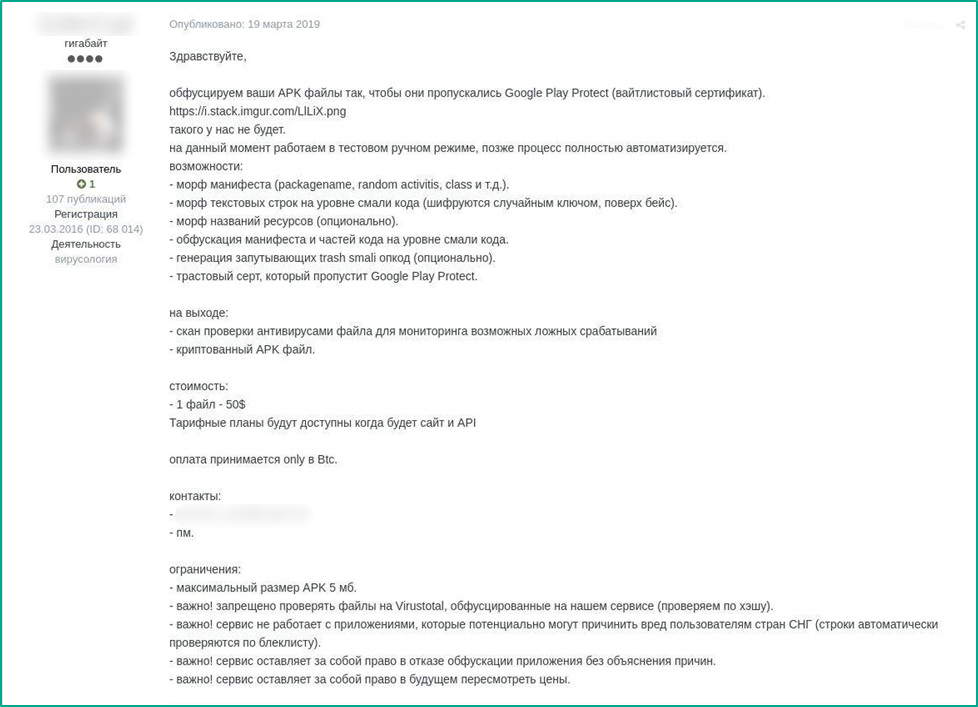
Google Play threat obfuscation offer for $50 apiece
See translation
Hi everyone,
We obfuscate your APK files, so Google Play Protect lets them pass (allowlist certificate).
[IMG link]
This is not our case.
We are now working in manual test mode, later the process will be fully automated.
We offer:
- manifest morph (packagename, random activitis, class, etc)
- text string morph on the Smali code level (encryption with random key with Base encoding)
- resource name morph (optional)
- manifest and code part obfuscation on the Smali code level
- complicated trash Smali opcode generation (optional)
- trusted certificate accepted by Google Play Protect
Output:
- antivirus check scan to monitor possible false positives
- encrypted APK
Price:
1 file – $50
Service plans will be available when the site and API are ready
Payment accepted in BTC only
Contacts:
- PM
Restrictions:
- APK max size – 5MB
- Important! Uploading files obfuscated by our service to VirusTotal is prohibited (checking via hash).
- Important! The service doesn’t support apps that can damage CIS users (strings are automatically checked against a denylist)
- Important! The service has the right to refuse app obfuscation without any explanation
- Important! The service has the right to review the prices in the future
Installations
To increase the number of downloads of a malicious app, many attackers offer to purchase installations by increasing app traffic through Google ads. Unlike other dark web offers, this service is completely legitimate and is used to attract as many downloads of the application as possible, no matter if it is a still-legitimate application or an already poisoned one. Installation costs depend on the targeted country. The average price is $0.5, with offers ranging from $0.1 to $1. In the screenshot below, ads for users from the USA and Australia cost the most — $0.8.
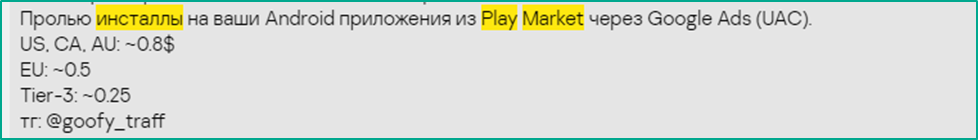
Seller specifies the installation price for each country
See translation
Increase installations of your Android app from Play Market through Google Ads (UAC).
Other services
Dark web sellers also offer to publish the malicious or unwanted app for the buyer. In this case, the buyer does not interact directly with Google Play, but can remotely receive the fruits of the app’s activity, for example, all victim data stolen by it.
Average prices and common rules of sale
Kaspersky experts analyzed the prices in dark web ads offering Google Play-related services, and found that fraudsters accept different payment methods. The services can be provided for a share of the final profit, rented, or sold for a one-time price. Some sellers also hold auctions of their goods: since the number of items sold is limited, they are not very likely to be discovered, so buyers may be willing to compete for them. For example, in one of the auctions we found, the bidding for a Google Play loader started at $1,500, the bid increment (step) was equal to $200, and the “blitz” — the instant purchase price — was $7,000.
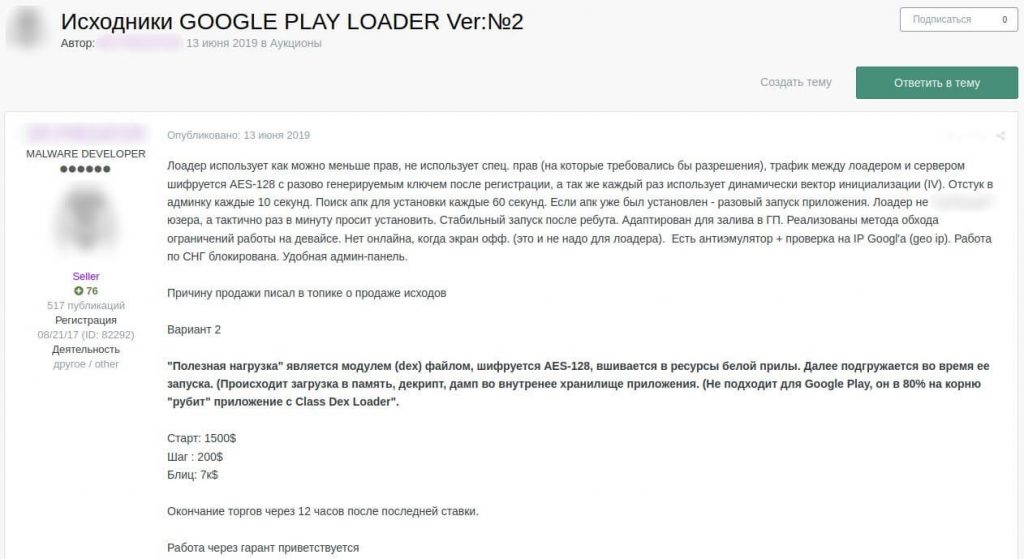
Cybercriminals auction a Google Play loader
See translation
Google Play Loader source, ver №2
The loader uses minimum rights, doesn’t require special rights that need permission to be granted, the traffic between the loader and the server is AES-128 encrypted with an encryption key generated once after registration, and a dynamically used initialization vector (IV). Contacts admin panel every 10 seconds. Searches for APK to install every 60 seconds. If an APK is already installed, the loader starts it one time. The loader doesn’t bother users, but subtly asks to install the app. Stable launch after reboot. Adapted for uploading to Google Play. Evasion methods for functionality restrictions on the device are implemented. Offline when the screen is off (loader doesn’t need to stay online). Anti-emulator and Google geo IP check. Blocked in CIS. Convenient admin panel.
The reason for selling I mentioned in the source sale topic.
Variant 2
The payload is a module (dex) file, AES-128 encrypted, injected into the legit app resources. It is loaded when the app is launched (loading into memory, decryption and dumping into the app’s internal storage). Not for Google Play, blocks 80% of apps with Class Dex Loader.
Start: $1,500
Step: $200
Blitz: $7k
The bidding ends in 12 hours after the last bid.
You are welcome to use an escrow service
The offered blitz price is not the highest. Prices for loaders we observed on dark web forums range between $2,000 and $20,000, depending on the malware complexity, novelty and prevalence, as well as the additional functions. The average price for a loader is $6,975.
Example of average offer for a Google Play loader
However, if cybercriminals want to buy the loader source code, the price immediately rockets, reaching the upper limit of the price range.
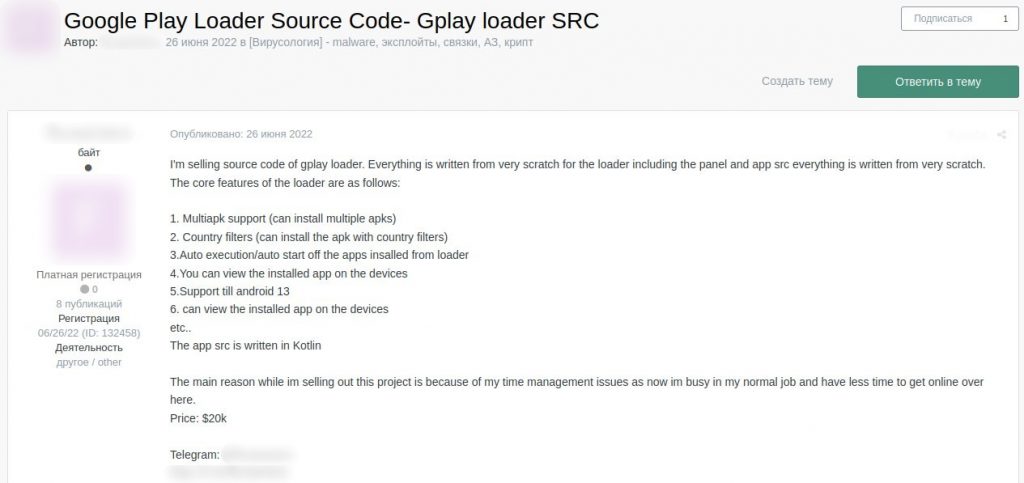
Seller offers a Google Play loader source code for $20,000
As opposed to a loader, a Google Play developer account (either hacked or newly created by the cybercriminals) can be bought quite cheaply, for example, for $200, and sometimes even for as little as $60. The price depends on the account features, such as the number of already published apps, number of their downloads, etc.
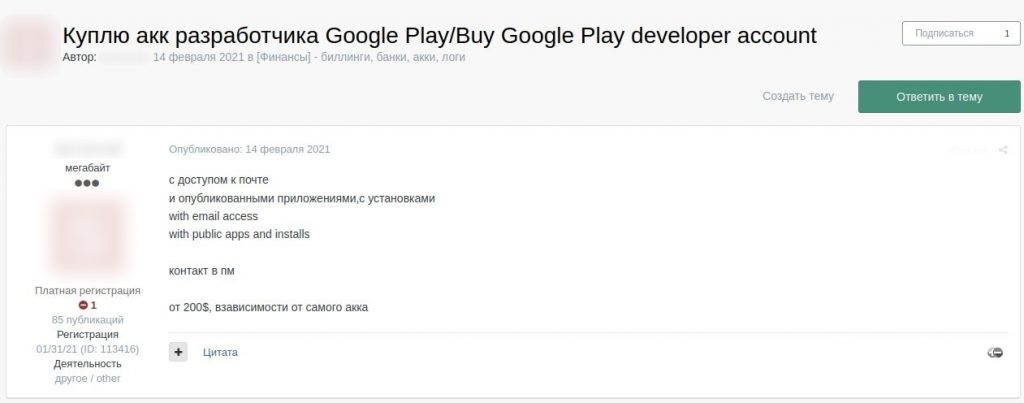
User wants to buy a Google Play account with access to the developer’s email
In addition to the many offers for sale, we also found numerous messages on the dark web about wanting to buy a particular product or service for a certain price.
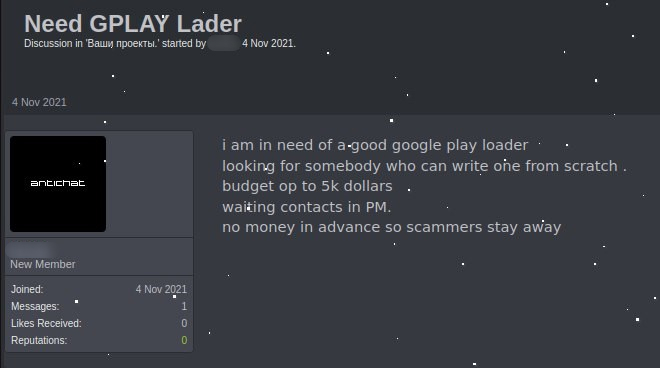
Cybercriminal looking for a new Google Play loader
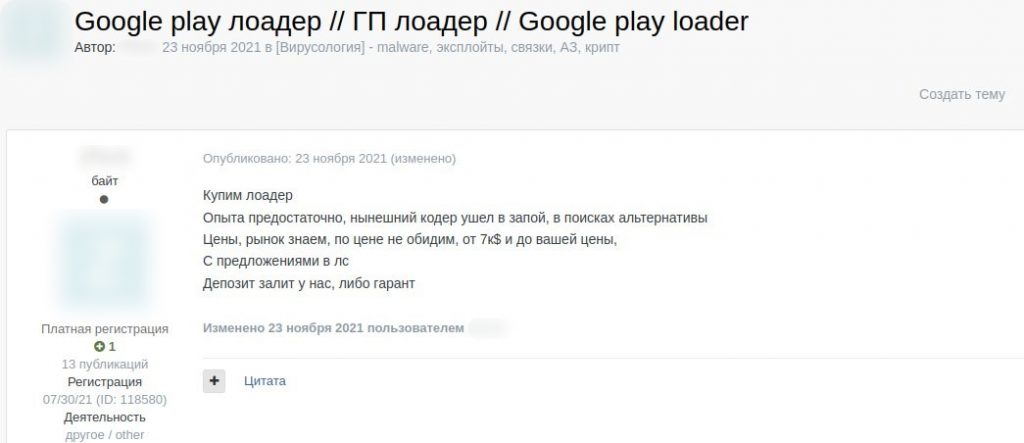
User wants to buy a new loader because their developer “went on a binge”
See translation
Need a loader
Enough experience, current coder went on a binge, and we’re in search of an alternative
We know prices and the market, won’t rob you, from $7k to your price
DM your offers
Deposit on our side or with an escrow service
How deals are made
Sellers on the dark web offer whole packages of different tools and services. To keep their activities low-profile, a large percentage of attackers negotiate strictly through private messages on dark web forums or personal messages on social networks and in messengers, for example in Telegram.
It may seem that service providers could easily deceive buyers, and make a profit from their apps themselves. Often this is the case. However, it is also common among dark web sellers to maintain their reputation, promise guarantees, or accept payment after the terms of the agreement have been fulfilled. To reduce risks when making deals, cybercriminals often resort to the services of disinterested intermediaries — escrow services or middlemen. An escrow may be a special service and supported by a shadow platform, or a third party disinterested in the results of the transaction. Note, however, that on the dark web nothing eliminates the risk of being scammed with 100% probability.
Conclusion and recommendations
We continuously monitor the mobile threat landscape to keep our users safe and informed of the most important developments. Not long ago, we published a report about the threats smartphone users faced in 2022. However, looking at the volume of supply and demand of such threats on the dark web, we can assume that the number of threats in the future will only grow — and become more complex and advanced.
To stay protected from mobile threats:
- Do not enable the installation of unknown apps. If some app urges you to do it, it is most likely infected. If it is possible, uninstall the app, and scan the device with an antivirus.
- Check the permissions of the apps that you use and think carefully before granting an app permissions it doesn’t need to perform its main functions, especially when it comes to high-risk permissions such as Accessibility Services. The only permission that a flashlight app needs is to use the flashlight.
- Use a reliable security solution that can help you to detect malicious apps and adware before they start misbehaving on your device.
- Update your operating system and important apps as soon as updates become available. To be sure that an app update is benign, enable automatic system scan in your security solution, or scan the device right after the updates are installed.
For organizations, it is necessary to protect their developer accounts with strong passwords and 2FA, as well as monitor the dark web to detect and mitigate credential leaks as early as possible.
To inquire about Kaspersky threat monitoring services for your organization, please contact us at dfi@kaspersky.com.
Source:: Securelist
